Predator Spyware Bypasses iOS Camera and Microphone Indicators via SpringBoard Hook

Intellexa’s Predator spyware defeats iOS 14+ recording indicators. It hooks SpringBoard’s sensor activity handler to suppress green camera and orange microphone dots. Jamf researchers reverse-engineered the technique requiring prior kernel access. Users see no alerts during surveillance.
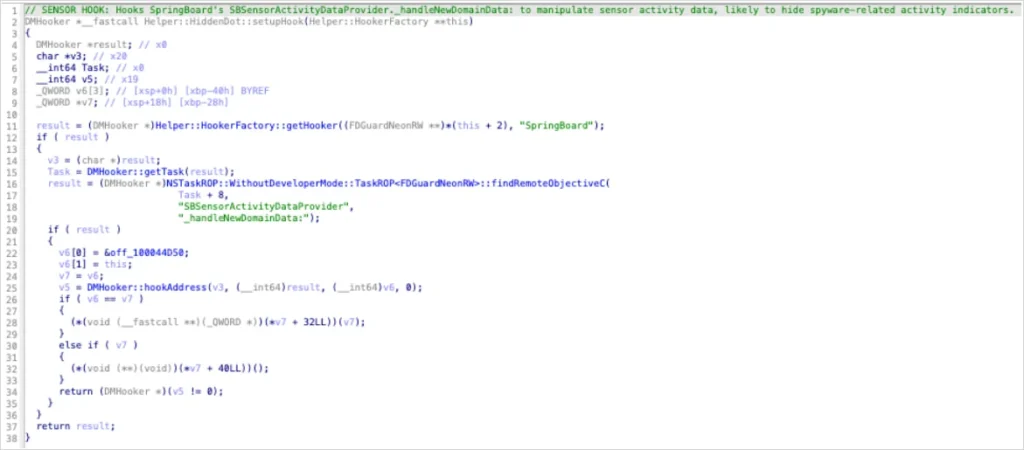
Predator targets high-profile victims using zero-click exploits. Once kernel privileges obtained, it injects into SpringBoard. The HiddenDot::setupHook() function intercepts _handleNewDomainData: calls from SBSensorActivityDataProvider. Nullifying the provider object silently drops updates before UI rendering.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Objective-C nil messaging ignores calls to null objects. One hook blocks all sensor indicators. Dead code hints at abandoned SBRecordingIndicatorManager approach. VoIP recording modules lack built-in stealth, relying on HiddenDot. Camera access uses ARM64 pattern matching and PAC bypass.
Hook Mechanism Table
| Component | Role | Hook Target |
|---|---|---|
| SBSensorActivityDataProvider | Aggregates camera/mic events | _handleNewDomainData: |
| SpringBoard | Renders status bar indicators | HiddenDot::setupHook() |
| mediaserverd | Handles VoIP/audio streams | Injection for persistence |
Single hook defeats both green/orange dots.
Technical Breakdown
Predator injection sequence:
- Kernel exploit grants code execution.
- Inject UMHooker into SpringBoard via Mach exceptions.
- Locate _handleNewDomainData: via breakpoint scanning.
- Replace with null-returning stub.
- Sensor events silently ignored.
VoIP falls back to main HiddenDot module.
Detection Indicators
Jamf identifies compromise artifacts:
- Unexpected SpringBoard memory mappings.
- Exception ports registered by non-Apple code.
- Breakpoint instructions in sensor handlers.
- mediaserverd writing audio to temp paths.
- Missing indicators during known mic access.
EDR on managed devices flags anomalies.

Predator Delivery Context
Intellexa spyware chain:
- Zero-click iMessage/PDF exploits.
- Chrome zero-days in watering holes.
- State-sponsored targeting (journalists, activists).
- US sanctions on operators.
Post-infection focuses on persistence and stealth.
Evasion Advantages
SpringBoard hook excels because:
- Upstream interception blocks all downstream indicators.
- No per-app hooks needed.
- Objective-C nil handling requires no cleanup.
- Works across iOS 14-17 sensor APIs.
Superior to dead-code manager-level approach.
Mitigation for Enterprises
MDM admins implement these:
- Lockdown SpringBoard exception ports.
- Monitor mediaserverd file writes.
- Block undocumented kernel task_for_pid calls.
- Deploy Jamf Protect for spyware signatures.
- Enforce latest iOS patches quarterly.
Personal users update immediately.
Comparison to Legit Apps
| Entity | Can Bypass Indicators? | Access Level |
|---|---|---|
| App Store Apps | No | Sandboxed |
| Predator | Yes | Kernel/root |
| State Malware | Yes | Kernel/root |
Requires compromise first.
Jamf Recommendations
Researchers advise monitoring:
# Suspicious SpringBoard mappings
vmmap SpringBoard | grep -v Apple
# mediaserverd temp files
ls /private/var/tmp/* | grep audio
# Sensor events without UI updates
frida-trace -f SpringBoard -m "*Sensor*"
FAQ
Hooks SpringBoard _handleNewDomainData: to nullify SBSensorActivityDataProvider.
No. Single hook suppresses all sensors.
SpringBoard, mediaserverd.
No. Sandbox prevents kernel access.
Anomalous memory maps, missing dots during mic use.
No. Relies on HiddenDot module.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages