VoidLink: a modular, AI-assisted malware framework tied to UAT-9921 what defenders must know

Security teams are tracking a powerful new malware framework called VoidLink that targets Linux cloud environments and can give attackers long-term, stealthy control. Researchers say the framework is modular, cloud aware, and was likely developed with heavy help from large language models. Cisco Talos links the current deployment of VoidLink to a threat cluster tracked as UAT-9921.
This article explains how VoidLink works, who is being targeted, why it is hard to detect, and what defenders should do first. The opening paragraph answers the most important question: VoidLink is a fully operational, modular C2 framework designed for cloud and container environments that supports on-demand plugin compilation, multiple language runtimes, and role-based access controls.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
What is VoidLink in plain terms
VoidLink is a cloud-first malware platform. It installs small implants on breached Linux hosts, then pulls plugins and tools from a central command server as needed. The implants are written in Zig, plugins use C, and the backend uses Go. The framework can compile plugins on demand so attackers can tailor tools for specific targets and Linux distributions. Check Point describes VoidLink as an early example of malware substantially developed with AI assistance.
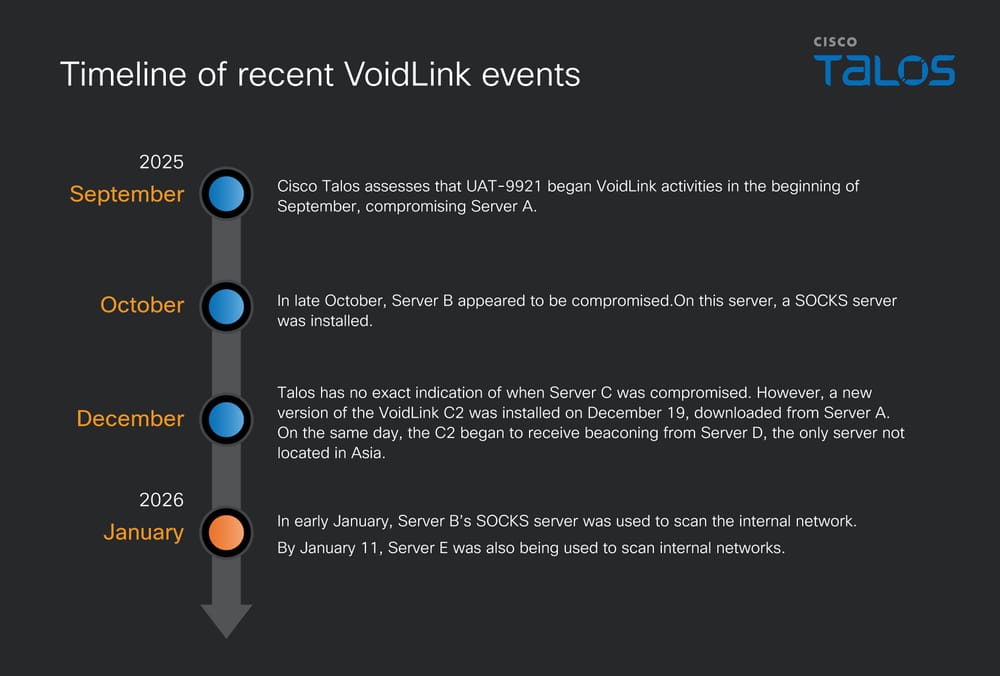
Cisco Talos connects recent VoidLink usage to a threat actor they name UAT-9921. Talos observed the actor deploy VoidLink implants, set up SOCKS proxies for internal scanning, and use the implants to collect credentials and move laterally inside cloud networks.
Why VoidLink is notable right now
- It is cloud aware and can detect if it runs on AWS, Azure, GCP, Alibaba, or Tencent clouds, and whether it is inside containers or Kubernetes.
- It supports compile-on-demand plugins so operators can generate tailored tools quickly for different targets and kernels.
- It includes strong stealth features, kernel-level tricks in some components, and active anti-analysis behaviors to avoid detection.
How an attack using VoidLink typically unfolds
- Initial access via credential theft, a vulnerable application, or a web shell. (Cloud posture and exposed interfaces are common vectors.)
- Implant drop and persistence. The attacker installs a lightweight Zig implant that survives reboots and hides inside the environment.
- On-demand plugin compilation. The C2 compiles plugins adapted for the host, then loads them into the implant to perform tasks such as credential harvesting, lateral movement, or kernel evasion.
- Lateral scanning using SOCKS proxies and tools like Fscan to find further targets inside the network. Talos observed this scanning behavior in UAT-9921 incidents.
- Long-term stealthy access. The implant’s RBAC and audit features let operators control which team members can run high-risk tooling, hinting the framework is built for sustained operations.
Technical snapshot
| Component | Notes |
|---|---|
| Implant language | Zig (primary Linux implant). |
| Plugin language | C (compiled on demand for target kernels). |
| Backend | Go, role-based C2 with RBAC controls. |
| Persistence | Kernel and user-space techniques; container and cloud metadata checks. |
| Notable capability | Compile-on-demand plugins, Windows DLL side-loading support in some builds. |
Quotes from the researchers
“VoidLink stands as the first evidently documented case of a highly capable malware framework authored with strong AI assistance, showing rapid feature development and modularity.” Check Point Research.
“Operators deploying VoidLink used compromised hosts to implant C2 and then perform internal scanning and targeted credential collection. The activity indicates deliberate, cloud-focused tradecraft.” Cisco Talos.
Why VoidLink is hard to detect
- It runs inside cloud workloads and containers where defenders expect many binaries and ephemeral processes.
- It tailors behavior by fingerprinting the host, reducing noisy actions on high-value or well-monitored systems.
- Compile-on-demand plugins mean each target can receive a unique binary, limiting signature reuse and detection.
Immediate defensive steps
- Search for unusual binaries and unexpected native modules in Linux hosts and containers. Compare hashes against known IOCs from vendor reports.
- Monitor for unexpected outbound connections to C2 infrastructure, especially persistent WebSocket or custom protocol traffic originating from cloud instances.
- Hunt for SOCKS proxy processes or signs of proxying that could indicate internal reconnaissance.
- Audit cloud metadata access and rotate any exposed credentials or tokens. Treat any cloud instance with elevated metadata access as high risk.
- Use runtime detection: inspect containers for processes that spawn compilers or unusual toolchains at runtime, since compile-on-demand behavior often invokes build toolchains.
Longer term mitigations
- Implement least privilege for service accounts and metadata access.
- Harden CI pipelines and require artifact signing for images and binaries.
- Enforce network segmentation between workloads and management networks.
- Deploy kernel integrity monitoring and EDR that covers container runtime and host kernel hooks.
- Share telemetry with trusted vendors so indicators from early detections are distributed rapidly.
FAQ
A: Researchers have confirmed deployments and victim cases dating back to at least September 2025, and Cisco Talos links current activity to UAT-9921. The framework is operational and seen in targeted campaigns, not just a lab proof-of-concept.
A: Check Point’s analysis found development patterns consistent with heavy LLM assistance and spec-driven generation. That does not prove AI wrote every line, but it strongly indicates AI accelerated development.
A: Cloud providers, technology companies, and financial services that run Linux workloads and manage sensitive cloud credentials are primary targets. DevOps and cloud admin roles are especially attractive to operators.
A: The framework’s RBAC model and compile-on-demand design imply it could be adapted into a service or sold to affiliates, increasing future risk. Researchers warn defenders to expect faster proliferation of similar tools.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages