North Korea-Linked UNC1069 Targets Cryptocurrency Firms using AI and ML

North Korean threat actors tied to the cluster known as UNC1069 have been observed conducting highly tailored attacks against cryptocurrency companies and fintech organizations. The group uses artificial intelligence tools, deepfake lures, and multi-stage malware to steal credentials, browser data, and financial assets from victims.
According to researchers from Google’s Mandiant unit, the latest intrusion involved a complex social engineering campaign that began with a Telegram contact and ended with the deployment of seven distinct malware families designed to maintain access and extract valuable data.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
“The intrusion relied on a social engineering scheme involving a compromised Telegram account, a fake Zoom meeting, a ClickFix infection vector, and reported usage of AI-generated video to deceive the victim,” Google Mandiant researchers Ross Inman and Adrian Hernandez said.
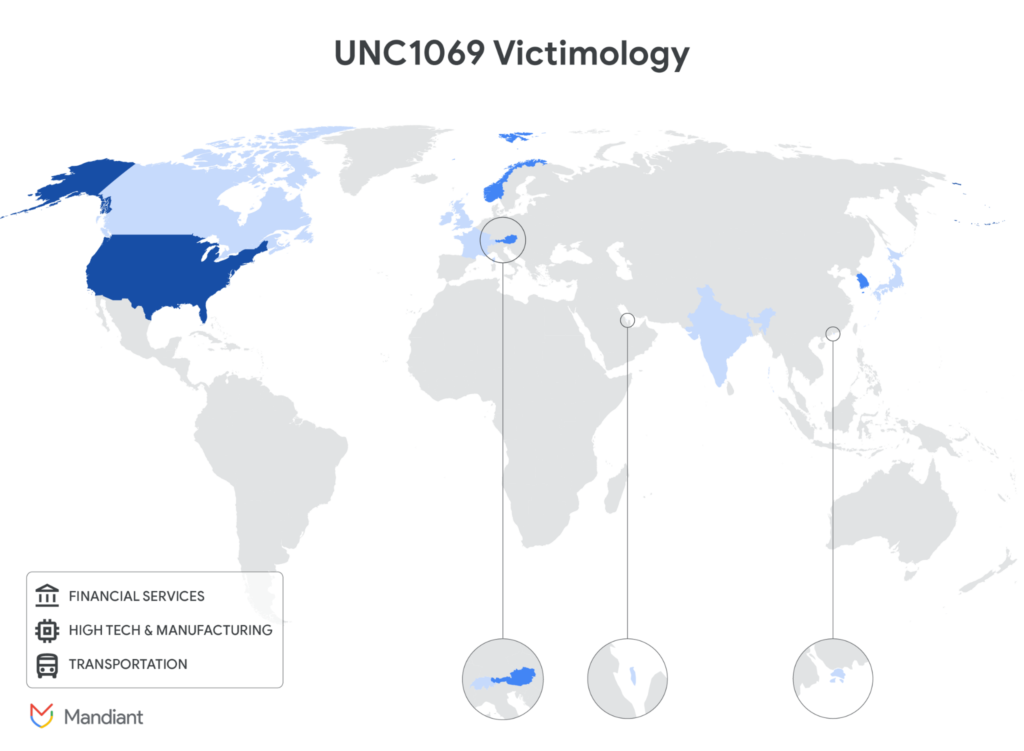
UNC1069 has been active since at least 2018 and historically carried out fraud related to financial gain under the aliases CryptoCore and MASAN. Experts say the group has now shifted its focus toward the Web3 and decentralized finance space, seeking high-value targets such as cryptocurrency startups, exchanges, venture capital firms, and developers involved in blockchain infrastructure.
How the Attack Chain Works
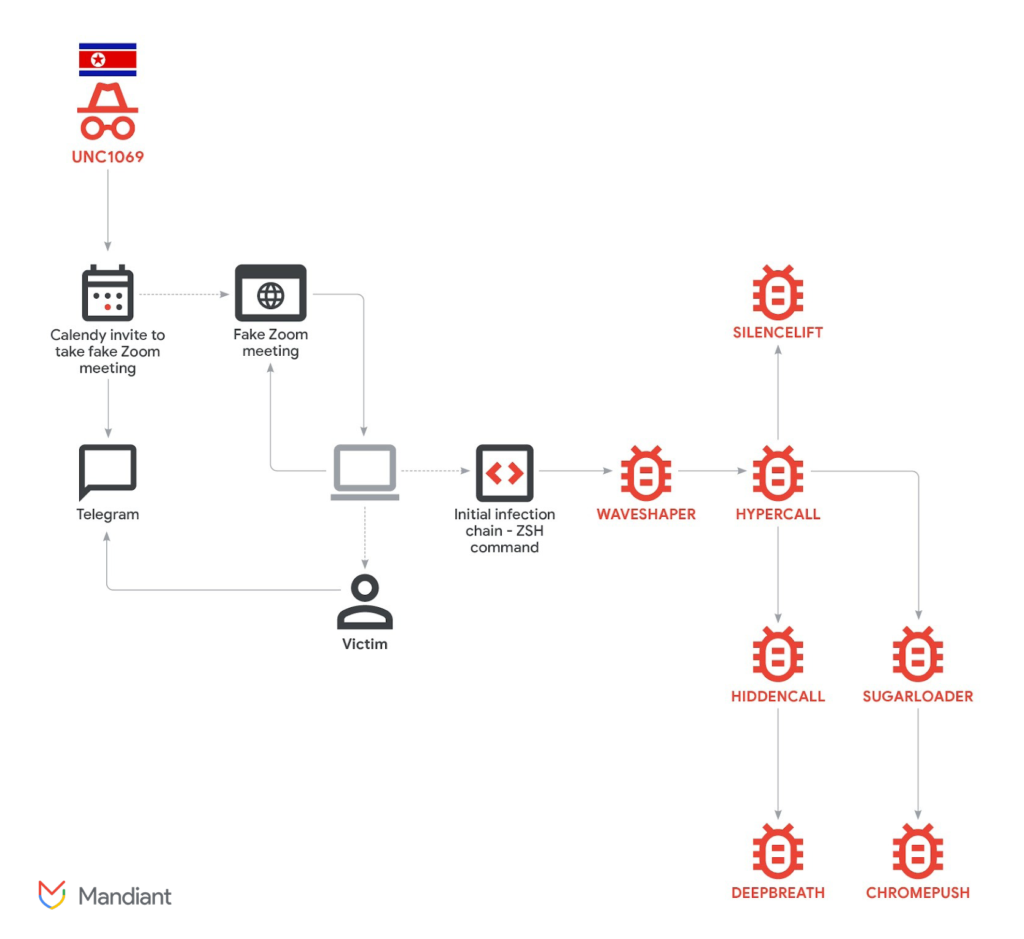
The UNC1069 attack chain documented by Mandiant is notable for its sophistication and use of deception at each stage:
Installation of Malware Families: The initial executable, known as WAVESHAPER, acted as a backdoor and facilitated deployment of additional tooling such as HYPERCALL, HIDDENCALL, DEEPBREATH, CHROMEPUSH, SUGARLOADER, and SILENCELIFT, each with specialized functions for data theft or remote control.
Initial Contact via Telegram: The attackers contacted a target using a compromised or fake Telegram account purporting to belong to a crypto executive.
Calendly Invite to Fake Zoom Meeting: Once rapport was built, the threat actor sent a Calendly link scheduling a “30-minute meeting.” This link redirected to a URL mimicking the Zoom interface hosted on the attacker’s infrastructure.
Deepfake Video Presentation: During the fake meeting, the victim was shown a video of what appeared to be a known CEO. Mandiant notes that while forensic evidence was not conclusive, it resembled previously reported deepfake videos used in such campaigns.
ClickFix Infection Vector: After the fake call, the victim received a bogus audio issue message and was prompted to run “troubleshooting” commands. One of these commands triggered the malware infection.
Notable Malware Tools Used
| Malware Family | Function |
|---|---|
| WAVESHAPER | Initial C++ backdoor used to drop follow-on components |
| HYPERCALL | Go-based downloader that fetches additional payloads |
| HIDDENCALL | Backdoor providing remote interactive access |
| DEEPBREATH | Data miner targeting credentials and system data |
| CHROMEPUSH | Browser-focused stealer disguised as a Chrome extension |
| SUGARLOADER | Secondary C++ downloader used to install modules |
| SILENCELIFT | Lightweight C/C++ backdoor for basic host telemetry |
These tools collectively enable credential harvesting, browser session token theft, file access, and persistent remote control.
AI and Deepfake Integration
UNC1069’s evolving tactics have included the use of generative AI tools. The threat actor is reported to misuse models such as Gemini for crafting lures and enhancing social engineering, though direct forensic proof of AI-generated videos in this specific incident was not recovered. According to TheRecord
“While Mandiant was unable to recover forensic evidence to independently verify the use of AI models in this specific instance, the reported ruse is similar to a previously publicly reported incident with similar characteristics,” Mandiant explained.
Earlier threat intelligence research by Google’s Threat Intelligence Group documented similar adversarial misuse of AI tools such as Gemini by state-linked actors to enhance phishing and reconnaissance workflows.
Why This Threat Matters to Cryptocurrency Organizations
Attackers targeting Web3 ecosystems and digital asset firms pose unique risks compared with traditional cybercrime:
- High-value targets often hold large sums of cryptocurrency and sensitive wallet infrastructure.
- Blockchain and DeFi companies rely on trust and rapid collaboration, which deepfakes and social engineering directly undermine.
- Credentials and session tokens stolen from developer laptops and executive systems can provide direct access to exchange admin panels or wallet keys.
UNC1069’s focus on credential and browser data theft shows a shift from simple phishing toward targeted, multi-stage compromises designed to facilitate financial theft rather than mere intrusion.
Indicators of Compromise (IoCs)
Security teams should watch for:
- Spoofed Zoom domains such as
zoom.uswe05[.]usused in fake meetings. - Unexpected Calendly invites from unknown or unusual Telegram contacts.
- Troubleshooting scripts proposed during virtual meetings that run command lines on victim machines.
- Presence of malware binaries such as WAVESHAPER and HYPERCALL on endpoints.
- Browser extension anomalies that could indicate CHROMEPUSH installation.
Recommended Mitigation Steps
To defend against similar campaigns:
- Verify all video meeting URLs independently before joining.
- Do not execute troubleshooting commands from untrusted messages.
- Use multi-factor authentication and strong endpoint protection.
- Enable AI and deepfake detection tools where available.
- Train staff to recognize social engineering signs and suspicious invites.
FAQ: UNC1069 Cryptocurrency Attack
What is UNC1069’s main goal?
To steal cryptocurrency and financial data from firms in the Web3, fintech, and crypto sectors.
Where did this information come from?
Reported by Google Mandiant researchers in official threat posts and technical analysis.
How do attackers initiate contact?
Via compromised or impersonated Telegram accounts with fake meeting invites.
Are deepfakes actually used?
Victims reported deepfake-like video in meetings, but forensic proof remains unverified.
How many malware tools were deployed?
Seven distinct families were observed, each with specific purposes like credential theft and persistence.
How can organizations protect themselves?
By verifying meeting URLs, enforcing strong authentication, training staff, and monitoring for suspicious scripts.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages