Lumma Stealer and Ninja Browser Attack Global Organizations Through 4,000+ Malicious Google Groups
Attackers created over 4,000 malicious Google Groups and 3,500 Google-hosted URLs to distribute Lumma Stealer and trojanized Ninja Browser malware worldwide. CTM360 threat researchers uncovered the campaign abusing Google’s trusted infrastructure for credential theft and persistent device compromise
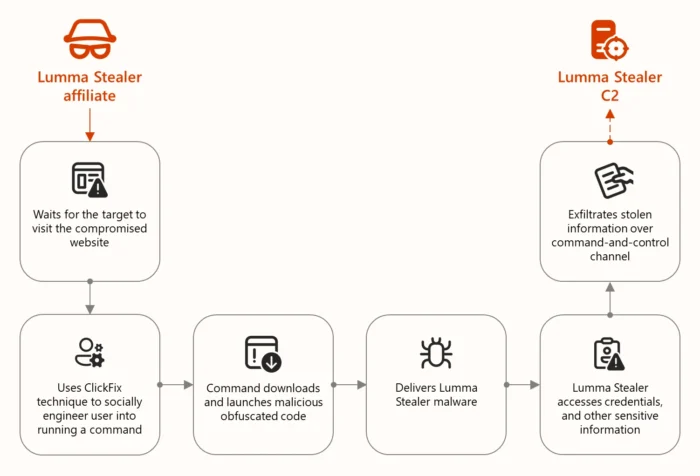
Campaign targets industry professionals through tailored social engineering. Attackers post legitimate-looking technical discussions in sector-specific Google Groups. Links disguised as “Download {Company} for Windows 10” lead to OS-specific malware payloads.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Windows victims receive 950MB password-protected archives padded with null bytes to evade antivirus scanners. Linux users download fake Ninja Browser with hidden malicious extensions. Google Docs/Drive redirectors detect operating systems before payload delivery.
Lumma Stealer exfiltrates browser credentials, session cookies, and executes shell commands via healgeni[.]live C2. Ninja Browser silently installs “NinjaBrowserMonetisation” extension for tracking and remote content injection.
Campaign infrastructure spans multiple IPs and domains confirming sophisticated global operation.
Google Groups appear legitimate hosting technical discussions about network issues and authentication errors. Industry keywords and organization names increase click rates significantly. URL shorteners mask final payloads.
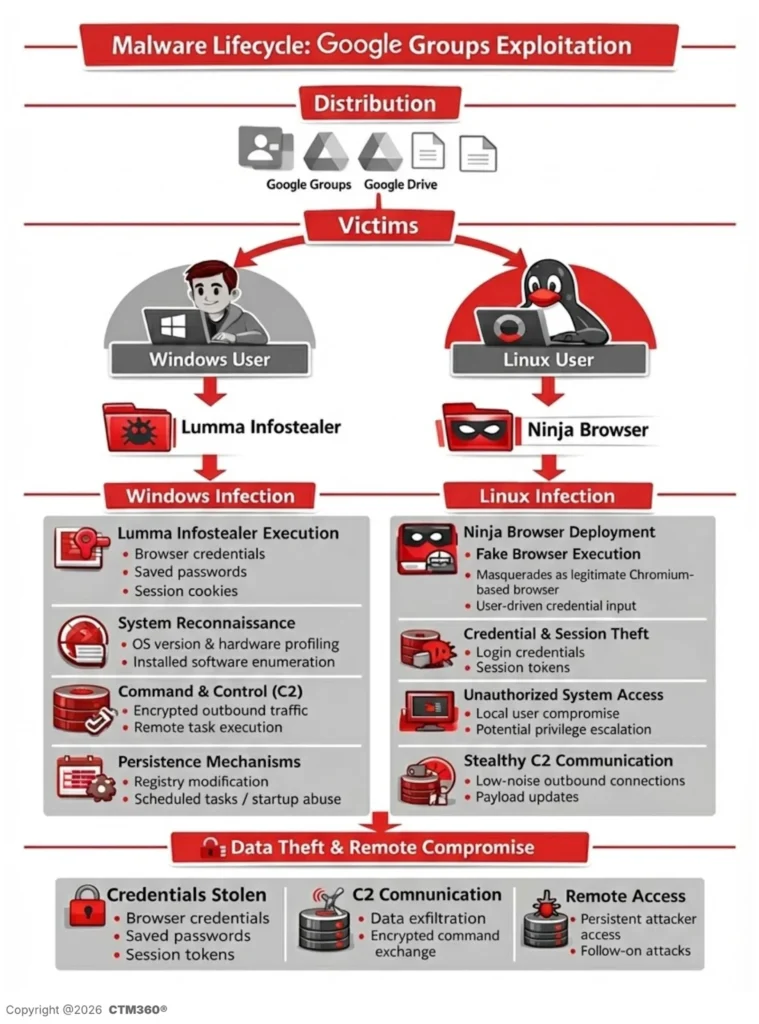
CTM360 identified consistent patterns across thousands of Groups confirming coordinated campaign. Attackers exploit Google’s reputation bypassing traditional email security controls.
CTM360 Report: “4,000+ malicious Google Groups, 3,500 Google-hosted URLs actively distributing Lumma Stealer (Windows) and Ninja Browser (Linux)”
Infection Chains
| Platform | Payload | Size | Evasion | Persistence |
|---|---|---|---|---|
| Windows | Lumma Stealer | 950MB archive (33MB actual) | Null byte padding | Memory-resident |
| Linux | Ninja Browser | Chromium-based | Malicious extensions | Scheduled tasks |
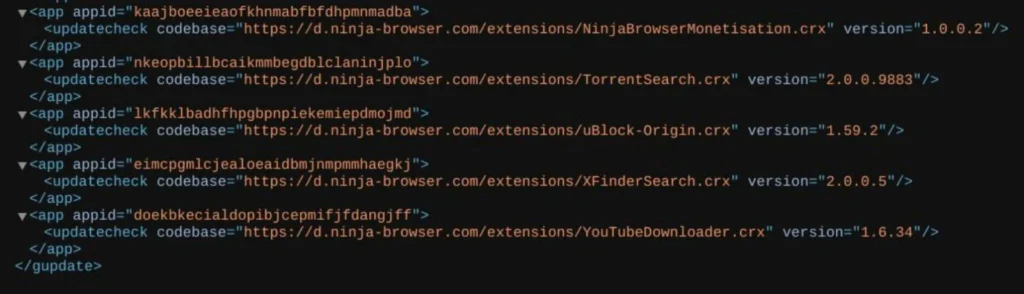
Windows Attack Flow
- Google Group → tailored download link
- Google Docs/Drive redirector detects Windows
- 950MB oversized archive download
- AutoIt executable reassembles payload
- Lumma Stealer: credential/session theft
- C2: healgeni[.]live via multipart/form-data
Linux Attack Flow
- Google Group → tailored download link
- Google redirector detects Linux
- Ninja Browser (trojanized Chromium)
- Silent “NinjaBrowserMonetisation” extension
- Scheduled tasks poll attacker servers
- Russian “X-Finder” search + AI redirects
Indicators of Compromise
IPs:
- 152.42.139[.]18
- 89.111.170[.]100
Domains:
- healgeni[.]live (Lumma C2)
- ninja-browser[.]com
- nb-download[.]com
- nbdownload[.]space
Malicious Behaviors
Lumma Stealer:
- Browser credential extraction
- Session cookie harvesting
- Shell command execution
- Obfuscated HTTP POST exfiltration
Ninja Browser Extension:
- User tracking via unique IDs
- Script injection into sessions
- Remote content loading
- Cookie/tab manipulation
- XOR/Base56 obfuscated JavaScript
Defensive Measures
- Block listed IOCs at firewall/EDR
- Inspect Google Docs/Drive redirect chains
- Monitor scheduled task creation
- Audit browser extension installations
- Train users: verify forum downloads
- Analyze oversized archives (>500MB)
Strategic Implications
Trusted SaaS platforms become malware delivery infrastructure. Google Groups bypass corporate email filters completely. OS fingerprinting ensures high success rates. Cross-platform coverage eliminates detection gaps.
Campaign monetizes through credential theft enabling account takeovers across enterprise environments globally.
FAQ
4,000+ Google Groups, 3,500+ Google URLs
Lumma Stealer via 950MB padded archive
Trojanized Ninja Browser + malicious extensions
healgeni[.]live
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages