Identity Cyber Scores: Key Metric for Cyber Insurance 2026

Identity cyber scores now shape cyber insurance rates in 2026. Insurers use them to measure identity security risks like password strength and MFA coverage. One in three attacks starts with stolen employee credentials, making these scores vital for lower premiums.
Cyber insurance demand grows as breach costs hit $4.4 million on average. UK coverage rose from 37% to 45% in two years. Insurers tighten rules due to more claims. They focus on identity controls to predict breach impact.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Weak identities let attackers escalate fast. Strong password hygiene and privilege limits cut risk. Insurers reward proof of active management over basic tools. Regular audits show maturity.
Why Identity Drives Underwriting
Credential theft tops attack methods. Attackers grab passwords, then spread. Insurers ask: How fast can one bad account become admin access? Poor answers mean higher costs.
Legacy protocols like NTLM linger. They bypass modern checks. Dormant accounts offer quiet entry points. Shared admin creds hide who did what.
MFA gaps hurt most. Cases like Hamilton city’s $18M denial show full coverage matters. Partial MFA leaves bypass paths open.
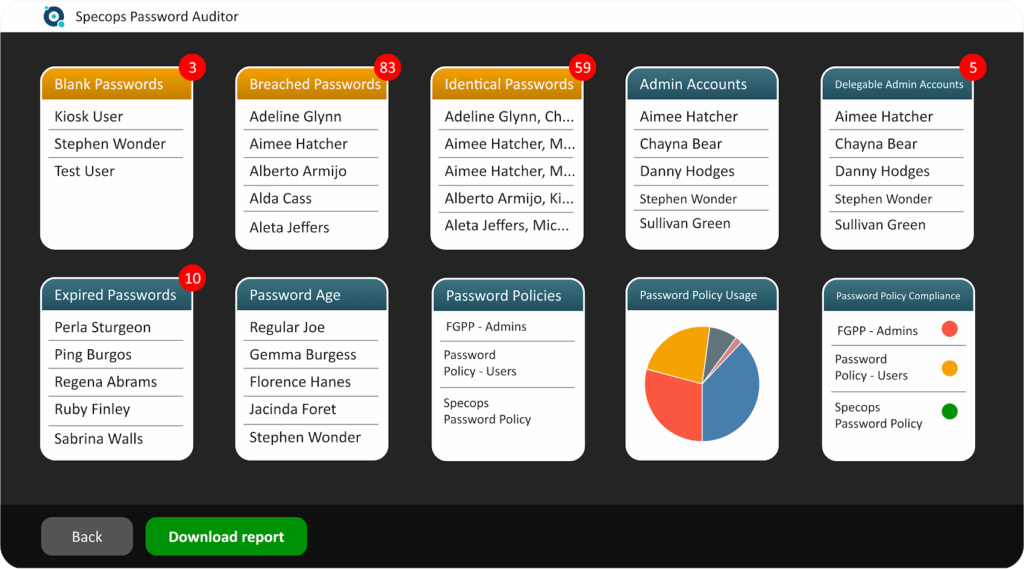
Core Identity Risks
Insurers check these factors closely.
| Risk Area | Common Issues | Impact on Scores |
|---|---|---|
| Password Hygiene | Reuse, never-expire, shared creds | High; easy theft and spread |
| Privileged Access | Over-permissioned admins, service accounts | Critical; fast escalation |
| MFA Coverage | Gaps in VPN, email, legacy auth | Major; reliable bypasses |
| Dormant Accounts | Stale users with old rights | Medium; hidden footholds |
Tools like password auditors spot these fast.
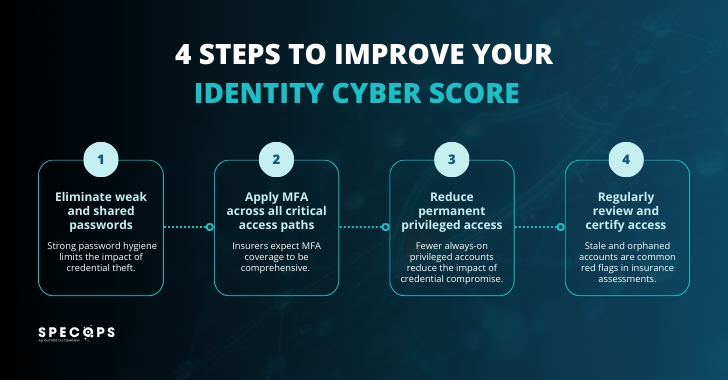
Steps to Boost Scores
Follow these to improve ratings and terms.
- Enforce strong password rules. Ban reuse on admin accounts.
- Roll out MFA everywhere: VPN, cloud, email, privileges.
- Cut permanent admin rights. Use just-in-time access.
- Audit accounts quarterly. Kill stale or orphaned ones.
Proactive fixes signal low risk to underwriters.
Official Guidance
IBM reports 1/3 attacks via creds. Focus on hygiene cuts costs.
Specops notes: “Evidence of management beats tools alone.”
FAQ
Metrics rating password strength, MFA use, and privilege controls for insurance risk.
33% attacks use stolen creds. Strong identity slows breaches.
Audit passwords, full MFA, limit privileges, review access often.
No coverage on legacy auth, service accounts, or VPN.
Yes. Proof of fixes shows maturity and cuts risk.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages