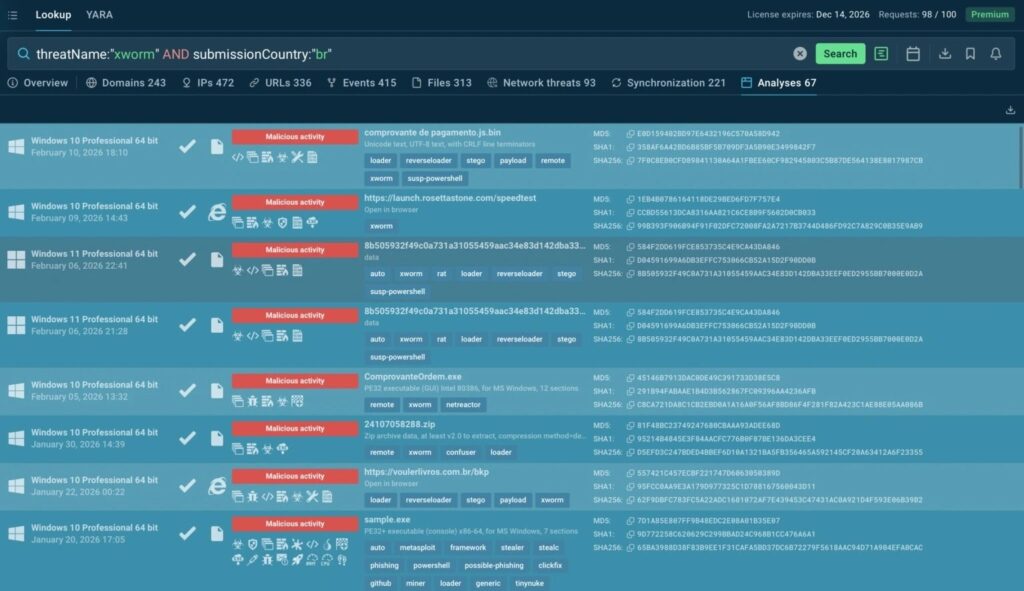
XWorm v5.6 Targets LATAM via Fake Bank Receipts

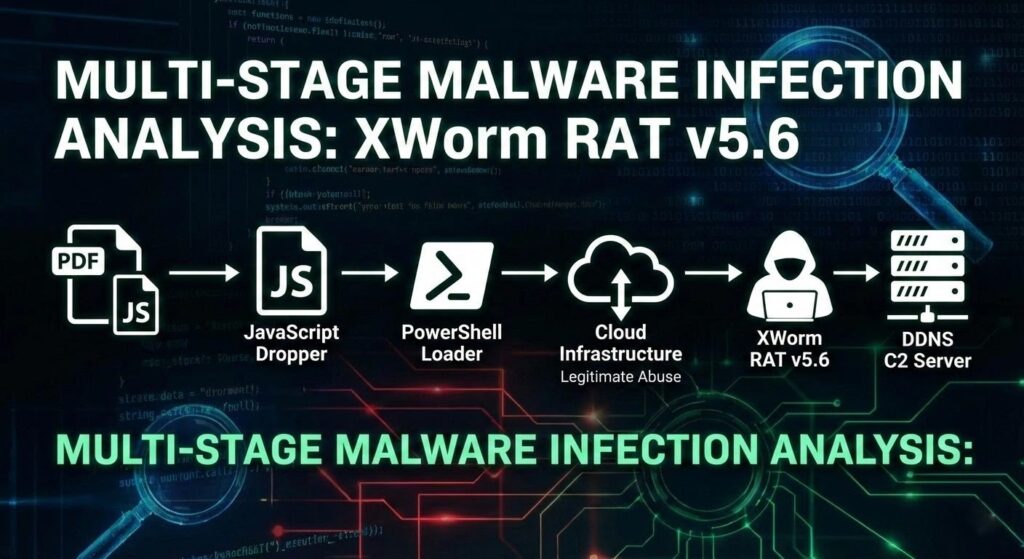
XWorm v5.6 malware spreads through fake Bradesco bank receipts targeting Brazilian and LATAM businesses. The campaign delivers a multi-stage RAT that steals credentials, hijacks browser sessions, and sets up ransomware staging. Researcher Moises Cerqueira uncovered the sophisticated infection chain.
Attackers disguise droppers as PDFs using .pdf.js double extensions. Files inflate to 1.2MB with junk Unicode data including emojis and homoglyphs. This evades static scanners expecting small malicious scripts.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
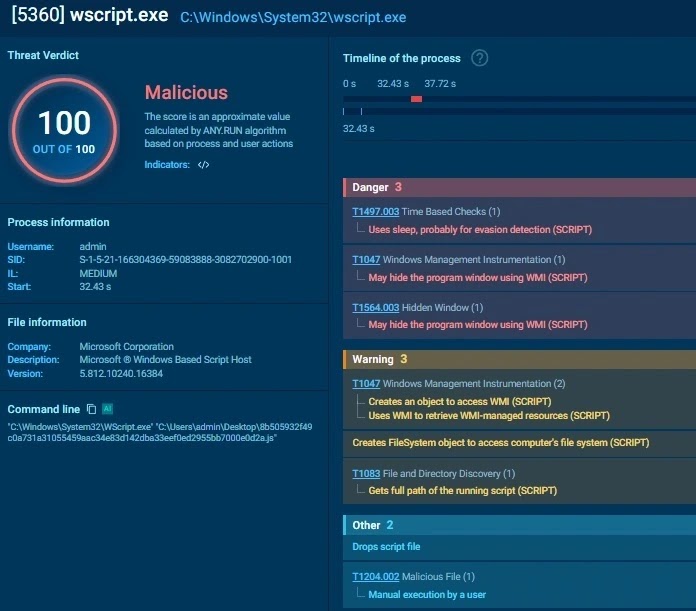
Runtime .replace() functions strip noise to reveal PowerShell commands. WMI spawns hidden PowerShell sessions instead of detectable WScript.Shell calls. Five-second Sleep(5000) delays beat sandbox detection.
Complete Infection Chain
Stage 1 – WSH Dropper:
- .pdf.js file triggers Windows Script Host
- Unicode junk hides PowerShell payload
- WMI Win32_Process spawns hidden PS1
- Sleep(5000) evades behavioral analysis
Stage 2 – Steganography Loader:
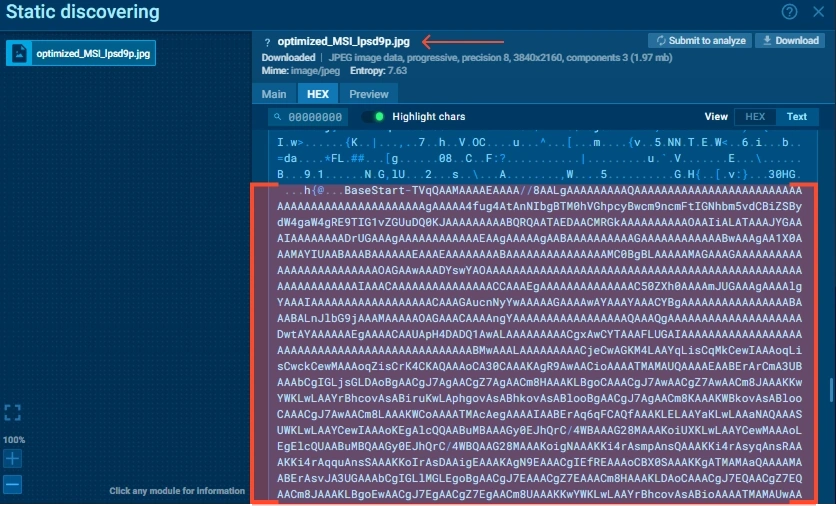
- Fetches Cloudinary JPEG: optimized_MSI_lpsd9p.jpg
- Extracts Base64 .NET assembly between BaseStart-/BaseEnd markers
- Reflection.Assembly.Load() runs filelessly
- Decodes reversed Base64 for final URL
Stage 3 – Persistence DLL:
- VB.NET assembly creates scheduled task via COM TaskService
- No command-line artifacts in logs
- Task re-runs Stage 2 PowerShell loader at logon
- Modular re-infection loop
Stage 4 – XWorm v5.6:
- Reversed Base64 from voulerlivros[.]com[.]br/arquivo_20260116064120.txt
- Injects into CasPol.exe (LOLBIN)
- AES-ECB C2 config (weak MD5 mutex key)
Evasion Techniques Table
| Technique | Purpose | Detection Bypass |
|---|---|---|
| .pdf.js double extension | Social engineering | File type confusion |
| 1.2MB junk Unicode | Static analysis | Size-based filtering |
| WMI vs WScript | Process visibility | No cmd.exe parent |
| Sleep(5000) | Sandbox evasion | Timing heuristics |
| Cloudinary JPEG stego | Network blending | Legit CDN traffic |
| CasPol.exe injection | Process hiding | Signed Microsoft binary |
| COM TaskScheduler | Persistence | No schtasks.exe logs |
Decrypted C2 Configuration
| Indicator | Value |
|---|---|
| C2 Domain | jholycf100[.]ddns[.]com[.]br |
| C2 IP | 152[.]249[.]17[.]145:7000 |
| Mutex | V2r1vDNFXE1YLWoA |
| Protocol | <Xwormmm> |
| Payload URL | voulerlivros[.]com[.]br/arquivo_20260116064120.txt |
| Stego URL | res[.]cloudinary[.]com/…/optimized_MSI_lpsd9p.jpg |
| SHA-256 | 7befeacf0b3480fb675d0cab7767b5b9697edc9d0e05982025a06ead0054afd5 |
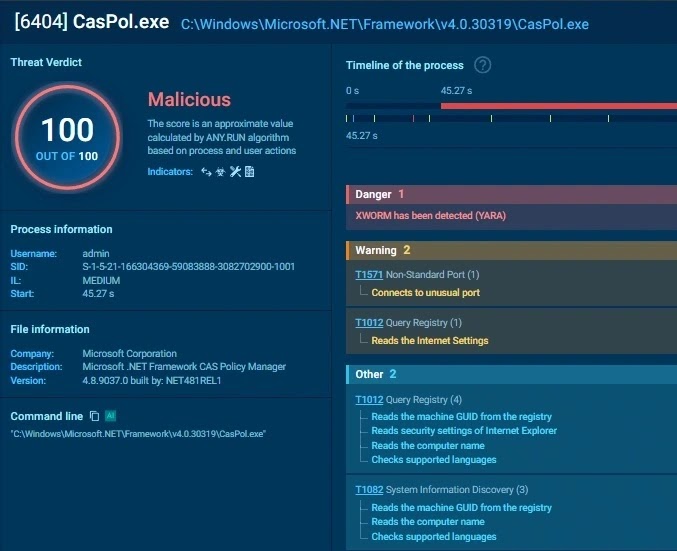
CasPol.exe Abuse Details
Living off the Land Binary:
textC:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe
Malware hollows legitimate CasPol.exe process. Network activity from signed utility flags in sandboxes. Weak AES-ECB reveals full C2 post-infection.
Detection Rules
Endpoint:
textparent_image: "CasPol.exe"
OR image_loaded: "CasPol.exe" AND NetworkConnect
.pdf.js file execution
WMI spawning PowerShell + Sleep(5000)
Network:
textCloudinary + "BaseStart" in response
voulerlivros[.]com[.]br TXT requests
jholycf100[.]ddns[.]com[.]br:7000
Persistence:
textTaskScheduler COM creation without schtasks.exe
powershell.exe spawn from scheduled task
LATAM Targeting Specifics
Primary vector: Bradesco receipts (Brazil’s 2nd largest bank)
Social engineering: Urgent payment confirmations
Regional focus: Brazilian businesses, Portuguese lures
Infrastructure: BR-hosted C2 domains
Immediate Response Actions
Hunt queries:
textfilename:*.pdf.js
process:powershell.exe AND parent:wmi*
network:cloudinary.com AND "BaseStart"
image:caspol.exe AND network_connect
Block indicators:
text152.249.17.145
jholycf100.ddns.com.br
voulerlivros.com.br
Prevention Framework
Email gateway:
- Block .pdf.js attachments
- Unicode normalization on subjects
- Bradesco sender reputation
Endpoint controls:
- CasPol.exe execution monitoring
- WMI PowerShell spawn alerts
- Scheduled task creation logging
Business Impact
Single click enables:
- Browser credential theft
- Session hijacking (email, SaaS)
- Business email compromise
- Ransomware staging ground
Low initial footprint delays detection significantly.
FAQ
Fake Bradesco .pdf.js receipts targeting LATAM businesses.
CasPol.exe process hollowing from .NET Framework folder.
Base64 payload between BaseStart-/BaseEnd markers in Cloudinary JPEG.
COM TaskScheduler creating logon PowerShell loader task.
AES-ECB with MD5-derived mutex key for C2 config.
C2 domains: jholycf100.ddns.com.br, voulerlivros.com.br.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages