How To Access The Dark Web - Complete Guide

You have probably seen the terms TOR, Dark Web, and Deep Web while surfing the Internet. In this article, you will learn all about the Dark Web and the Deep Web, and the differences between them. You will also learn how to use TOR to browse the Deep (Dark Web).

World Wide Web Size, a site that is credited with developing a statistical method for tracking the number of web pages indexed by the popular search engines, estimates the indexed web to contain at least 4.5 billion pages by 4/28/2017.
Internet Live Stats, the international Real-Time Statistics Projects website estimates the number of websites to be slightly above 1.18 billion on the same date. If you think the figures are huge, then, you are in for a big shock as that constitutes only a bare fraction of the World Wide Web.
WEB PAGES INDEXED BY GOOGLE, YAHOO,BING, OR OTHER SEARCH ENGINES ARE ONLY A TINY FRACTION OF THE WORLD WIDE WEB
The Deep Web that exists beneath the surface and cannot be indexed by conventional search engines contains five hundred times more content than the surface web.
This guide will explain in detail the Dark Web and how it differs from the Deep Web and also walk you through the requisite steps of how to access the Dark Web safely.
What is the Deep Web?
The Deep Web or Hidden Web is that part of the World Wide Web that cannot be indexed by traditional search engines such as Google, Yahoo, or Bing.
What is the difference between the Deep Web and the Dark Web?
While the Deep Web refers to websites not indexed by traditional search engines, the Dark Web is the most secretive section in the deep web that contains a collection of websites that exist on an encrypted network.
Most sites on the Dark Web use the Tor encryption tool to hide their identity. Tor is popular with websites in the dark web for its ability to bounce both the user’s IP address and the website’s IP address through layers of encryption to make each of them appear to be at another IP address on the Tor network.
That way, you can spoof your location to appear as if you’re in a different location and not your real location contributing to your anonymity.
Who is using the Dark Web?
Contrary to the assumption by many that the dark web is a reserve for drug trafficking, child pornography, hitmen, and everything illegal, the dark web is also used for good by journalists, scientists, and government agencies.
It is also a lifeline for those in dangerous and oppressive regimes. Simply put, the dark web is a place for those who seek to stay anonymous and keep their communications and transactions away from the surface web.
Bitcoin is the currency of the Dark Web
Bitcoin can be defined as a technology that creates digital currency using cryptographic code. Transactions in the dark web are made possible by virtual currency.
The sender transmits their bitcoin code via a ledger called âblock chainâ to the recipient. Though Bitcoin is not perfectly anonymous, with proper use, it can facilitate online transactions anonymously without revealing the identity of the parties. Bitcoin is widely employed in Dark Web transactions because of its anonymity and also because banks and governments do not control it.
How do I browse the Dark Web?
As discussed above, the dark web contains both interesting and terrible content. If you are planning to access the dark web, you had better take the following precautions.
- The dark web can be safe if you play your cards right. You need to use the Tor browser bundle as it is pre-configured to protect you against privacy threats.
- If you are going to register on any site on the dark web, don’t use your real email, a username that you’ve used before or intend to use in the future as well as your real name.
- It is advisable to seek reviews of a site to ensure it has a good reputation before you engage in any commercial transactions on the dark web. We advise you use Bitcoin, but even then, ensure that the site provides an escrow service.
- Avoid downloading anything while on the dark web unless you are completely sure of what you are doing. Where you intend to download any content, you had better use a competent virus tool such as Virus Total to scan the content.
- Connecting to Tor via a bridge might be helpful if you are in a location where connecting to Tor might cause problems for you. You can access valuable instructions for acquiring bridge addresses and how to configure your software at Tor Project: Bridges.
- Finally, we advise you to exercise good judgment while surfing the dark web. Honing your own sense of possibility and perspective will go a long way to protecting your privacy than any defensive software.
How to access the Dark Web using Tor?
Though there are several ways to access the dark web, Tor is the most widely used method. Other methods are the IP2 and Freenet.
The US military initially developed Tor which later on became open source and publicly funded. The Tor browser is available for use on Windows, Mac, OSX, or Linux without the need for installing any software.
Tor can also run off a USB flash drive, is portable, and comes with a preconfigured browser to protect your anonymity.
Installation instructions
- Login on the Tor Projects website to access direct download links.
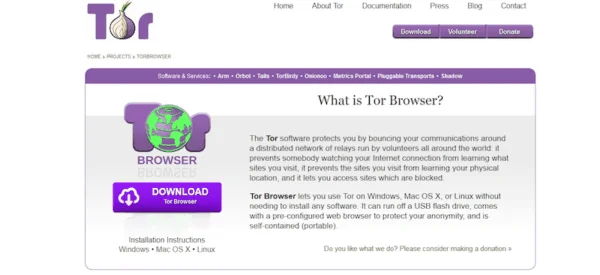
- Download the file for your preferred language and operating system, save the file anywhere, and then double-click on it.
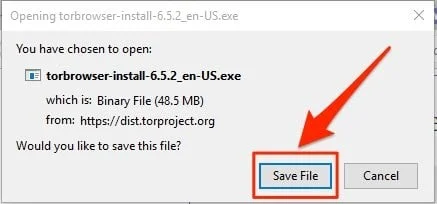
- Click Run, choose the language of the installer, and then click OK.
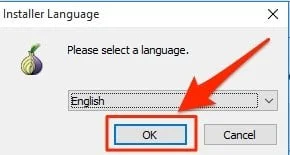
- You need at least 140MB of free disk space in the selected location. Click Install.
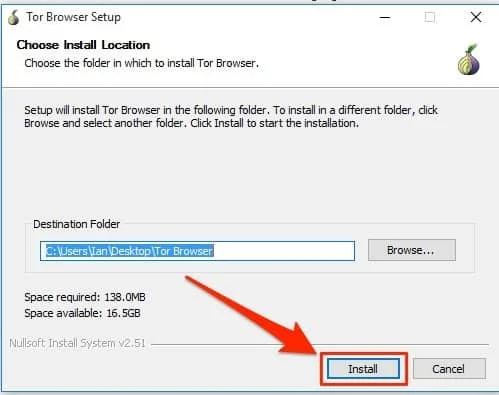
- The installer takes a few minutes to complete. Then click Finish to launch the Tor Browsers wizard.
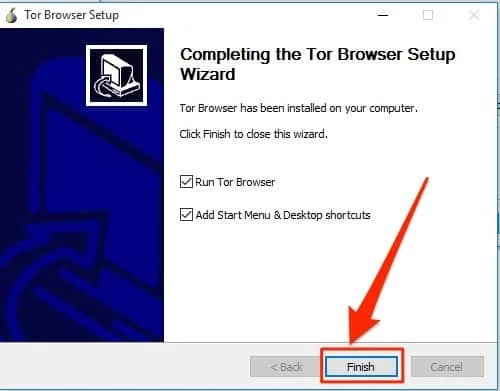
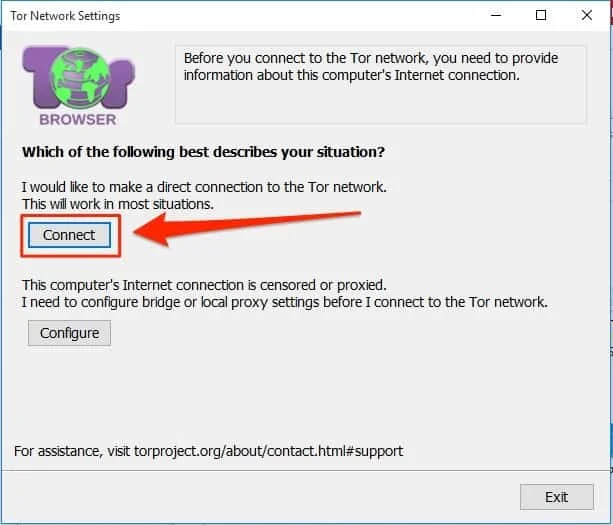
- Finally, click Connect in the wizard.
An alternative method of launching the Tor browser is to go to the folder Tor Browser found at the location you saved the bundle and double click the start Tor Browser application. The Tor Browser will automatically open.
Only the web pages visited via the Tor Browser will be sent through Tor. Other Web Browsers such as Firefox, or Chrome will not be affected.
How to access the .onion domain?
The .onion domains are the websites that belong to the area of the Internet referred to as the Dark Web. The fact is that, no matter how great the internet is, it is very, very unsafe for regular users. Especially for those who do not have skill in protecting themselves online.
However, the awareness of this has finally reached the users, and they are now looking for means of protection.
One of the best ways for them to protect themselves would include using special, secure, and anonymous networks. Tor network is the perfect example of this, and today, we are going to talk about it, and also about its .onion domains. So, let us start.
What are Tor Network and .onion domains?
Tor network is a special private network that works by making its users anonymous and therefore protected online. Tor is short for The Onion Router, and when you connect to it, all of your online actions are going through the Tor network.
The data will go from one relay to another on the Tor network, and it will do it until it loses any connection to you. It will only then use an exit node to leave the network and send you the browsing data. Even the site that you are accessing through Tor will see the address of the exit node, instead of your own.
As you can see, this is a very safe way of browsing the web, if you wish to remain anonymous. However, it is not the ultimate safety, and that last part of the process can still remain under surveillance. Also, do note that Tor doesn’t encrypt any part of your traffic. It only makes it impossible for anyone to follow and connect it to you.

Another great use for the Tor network is that it allows you to access the so-called .onion websites. These are the sites that end with .onion and you can’t access them through normal browsers. They are only accessible through Tor, and they are a part of the deep web.
Basically, these are hidden services on the internet. You can only access them through Tor, which means that they are inside the Tor network. Thanks to that, nobody can see what you are doing in there, and they definitely can’t make any connection between that content and you.
Many sites have their .onion version, but the majority of these sites contain some very nasty things. Some of them may even be illegal, while the majority are some kind of scams and tricks. This is a dangerous, lawless area, and you should avoid navigating through it if you don’t know what you are doing.
Instead, use the Tor network for accessing specific sites. If you know any of them, you can access them safely through Tor but try not to wander off. Especially since there is no map of the Tor network. Instead, you can access other sites by following external links on some other site. Search engines don’t work here, and it is an entirely new world on the internet. One that you should not take lightly.
As mentioned, many sites have a .onion version. Even Facebook is one of them, and this is because those sites might suffer from restrictions and censorship in certain countries. By providing a .onion version of their service, they are allowing access to users from countries that block Facebook.
You should only use Tor when you have to. For all the good you get by using it, there are also some of the bad, and in this case, it is about the side effect of the Tor network. We explained how your data travels from relay to relay while you use Tor, and that will make everything perfectly safe. However, the entire process takes its toll, and it will slow your browsing speed. A lot.
So much, in fact, that you can’t use this method for downloading anything, or even for watching videos. Regular browsing is fine, but when it comes to the rest of the internet services, you just won’t have enough speed to access them as you usually would. This is mostly why people don’t use Tor all the time.
How to use the Tor Network?
In order to make using the Tor network easier, the special Tor browser was developed. This is basically a Firefox browser that went through a lot of modification. Thanks to that, it can now access the Tor network and make the entire process a lot easier. You can download it for free from the Tor project’s website, and it works on Mac, Windows, and even Linux.
If you would rather use a tablet or an Android phone, you can go to your Google Play Store and download an Orbot proxy app. Alternatively, there is also an Orfox browser that you can use on these devices as well. Unfortunately for iOS users, there are no apps that will allow access to .onion sites. Your only remaining option is to use the Tor browser for Mac.
Now, upon downloading the Tor browser, you should install it, and the process is pretty much the same as for any other program or browser. If you encounter difficulties, there are a lot of tutorials on YouTube that you can use.
When you install it and launch it, all you need to do is type the .onion address in the browser. It is just like typing a regular address to a regular browser, only with two differences. First, the names of the websites are often complex and they look like a random string of numbers and letters. And second, they all end with .onion, instead of .com.
For example, the .onion URL version of Facebook looks like this: facebookcorewww.onion.
As you can see, it ends with .onion. The rest of the address is pretty close to the traditional Facebook address, which is mostly because of Facebook’s popularity. The whole point of this version of Facebook is to allow easy access to those who usually don’t have it.
On the other hand, the Tor version of the search engine DuckDuckGo looks like this: 3g2upl4pq6kufc4m.onion.
This is a lot more Tor-like, and it is a proper example of how the majority of these addresses actually look like.
These addresses will load normally in the Tor browser. However, they won’t work on Chrome, regular Firefox, Safari, or some other browser that you might use.
How to access .onion domains without Tor?
These sites and the entire Tor network are also accessible through special proxies that can connect to this network. However, using them is a very bad idea. If you try to access these sites through proxies instead of Tor browser or Android app, you will lose the usual anonymity.
That anonymity is pretty much the entire point, and by accessing these sites via proxy, you won’t have it anymore. Someone who is monitoring your connection will instantly see what you are up to, where do you go, and what do you do. The same goes for your ISP, which will get all the information and record it.
There are several Tor proxies that will let you do this. However, keep in mind that you must only use them as the last resource. Also, remember that you won’t stay hidden if you do so. These are the ones that you can use to access Tor network.
What are the alternatives to accessing the Dark Web?
1. onion.to

This is the first proxy that we can recommend for accessing the Tor network. All you need to do is add “.to” to the link of the .onion website and it will take you there. This way, you can even access these sites through the regular browser.
2. Onion.nu
Onion.nu works pretty much the same as our previous entry. Simply add .nu at the end of a .onion link, and it will take you to the website that you wish to visit.
3. Onion.cab
Onion.cab is a very good option as well, as far as proxies go. You can go to the onion.cab site directly via your regular browser, and get access to the Tor network.
If not, you can simply do the same as in our previous entries, and just add .cab to the end of a .onion link.
4. Tor2Web.Org
This proxy is also a potential candidate for accessing the Tor network, although we should point out that it is relatively unstable. As such, you should use it with caution, and probably only as the last resort. You can still access the Tor network through it, but it is not very safe.
Even some sites like Facebook think so, and they will actually warn you that you should not do it if you try to access their .onion version.
5. I2P
I2P is an anonymous overlay network that can only be used to access hidden websites and services that are unique to the I2P network. You cannot use I2P to access .onion sites because it is a separate network from Tor. I2P has its own hidden sites referred to as deepsites.
I2P aims at protecting communication monitoring by third parties and from dragnet surveillance. Among its users are oppressed people, journalists, and whistleblowers as well as the average person looking to secure his privacy.
I2P makes privacy attacks harder to mount. The I2P is available on Desktops, Android phones, and embedded systems (like the Raspberry Pi)
What do you get with I2P?
- Emails: You get an integrated plugging for serverless emails
- Anonymous websites and gateways both to and from the public internet
- Availability of blogging and Syndie plugins for Blogging and Forums
- Web hosting from an integrated anonymous web server
- Instant messaging as well as IRC client
- File sharing is available through the built-in BitTorrent as ED2K and Gnutella clients.
I2P is much faster than Tor. And the peer-to-peer routing structure is more advanced. I2P does not depend on a trusted directory to get route information. Another advantage of I2P is that it uses one-way tunnels so that an eavesdropper can only capture inbound or outbound traffic but not both.
Setting up I2P is involving and requires more configuration on the userâs part as contrasted with Tor. After downloading I2P, you must configure individual applications separately to work with I2P. In the case of a web browser, you have to set up your browser’s proxy settings to use the correct port.
6. Freenet
Freenet is a self-contained peer-to-peer network that helps to provide censorship-resistant communication as well as publishing. Freenet enables users to connect to the dark web and only uses content uploaded to the Freenet.
Unlike Tor and I2P, a server is not needed to host content, and the content that you upload on Freenet stays there permanently.
Freenet allows connection to the darknet mode and the OpenNet mode. In darknet mode, Freenet will allow you to connect and share content with only your friends on the network. In the OpenNet mode, Freenet automatically assigns peers on the network.
Freenet is easy to configure, and you only need to download, install and run. Freenet enables users to browse websites, publish files, and post on forums within the Freenet network with high privacy protection.
Other options to browse the Deep Web
As we explained, Google and other powerful search engines can’t crawl and index the data on the Dark Web. However, there are specialized deep web search engines that crawl over the Tor network successfully and bring results to your regular browser.
These are additional best deep and dark web user-friendly search engines:
- Onion.link
- NotEvil
- DuckDuckGo
- The WWW Virtual Library
- Surfwax
The deep web search engines communicate to the service through Tor and resolve the .onion links thereby delivering their output to your surface web browser.
What are the best VPNs to access the Dark Web with Tor?
If you are planning to access the dark web, you should understand that Tor alone will not provide the highest levels of protection. Tor is known to anonymize the origin of your traffic and encrypt everything inside the Tor network, but not your traffic between the Tor network and its final destination.
Because of this and other flaws, it is advisable to use another end-to-end encryption service preferably a VPN service to achieve maximum anonymity.
Using Tor in combination with a VPN service can provide an extra layer of security as it mitigates the disadvantages of using either technology exclusively. However, not any other VPN service can provide the required level of anonymity protection.
And so, here are some of the features you should look out for in the best VPN when using Tor to access the dark web:
- The best VPN service should be one that allows subscription payments through mixed Bitcoins. Any money trail limits anonymity.
- The VPN should have a Multihop routing feature. The feature makes traffic analysis attacks difficult as the public IP you get is different that the IP of the gateway to which you are connecting.
- The VPN service must not keep logs. The goodness for not keeping logs is that if the VPN service is confronted by law enforcement to surrender the logs, they won’t have any to give.
- The best VPN for accessing the dark web should have a client with VPN kills switch and DNS leak protection.
We found the following VPN services to offer the best protection when using Tor to access the dark web:
1. CyberGhost
With CyberGhost you can surf the deep web avoiding any risk. This VPN is among the big player in the security industry.
The company is based in Romania and thanks to local privacy laws it doesn’t keep any log of your activity.
CyberGhost provides its users with strong military grade 256-bit AES encryption, a Kill switch, and port forward secrecy.
To be noted that CyberGhost has some of the most economical plans on the market without compromising security.
2. NordVPN
NordVPN is a service that is based in Panama. The location is excellent for a VPN service as rules there are relaxed. They donât log user activity and accept Bitcoin payments.
NordVPN is designed to access the dark web. In fact, among the many features, it has unique options such as double VPN and Tor over VPN.
The features make NordVPN viable for accessing the dark web as your IP address can’t find out that you are using Tor.
3. ExpressVPN

Based in the Virgin Islands, ExpressVPN is not affected by the Data Retention Laws. They do not keep logs and accept Bitcoin payments.
ExpressVPN provides DNS leak protection that is helpful for protecting your privacy while you surf the dark web.
You can find out more about the service by checking out our in-depth review of ExpressVPN.
4. IPVanish
Though based in the United States, IPVanish is a tier-1 VPN service with absolute control over all its VPN servers.
They keep no logs so that even if they are requested by the strength of a Court Order to surrender a user’s records, they will have none.
IPVanish accepts Bitcoin payments and also allows P2P as a user activity.
What is the Silk Road?
Silk Road was an anonymous underground marketplace for the exchange of any type of goods from drugs such as LSD, Cocaine, and high-grade MDMA to forged documents and even hit men.
The dark market was a great success and generated about $1.2 billion dollars with more than a million users worldwide, thanks to a perfect innovative combination of Tor and Bitcoin.
Silk Road was a massive dark market with sophistication and ease of use. It offered more than 13,000 items with fast and free shipping, call it the Amazon and eBay of the dark marketplace.
Tor made it possible for Silk Road users to transact anonymously as all communication through Tor is strongly encrypted. Bitcoin, on the other hand, ensured through its anonymized transactions that even the police would get nowhere with their investigations.
Silk Road was the creature of Ross William Ulbricht. He used a pseudonym Dread Pirate Roberts. Ulbricht had always wanted to create an online black market that utilized a combination of Tor and Bitcoin to evade law enforcement. The vendors of Silk Road were sought out using encryption keys to verify their identities.
The FBI arrested Ulbricht and shut down what they referred to as the most sophisticated and extensive criminal market on the internet. However, the demise of Silk Road did little to hamper the sale of drugs on the Dark Net. In fact, Silk Road was back and interestingly, run by someone calling themselves Dread Pirates Roberts.
Conclusion
The Deep Web as we have seen is an invisible part of the World Wide Web. To say that the dark web is a place of illegal activities only amounts to throwing the baby with the bath water.
After the Assange Snowden revelations and the understanding of NSA’s surveillance programs, the public is fearing for their privacy. It is becoming a daily routine activity to anonymize our communication and the deep web is becoming an option for securing sensitive communication.
The dark web will continue to exist for the bad and the good. We have given you valuable information on the dark web and how to access it safely. We hope you will protect your privacy accordingly should you decide to access the dark web.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages