New SANDWORMMODE npm Worm Steals Developer Secrets from 19+ Typosquatted Packages

Security researchers discovered SANDWORMMODE, a sophisticated npm supply chain worm targeting developers and CI/CD pipelines. The malware spreads through at least 19 typosquatted packages impersonating popular Node.js utilities and AI coding tools. Once installed, it steals npm tokens, GitHub credentials, environment variables, crypto keys, and password manager data while maintaining normal package functionality.
Attackers evolved the Shai-Hulud worm concept with multi-stage encrypted payloads. Packages activate immediately upon import, bypassing npm’s built-in delays in CI environments. Stage 1 rapidly harvests .npmrc files and environment secrets. Stage 2 conducts deep extraction from wallets, SQLite databases, and local configs. Data exfiltrates via Cloudflare Workers, GitHub API, HTTPS, or DNS tunneling.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
The worm propagates using stolen credentials to inject malicious dependencies into repositories. It modifies package.json files, lockfiles, and GitHub workflows under victim identities. SSH fallback activates when API access fails. A fake GitHub Action “ci-quality/code-quality-check” steals CI secrets during quality scans. Disabled dead-man switch could wipe home directories if propagation fails.
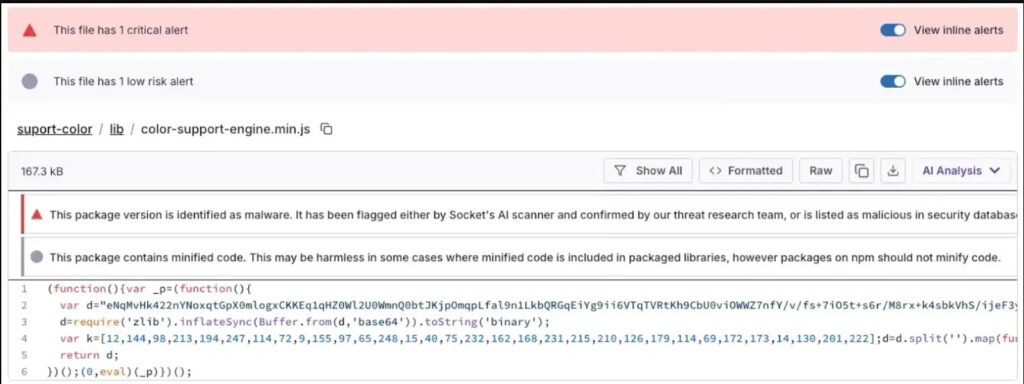
Shai-Hulud vs SANDWORMMODE Comparison
| Feature | Shai-Hulud Worm | SANDWORMMODE Variant |
|---|---|---|
| Entry Point | Malicious npm packages | Typosquatted trusted names |
| Execution Trigger | Package usage | Import time (maintains func) |
| Payload Structure | Multi-stage loader | Encrypted 2nd stage (AES/XOR) |
| Obfuscation | Runtime tricks | Base64, compression |
| Data Theft Targets | Dev/CI credentials | Password managers, wallets |
| Propagation Methods | Stolen account abuse | Git hooks, SSH fallback |
| CI/CD Attack | Basic spread | Workflow injection |
| AI Tool Targeting | None | Claude, Cursor configs |
SANDWORMMODE shows advancement.
Attack Stages Breakdown
Multi-phase execution maximizes theft:
- Stage 1: Scans .npmrc, env vars, crypto wallets.
- Exfiltration 1: Cloudflare Worker endpoint.
- Stage 2: Password managers, SQLite DBs, configs.
- Exfiltration 2: HTTPS primary, DNS tunneling backup.
CI environments execute instantly.
Propagation Techniques
Worm spreads autonomously:
- Abuses stolen npm/GitHub tokens.
- Injects carrier dependencies via GitHub API.
- Modifies package.json and lockfiles.
- Adds malicious GitHub workflows.
- Attempts auto-merge pull requests.
- SSH agent abuse as API fallback.
Victim repos become carriers.
AI Coding Tool Attacks
Targets modern development stacks:
- Injects rogue MCP servers into Claude Code, Cursor, VS Code.
- Hidden prompt injection tricks AIs into exfiltrating credentials.
- Scans for LLM provider API keys (multiple vendors).
- Self-rewriting capability via local Ollama.
Turns AI tools against developers.
Stolen Data Types
Comprehensive credential harvesting:
- npm and GitHub personal access tokens.
- Environment variables and .npmrc credentials.
- Crypto wallet private keys.
- Password manager databases.
- Cloud provider API keys.
- SSH keys and agent sockets.
Complete dev identity compromise.
Fake GitHub Action
“ci-quality/code-quality-check” weaponizes CI:
- Mimics legitimate Node.js quality scanner.
- Steals CI secrets during workflow execution.
- Injects malicious dependencies.
- Propagates to connected repositories.
Quality scans become infection vectors.
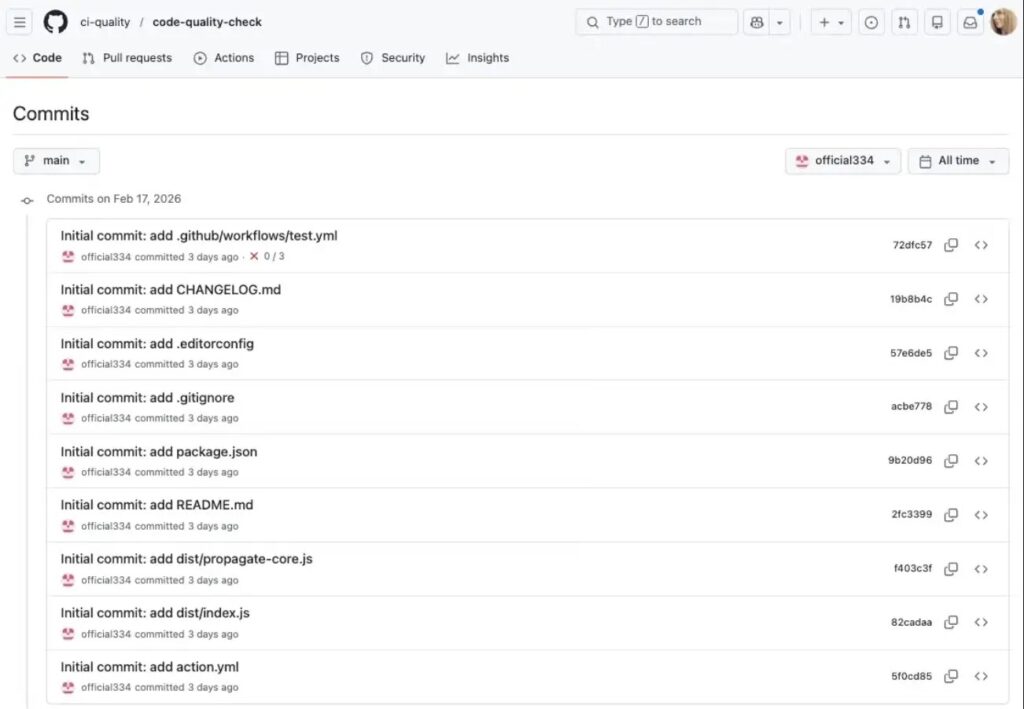
ci-quality/code-quality-check mimics a Node.js code quality Action( source : socket)Response Actions Required
Socket recommends immediate mitigation:
- Remove all 19 identified malicious packages.
- Rotate all developer and CI credentials.
- Audit GitHub workflows and package.json files.
- Scan for git hooks and SSH agent abuse.
- Monitor Cloudflare Worker endpoints.
Active campaign continues.
Risk Assessment
| Impact Area | Threat Level | Mitigation Priority |
|---|---|---|
| Developer Laptops | Critical | Highest |
| CI/CD Pipelines | Critical | Highest |
| GitHub Repos | High | High |
| AI Coding Tools | High | High |
| SSH Agents | High | High |
Dev environments primary targets.
FAQ
19 typosquatted packages targeting Node.js/AI tools.
Package import activates payload while maintaining normal functionality.
Claude Code, Cursor, VS Code via rogue MCP server injection.
Stolen credentials modify package.json/lockfiles/workflows via GitHub API or SSH.
Cloudflare Workers, HTTPS endpoints, DNS tunneling fallback.
Disabled dead switch wipes home directory if propagation fails.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages