'Massiv' Android Banking Malware Disguised as IPTV App Steals Banking Access and Identities

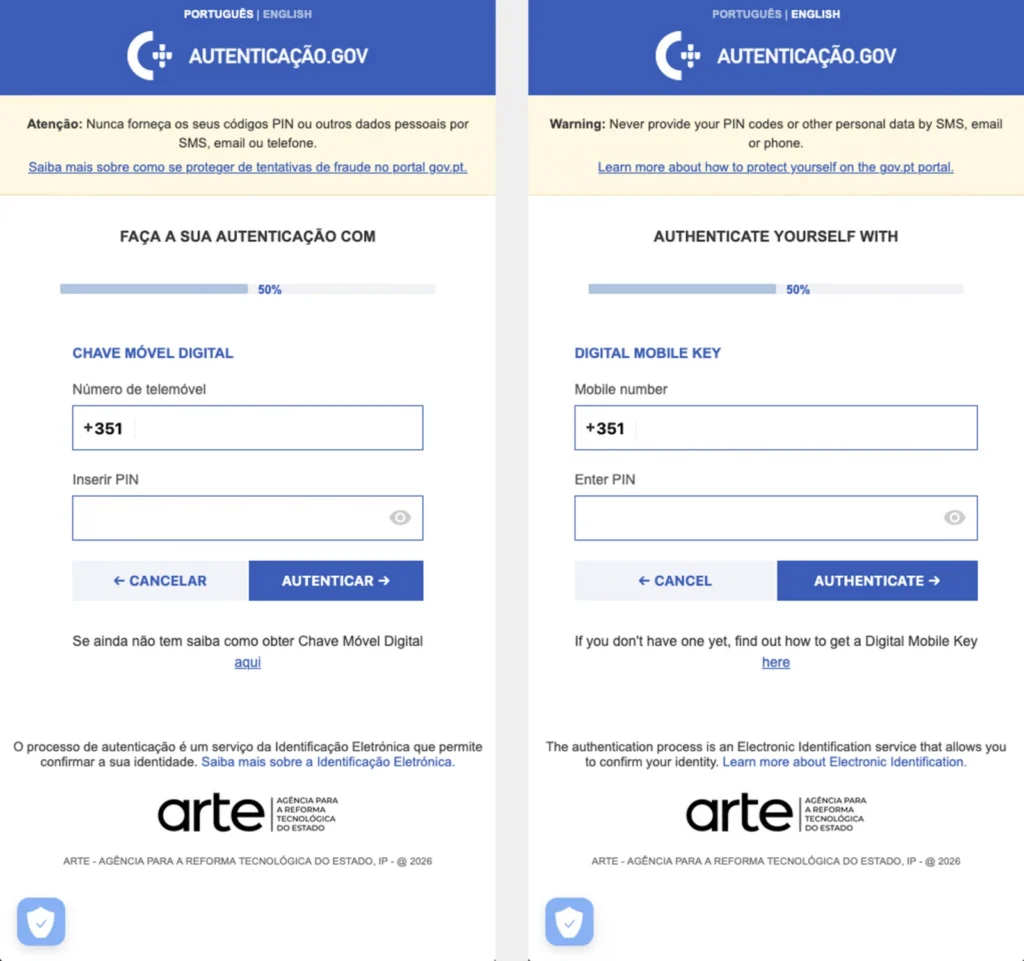
Massiv banking trojan targets Android users through fake IPTV apps. The malware overlays screens, logs keystrokes, and enables remote device control. ThreatFabric researchers identified campaigns hitting Portuguese government authentication apps connected to Chave Móvel Digital. Attackers use stolen data to bypass KYC checks and open fraudulent accounts.
Operators control victims through two methods. MediaProjection API streams live screens. Accessibility Service extracts UI trees with text, coordinates, and interaction data. This bypasses banking apps blocking screenshots. Fraudsters open new accounts in victim’s name, take loans, and leave debts behind.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
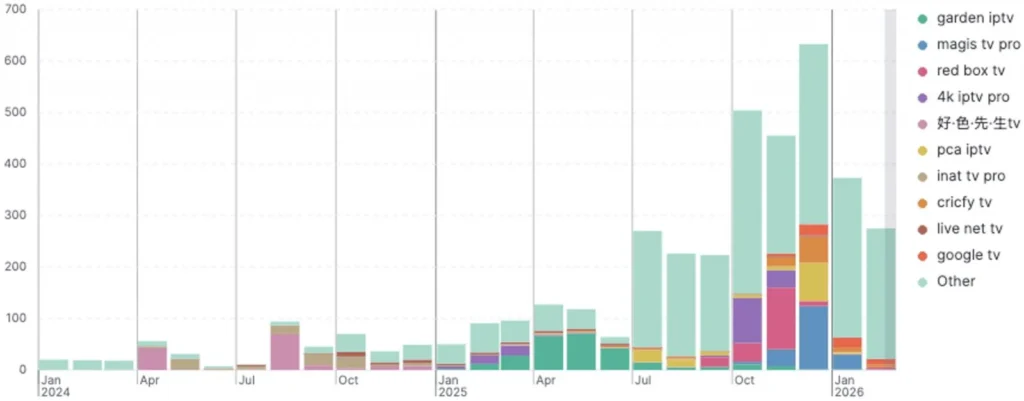
IPTV lures exploded over eight months. Users expect pirated streams outside Google Play. Sideloading seems normal. Fake apps drop Massiv payload. Some load real IPTV sites via WebView to avoid suspicion. Spain, Portugal, France, and Turkey see heaviest attacks.
Attack Capabilities Table
| Feature | Technique | Purpose |
|---|---|---|
| Screen Overlay | WebView injection | Capture login credentials |
| Keylogging | Accessibility Service | Log passwords, OTPs |
| Live Streaming | MediaProjection API | Real-time operator control |
| UI Tree Extraction | Accessibility dump | Bypass screenshot protection |
| Device Admin | Silent activation | Prevent uninstall |
Full banking takeover enabled.
Target Applications
Massiv focuses on high-value apps:
- Portuguese Chave Móvel Digital authentication.
- Major EU/Spanish/Portuguese banks.
- Government identity services.
- KYC verification portals.
Stolen data fuels synthetic identity fraud.
Remote Control Modes
Operators choose between:
- Screen Streaming: MediaProjection captures everything visually.
- UI Automation: Accessibility Service reads structured data (text, buttons, fields).
UI mode defeats banking anti-malware protections perfectly.
IPTV Lure Trend
Fake IPTV APKs surged recently:
- Copyright violations keep apps off Google Play.
- Users accustomed to Telegram/Discord distribution.
- WebView fakes maintain credibility.
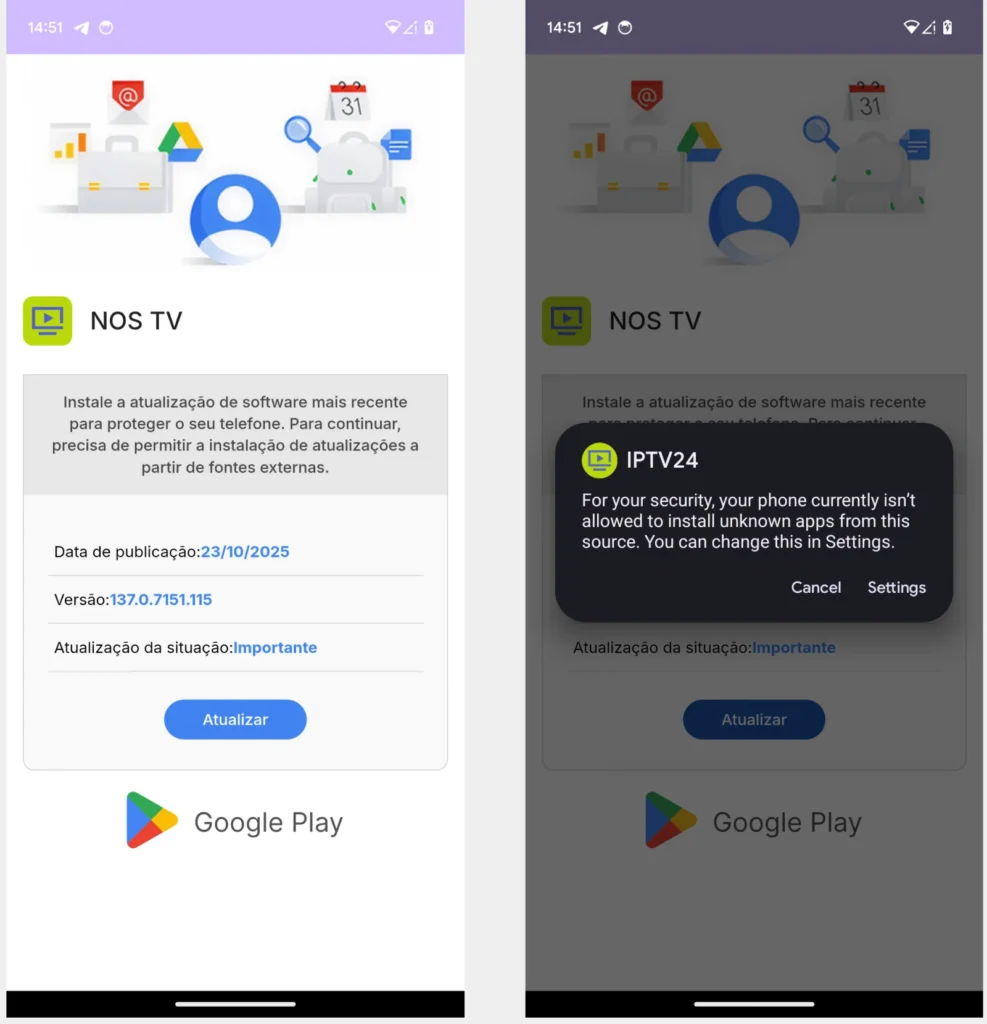
- Dropper installs Massiv silently.
Targets: Spain (40%), Portugal (25%), France (20%), Turkey (15%).
Infection Chain
- Lure: IPTV APK from Telegram/social media.
- Dropper: Fake app requests permissions.
- Payload: Massiv extracts from assets.
- Persistence: Accessibility + Device Admin.
- C2: Operator receives control panel access.
Victim sees working IPTV interface.
Immediate Protection Steps
Android users act now:
- Disable unknown sources (Settings > Apps > Special Access).
- Revoke Accessibility access for non-system apps.
- Enable Google Play Protect scanning.
- Avoid IPTV APKs from unofficial sources.
- Monitor for overlay attacks during banking.
Only install from Google Play Store.
Detection Indicators
Warning signs of Massiv:
- IPTV app requests Accessibility Service.
- MediaProjection prompts from video apps.
- Banking apps show overlay warnings.
- Device Admin enabled for streaming apps.
- High network to C2 domains.
Uninstall suspicious apps immediately.
Geographic Impact Map
| Country | Attack Share | Primary Lures |
|---|---|---|
| Spain | 40% | Football streams |
| Portugal | 25% | Government apps |
| France | 20% | Premium channels |
| Turkey | 15% | Local sports |
EU banking sector heavily targeted.
Enterprise Defenses
Organizations deploy MDM controls:
- Block Accessibility Service for non-approved apps.
- Disable MediaProjection API enterprise-wide.
- Monitor for overlay permission abuse.
- Whitelist banking apps only.
- Regular Google Play Protect scans.
Employee education critical.
FAQ
Accessibility Service, MediaProjection API, Device Admin.
Spain, Portugal, France, Turkey primarily.
UI tree extraction via Accessibility Service.
No. IPTV interface appears functional.
Telegram, Discord, social media groups.
No. Only sideloaded APKs observed.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages