Global Defense Sector Faces Coordinated Cyberattacks from China, Russia, Iran & North Korea
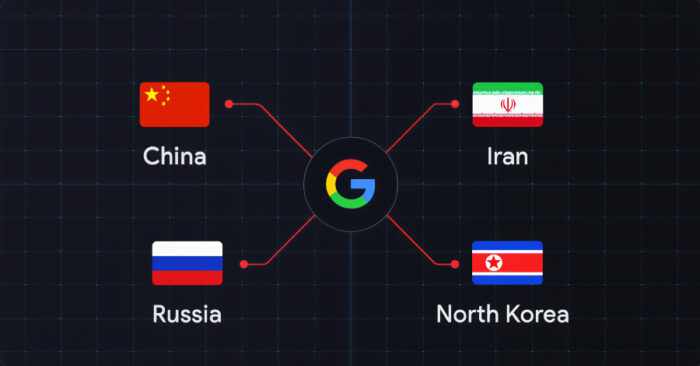
Cybersecurity researchers at Google Threat Intelligence Group (GTIG) report that major state-linked hackers from China, Russia, Iran, and North Korea are actively targeting the global defense industrial base (DIB). These operations include espionage, credential theft, malware delivery, and exploitation of recruitment processes aimed at military suppliers, contractors, and key personnel.
Defense contractors and their supply chains are facing a multi-vector siege. Attacks extend beyond traditional network intrusions to include manipulation of personal devices, job application channels, and operational technology like edge devices. The campaign reflects how modern warfare plays out in digital space as much as on physical battlefield

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
What Google Observed in the Defense Sector
Google’s threat intelligence report highlights multiple concurrent tactics used by state-aligned actors and associated groups:
Focus on battlefield technologies
Many operations aim at companies that build unmanned aircraft systems (UAS) and other next-generation military platforms. These technologies have strategic significance in conflicts such as the Russia-Ukraine war, drawing persistent interest from espionage groups.
Targeting individuals and recruitment processes
Threat actors are increasingly attacking employees and applicants of defense firms. This includes spoofed hiring platforms, fake job offers, and sophisticated social engineering designed to harvest login credentials or install malware on personal systems.
Edge devices and network appliances exploited
Groups emphasize initial access via edge devices like VPNs, routers, or firewalls. These entry points can bypass traditional enterprise defenses and grant long-term access to internal networks.
Supply chain and manufacturing pressure
Beyond direct attacks on defense companies, broader manufacturing and supply of dual-use goods face continual targeting. Malicious activity against subcontractors and third-party suppliers increases risk to the entire industrial base.
Notable Actors and Behaviors Identified
Google and security analysts have linked a range of state-linked and sophisticated clusters to these campaigns:
| Actor / Cluster | Country Link | Actions Observed |
|---|---|---|
| APT44 (Sandworm) | Russia | Exfiltrated encrypted messaging data; focused on battlefield support targets. |
| TEMP.Vermin (UAC-0020) | Russia | Used malware like VERMONSTER and SPECTRUM on drone and surveillance targets. |
| UNC5125 (FlyingYeti) | Russia | Employed reconnaissance forms and malware against UAV operators. |
| UNC5792 | Russia | Targeted secure messaging apps and military entities. |
| UNC6446 | Iran | Distributed custom malware via resume builders to aerospace/defense roles. |
| UNC6508 | China nexus | Used REDCap exploit to deploy INFINITERED malware for persistent access. |
This list is illustrative but not exhaustive. Google also noted that distinct hacktivist and criminal elements join state-sponsored campaigns, complicating the threat landscape.
How These Campaigns Operate
Cyber operations against defense targets show several key patterns:
- Credential harvesting: Attackers use fake hiring or recruitment emails to collect usernames, passwords, and MFA codes.
- Phishing and malware delivery: Targeted messages and archives may contain malicious scripts that deploy credential stealers or remote access tools.
- Reconnaissance and lateral movement: After initial access, attackers map internal systems and escalate privileges to reach sensitive environments.
- Evasion of detection: Many intrusions intentionally avoid endpoint detection and response (EDR) tools and may operate on personal devices outside corporate oversight.
How These Campaigns Operate
Cyber operations against defense targets show several key patterns:
- Credential harvesting: Attackers use fake hiring or recruitment emails to collect usernames, passwords, and MFA codes.
- Phishing and malware delivery: Targeted messages and archives may contain malicious scripts that deploy credential stealers or remote access tools.
- Reconnaissance and lateral movement: After initial access, attackers map internal systems and escalate privileges to reach sensitive environments.
- Evasion of detection: Many intrusions intentionally avoid endpoint detection and response (EDR) tools and may operate on personal devices outside corporate oversight.
Implications for Defense Industry Security
| Risk Area | Impact |
|---|---|
| Production and R&D theft | Loss of intellectual property slows innovation; adversaries gain competitive advantage. |
| Operational disruption | Malware or ransomware may interrupt supply chains. |
| Credential reuse and identity theft | Compromised employee credentials may lead to broader access. |
| Supply chain cascading effects | Attacks on subcontractors may affect prime contractors indirectly. |
Recommended Defensive Actions
- Network segmentation: Isolate sensitive systems and audit privileged access frequently.
- Employee awareness and training: Security teams should educate employees on phishing and job-offer scams.
- Harden recruitment pipelines: Verify job portals and email sources; implement DMARC, DKIM, and SPF protections.
- Endpoint management: Extend protections to personal devices used for work tasks.
- Zero trust and multi-factor authentication: Enforce strong MFA across both corporate and cloud services.
FAQ
A: Multiple nation-state actors linked to China, Russia, Iran, and North Korea are involved, often using tailored phishing, malware, and espionage techniques.
A: No. Supply chain partners, personnel, and even job applicants have been targeted to broaden access vectors.
A: Fake recruitment processes can trick individuals into giving up credentials or installing malicious software, bypassing traditional network defenses.
A: Not always. Some campaigns focus on reconnaissance and credential theft, while others use malware like credential stealers or remote access tools.
A: Very. The combination of state actors, hacktivists, and cybercriminals working around the globe underscores a persistent, strategic risk to defense industrial base security.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages