Malicious Chrome Extensions Exposed: Stealing Business Data, 2FA Codes, and Browser History

Security researchers have uncovered multiple malicious Google Chrome extensions that are abusing browser permissions to steal sensitive data. These include extensions aimed at Meta Business Suite, AI tools, and extensions that quietly collect browsing history from millions of users.
One of the most concerning discoveries is an extension called CL Suite (ID: jkphinfhmfkckkcnifhjiplhfoiefffl). It was uploaded to the Chrome Web Store and marketed as a tool to help with Meta Business Suite tasks. In reality, it collects two-factor authentication (2FA) codes, business contacts, and analytics data and sends it to attacker-controlled servers. Security research indicates this extension has at least 33 users.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Other campaigns involving AI-branded extensions and history-stealing add-ons show the threat is broader than just one extension. Investigations reveal that over 287 extensions installed by approximately 37.4 million users collect browsing history and send it to data brokers.
CL Suite Steals Meta Business Codes and Manager Data
The CL Suite extension openly requests broad access to the domains meta.com and facebook.com. According to security researchers, its privacy policy falsely claims any collected data stays on the user’s browser. In practice, the extension sends sensitive information to a remote server at getauth[.]pro.
Security analysts documented several data types transmitted to attacker infrastructure:
- 2FA secrets and current time-based codes used for account login
- Business Manager contacts and metadata exported as CSV files
- Analytics and asset information from Meta Business Manager
The extension effectively operates as a data exfiltration tool while posing as a legitimate utility for business users.
Growing Threat of AI-Pretending Extensions
In separate research, security firm LayerX identified at least 32 Chrome extensions marketed as helpful AI assistants. These add-ons claim to provide functionality such as Gmail assistance, AI chat integration, or productivity features. In reality, they contact a remote domain and capture sensitive user data, including emails, API keys, and other browser information. Many of these extensions were still available in the Chrome Web Store at the time of reporting.
Examples include:
- AI Assistant (nlhpidbjmmffhoogcennoiopekbiglbp) with tens of thousands of users
- AI Sidebar (gghdfkafnhfpaooiolhcnnegcdhkh) reposted after earlier versions were removed
Multiple extension IDs from these campaigns continue to circulate.
This reflects a broader trend of threat actors using popular AI branding to lure users into installing malicious code.
Massive Browser History Exfiltration Campaign
A comprehensive study by security researchers identified 287 Chrome extensions that silently collect and transmit browsing history. These extensions often disguise themselves as helpful tools but request unnecessary access to browsing data. Combined, they have been installed by approximately 37.4 million users worldwide.
Data collected in these campaigns may include:
- URLs visited by the user
- Browsing behavior and search patterns
- Correlated identifiers that could deanonymize browsing habits
Collected information is reportedly shared with multiple data service companies, drawing attention to how extension data practices intersect with broader online tracking ecosystems.
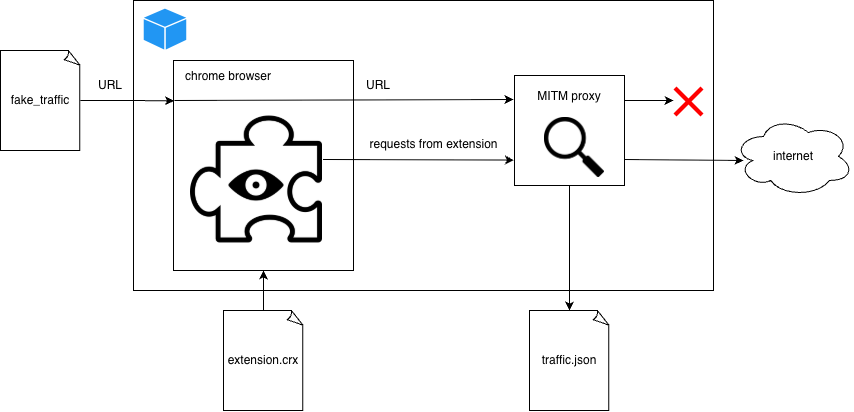
The names of the malicious extensions are as follows –
- AI Assistant (ID: nlhpidbjmmffhoogcennoiopekbiglbp)
- Llama (ID: gcfianbpjcfkafpiadmheejkokcmdkjl)
- Gemini AI Sidebar (ID: fppbiomdkfbhgjjdmojlogeceejinadg)
- AI Sidebar (ID: djhjckkfgancelbmgcamjimgphaphjdl)
- ChatGPT Sidebar (ID: llojfncgbabajmdglnkbhmiebiinohek)
- AI Sidebar (ID: gghdfkafnhfpaooiolhncejnlgglhkhe)
- Grok (ID: cgmmcoandmabammnhfnjcakdeejbfimn)
- Asking Chat Gpt (ID: phiphcloddhmndjbdedgfbglhpkjcffh)
- ChatGBT (ID: pgfibniplgcnccdnkhblpmmlfodijppg)
- Chat Bot GPT (ID: nkgbfengofophpmonladgaldioelckbe)
- Grok Chatbot (ID: gcdfailafdfjbailcdcbjmeginhncjkb)
- Chat With Gemini (ID: ebmmjmakencgmgoijdfnbailknaaiffh)
- XAI (ID: baonbjckakcpgliaafcodddkoednpjgf)
- Google Gemini (ID: fdlagfnfaheppaigholhoojabfaapnhb)
- Ask Gemini (ID: gnaekhndaddbimfllbgmecjijbbfpabc)
- AI Letter Generator (ID: hgnjolbjpjmhepcbjgeeallnamkjnfgi)
- AI Message Generator (ID: lodlcpnbppgipaimgbjgniokjcnpiiad)
- AI Translator (ID: cmpmhhjahlioglkleiofbjodhhiejhei)
- AI For Translation (ID: bilfflcophfehljhpnklmcelkoiffapb)
- AI Cover Letter Generator (ID: cicjlpmjmimeoempffghfglndokjihhn)
- AI Image Generator Chat GPT (ID: ckneindgfbjnbbiggcmnjeofelhflhaj)
- Ai Wallpaper Generator (ID: dbclhjpifdfkofnmjfpheiondafpkoed)
- Ai Picture Generator (ID: ecikmpoikkcelnakpgaeplcjoickgacj)
- DeepSeek Download (ID: kepibgehhljlecgaeihhnmibnmikbnga)
- AI Email Writer (ID: ckicoadchmmndbakbokhapncehanaeni)
- Email Generator AI (ID: fnjinbdmidgjkpmlihcginjipjaoapol)
- DeepSeek Chat (ID: gohgeedemmaohocbaccllpkabadoogpl)
- ChatGPT Picture Generator (ID: flnecpdpbhdblkpnegekobahlijbmfok)
- ChatGPT Translate (ID: acaeafediijmccnjlokgcdiojiljfpbe)
- AI GPT (ID: kblengdlefjpjkekanpoidgoghdngdgl)
- ChatGPT Translation (ID: idhknpoceajhnjokpnbicildeoligdgh)
- Chat GPT for Gmail (ID: fpmkabpaklbhbhegegapfkenkmpipick)
Why Browser Extensions Can Be Dangerous
Extensions run with powerful permissions in the browser. Once granted access, they can:
- Read and modify web page contents
- Access browser history and cookies
- Generate network requests to remote servers
- Execute scripts that harvest authentication tokens
Browser security research has shown extensions can bypass certain sandbox protections, making them useful tools for attackers to move laterally in a victim’s browser session.
Many extensions request dangerous or invasive permissions, such as full access to all visited websites, scripting privileges, or history access. A separate analysis found that most extensions ask for multiple high-risk permissions, increasing the potential for abuse.
How Attackers Distribute Malicious Extensions
Malicious extensions usually reach users in one of two ways:
- Direct upload to the Chrome Web Store with deceptive descriptions
- Re-publish after removal using similar names and icons to evade detection
Research has shown that attackers often update and refine malicious code over time, using version control and iterative commits, effectively treating malware as a maintained software project. This makes detection and takedown more challenging.
Risks and Potential Impact
| Risk Type | Description |
|---|---|
| Credentials & 2FA Capture | Extensions can harvest tokens used for logging into services such as Meta Business Manager. |
| Document & Analytics Exfiltration | Contact lists, asset configurations, billing info, and analytics can be extracted and stored remotely. |
| Browsing History Theft | Large-scale campaigns can reconstruct user behavior or link it to profiles. |
| Deceptive AI Tooling | Malicious AI add-ons use brand names to disguise extraction behaviors. |
Recommendations for Users and Organizations
- Monitor for suspicious network activity. Watch for unexpected connections to unknown domains.
- Review permissions before installing extensions. Only grant access that is necessary for the extension’s functionality.
- Remove unused or unnecessary extensions. Periodically audit your browser add-ons.
- Use separate profiles for sensitive work. Keep extensions off profiles used for banking or business tasks.
- Allowlist approved extensions only. Enterprise environments should control extension installation centrally.
FAQ
No. Even extensions in the official store can contain malicious code or collect more data than necessary. Users should evaluate permissions and reviews carefully.
Some can capture session cookies and tokens that may be used for account access, though the extensions mentioned focus mostly on 2FA codes and browsing data.
Removing a malicious extension stops its code from running, but users should also change passwords and tokens if sensitive data may have been exposed.
Implement extension allowlisting and restrict installation rights. Train users on extension risks and regularly audit browser profiles.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages