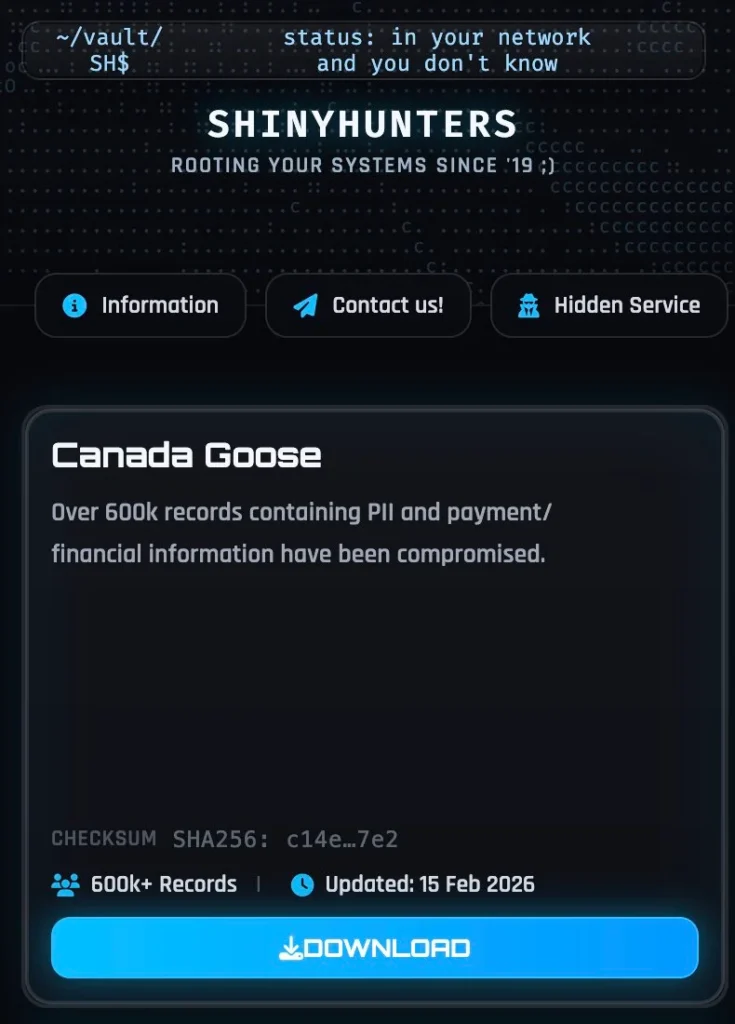
Canada Goose 600K Customer Records Leaked: ShinyHunters Claims Third-Party Breach

ShinyHunters claims to have stolen over 600,000 Canada Goose customer records. The 1.67GB dataset contains names, emails, phone numbers, billing/shipping addresses, IP addresses, order histories, and partial payment card data (last 4 digits, some BINs). Canada Goose found no evidence of direct system breach.
The Toronto-based luxury outerwear brand told BleepingComputer the data relates to historical transactions. Company review shows no unmasked financial information exposed. Canada Goose investigates dataset accuracy and scope.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
ShinyHunters added Canada Goose to its leak site this week. JSON format reveals e-commerce checkout records with fields like checkout_id, shipping_lines, cart_token. Data enables targeted phishing against high-value customers with purchase histories.
Hackers deny connection to recent SSO attacks. Group claims August 2025 third-party payment processor breach, unverified by BleepingComputer. Dataset schema matches hosted payment platforms.
ShinyHunters targets major e-commerce brands through extortion. Victims face data leaks when refusing payments.
Canada Goose Response: “We have no indication of any breach of our own systems. Our review shows no evidence that unmasked financial data was involved. Canada Goose remains committed to protecting customer information.”
Exposed Data Categories
| Data Type | Risk Level | Threat Vector |
|---|---|---|
| Names/Emails/Phones | High | Phishing campaigns |
| Billing/Shipping Addresses | High | Physical fraud |
| Partial Card Data (Last 4/BIN) | Medium | Carding + profiling |
| IP Addresses + Order History | High | Account takeover |
| Device/Browser Info | Medium | Session hijacking |
ShinyHunters Profile
Prolific extortion group since 2020. Targets:
- E-commerce platforms
- SaaS services
- Cloud environments
- Recent SSO vishing campaigns
High-profile victims include Panera Bread (51M records), others unnamed. Refusal triggers public leaks.
Company Background
- Founded: 1957, Toronto Canada
- Industry: Luxury performance outerwear
- Employees: ~4,000 globally
- Retail: International footprint
Breach Timeline
- August 2025: Alleged third-party breach
- Feb 2026: ShinyHunters leak site posting
- Feb 15, 2026: Canada Goose statement
- Ongoing: Dataset accuracy investigation
Risk Implications
Partial card data insufficient for direct fraud. Combined with addresses and purchase history enables sophisticated social engineering. High-value customers prime targets for executive impersonation.
No notification timeline confirmed. Canada Goose assesses scope before customer outreach.
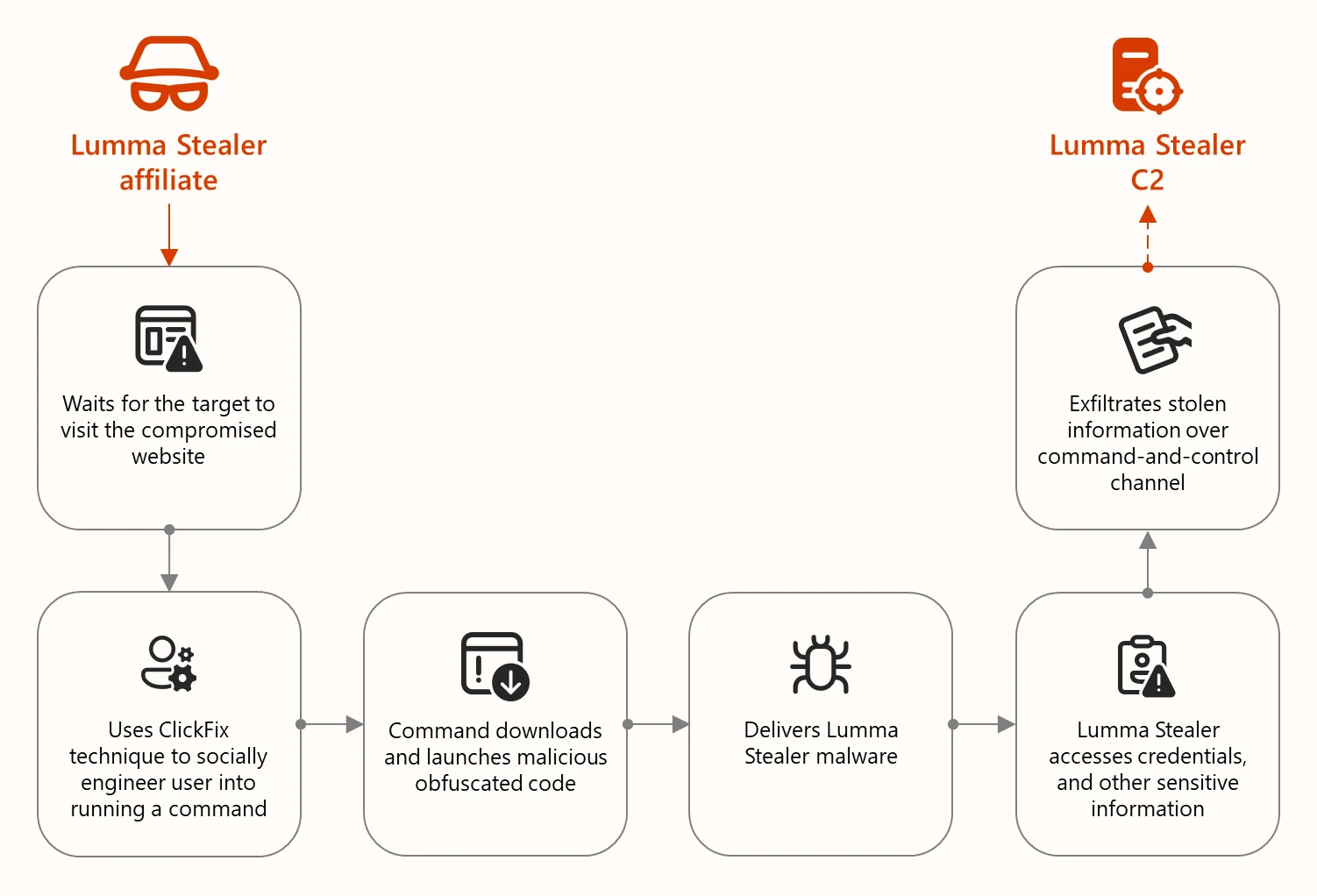
Threat Actor Tactics
ShinyHunters favors supply chain compromise over direct breaches. Third-party payment processors common vectors. Dataset structure suggests legitimate e-commerce export format exploited.
FAQ
600,000+ customer records
No evidence found, investigating third-party source
Partial (last 4 digits, BINs), no full cards
August 2025 payment processor breach, unverified
Under investigation, no timeline confirmed
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages