Shift Left Security Failed: Container Risks and Platform Engineering Fix Developers Need

Shift left promised faster, safer software development. Developers would handle security early in the cycle. Reality proved different. Business pressure for speed crushed security adoption. Developers bypassed slow scans to meet deadlines. Security became a blocker, not a partner.
Public container registries fueled the problem. Developers grab Docker Hub images for velocity. These images carry hidden risks. Qualys analyzed 34,000 public containers and found 7.3% malicious. Cryptominers dominated 70% of threats. 42% leaked AWS keys, GitHub tokens, database credentials.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Organizations lost runtime visibility. Auto-scaling pipelines deploy unvetted code. AI agents execute scripts autonomously. Trusted container images bypass gates. Typosquatting tricks developers into pulling fake images. Manual checks fail under deadline pressure.
Key findings: 2,500 malicious images confirmed.
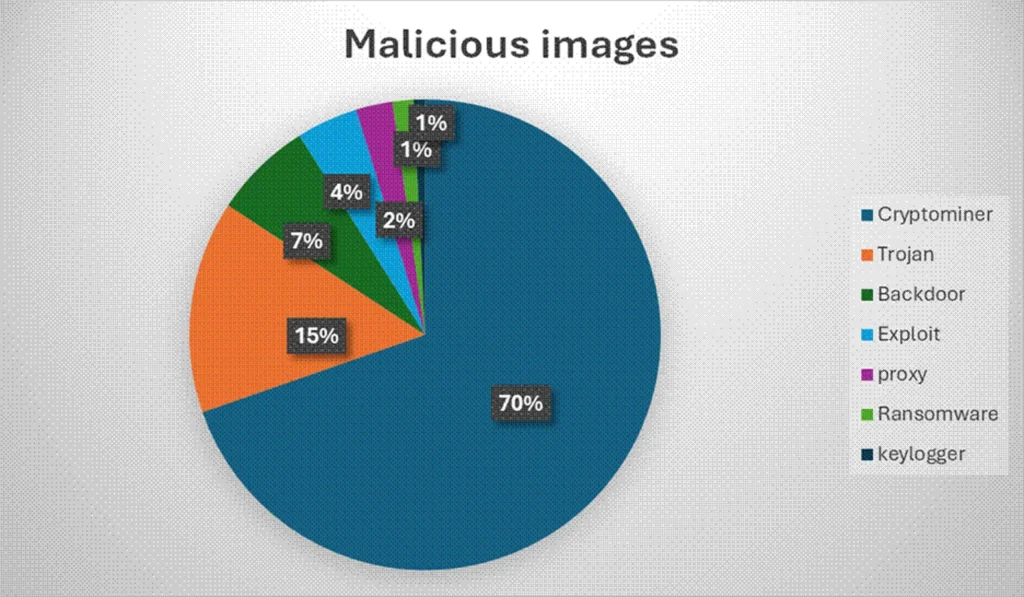
Container Threat Breakdown
| Risk Type | Prevalence | Impact |
|---|---|---|
| Malicious Images | 7.3% (2,500) | Cryptomining, backdoors |
| Cryptominers | 70% of threats | Resource theft, compute costs |
| Secrets Exposure | 42% (>5 secrets/image) | AWS keys, GitHub tokens, DB creds |
| Typosquatting | Primary vector | Fake popular image names |
Public registries lack curation.
Developer Pressure Reality
Businesses demand impossible: fast, good, cheap, secure. Developers face:
- Feature velocity metrics.
- Friday shipping deadlines.
- 4-hour security scans blocking CI/CD.
- Bonus tied to delivery speed.
Security tools feel like friction.
Shift Left Failures
Theory: Fix bugs cheaper in design phase. Practice: Developers drown in:
- Vulnerability scanning.
- Dependency checks.
- Secret detection.
- Compliance audits.
- Infrastructure hardening.
Cognitive overload forces bypasses.
Proposed Shift Down Solution
Move security to platform layer automatically:
- Golden path: Pre-approved images, templates, pipelines.
- Platform team owns enforcement via Terraform, OPA policies.
- Reject non-compliant resources at admission.
- Auto-generate PRs for vulnerable base images.
- Runtime tools kill bad pods autonomously.
Developers cannot make insecure mistakes.
Golden Path Implementation
Secure defaults win adoption:
- Standard templates auto-scan containers.
- CI/CD pipelines reject critical CVEs.
- S3 buckets require versioning by policy.
- Admission controllers block bad images.
- Platform auto-upgrades vulnerable bases.
Off-road requires security review.
Public Registry Risks
Docker Hub, Amazon ECR seem safe. Reality differs:
- No malware scanning at ingestion.
- Typosquatted images mimic popular ones.
- Secrets persist in image layers forever.
- Pull = trust decision bypassing gates.
Proxy all external pulls through internal quarantine.
Platform Engineering Role
Infrastructure becomes security enforcer:
# OPA Policy Example - S3 Versioning Required
deny[msg] {
bucket := input.resources[_]
not bucket.versioning_configuration.status == "Enabled"
msg := "S3 versioning required"
}
Developers request, platform enforces.
Runtime Automation
Beyond prevention, auto-remediate:
- Container spawns shell → pod killed.
- Vulnerable image detected → node isolated.
- Alert fatigue eliminated.
- Developer freed from monitoring.
Security operates autonomously.
Business Alignment Strategy
Security + Dev present united costs:
- Golden path = free security.
- Custom work = explicit security budget.
- Velocity metrics include platform compliance.
- Platform team owns secure defaults.
Incentives align naturally.
Maturity Model Comparison
| Approach | Developer Load | Security Posture | Velocity Impact |
|---|---|---|---|
| Manual Shift Left | High | Poor | Blocked |
| Platform Shift Down | Low | High | Accelerated |
| No Security | Low | None | Risky velocity |
Platform engineering scales best.
FAQ
7.3% per Qualys analysis of 34,000 images.
Slow scans block CI/CD pipelines under deadline pressure.
Platform layer enforces security automatically, freeing developers.
AWS keys, GitHub tokens, database credentials (42% of images).
Pre-approved templates/pipelines make security the default choice.
No. Proxy through internal quarantine repositories.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages