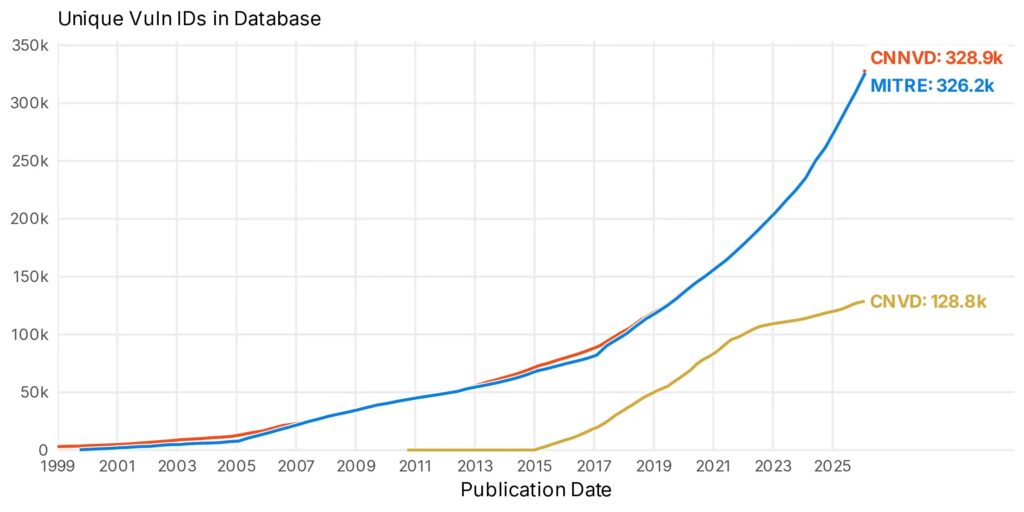
China’s CNVD CNNVD Databases Create Vulnerability Disclosure Gaps

China maintains two national vulnerability databases, CNVD and CNNVD, that reveal security flaws months before Western databases. These systems create informational asymmetry exploited by threat actors. Enterprises relying solely on CVE/NVD remain blind to “Red Vulns” during critical exposure windows.
Bitsight analysis compared publication timestamps across ecosystems. CNNVD largely mirrors MITRE CVE entries. CNVD publishes unique vulnerabilities with independent timelines and deliberate disclosure delays.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Strategic latency turns vulnerability intelligence into national security assets rather than public goods. Attackers weaponize flaws like OneDrive DLL hijacking before global patches deploy.
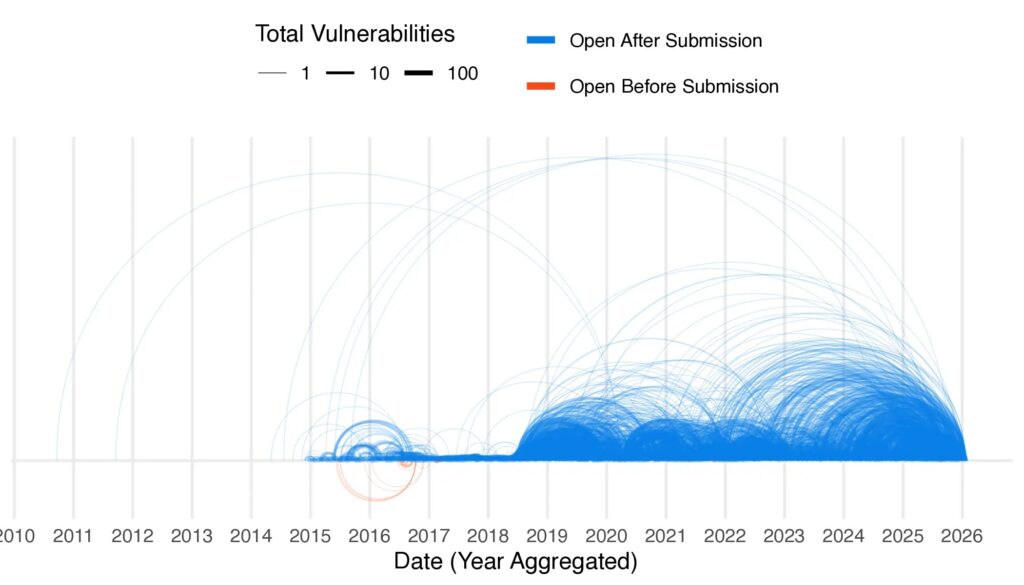
High-severity vulnerabilities appear in CNVD while absent from NVD. Disclosure delays exceed weeks for sensitive entries. Global defenders lack IOCs during active exploitation phases.
CNVD maintains a shadow inventory unmapped to CVE numbers. Severity ratings differ across borders. Enterprise security teams must monitor both databases for complete coverage.
Database Comparison Matrix
| Database | Operator | CVE Alignment | Disclosure Speed | Unique Entries |
|---|---|---|---|---|
| CNVD | CNCERT/CC | Partial | Delayed (weeks+) | High |
| CNNVD | NSFOCUS | Strong | Mirrors CVE | Low |
| NVD | NIST | Global standard | 24-72 hours | None |
| CVE | MITRE | Master list | Vendor submission | Master IDs |
CNVD growth matches global standards but prioritizes national security over rapid disclosure.
Disclosure Delay Patterns
Strategic latency arcs:
- High/Critical CVEs held back >30 days
- Zero-day indicators published post-exploitation
- CNVD “event-based” entries precede CVE
- OneDrive DLL hijacking cataloged pre-CVE equivalent
Key example:
CNVD-2024-xxxxx: OneDrive DLL Hijacking (High)
Published months before comparable CVE
Enabled targeted attacks during patch gap
Bitsight identified systematic patterns where submission-to-publication exceeds one week.
Vulnerability Timeline Examples
| CVE/ID | Name | CNVD Date | NVD Date | Delay | Severity |
|---|---|---|---|---|---|
| CVE-2024-33698 | Generic | Early 2024 | Mid 2024 | 4 months | High |
| CNVD-2024-xxxxx | OneDrive DLL | Q1 2024 | No CVE | N/A | High |
| CNVD-202-35587 | Bitcoin DoS | 2022 | No CVE | N/A | Medium |
| CVE-2021-40444 | MSHTML RCE | Reference | Reference | Baseline | Critical |
CNVD entries often lack direct CVE mapping, creating shadow inventory.
Attack Implications
Weaponization window:
- Chinese actors exploit during disclosure blackout
- Western EDR/SIEM blind to CNVD-tracked IOCs
- Patch cycles lag vulnerability awareness
- Persistence established pre-detection
OneDrive DLL hijacking case:1. CNVD publishes flaw details
2. State actors develop exploit
3. Western vendors unaware
4. Months pass before CVE/NVD sync
5. Targeted intrusions complete
Severity Distribution Differences
Risk rating divergence:CVE: CVSS v3.1 standardized
CNVD: National priority scoring
Result: Medium CNVD = Critical CVE
Organizations misprioritize when using single-source intelligence.
Intelligence Requirements
Multi-source monitoring:NVD + CNVD + CNNVD + CVE daily sync
Chinese-language vuln feeds
Event-based CNVD entries
Delay arc tracking
Enterprise actions:
- Automate CNVD/CNNVD API polling
- Cross-reference CVE mappings
- Prioritize CNVD High/Critical entries
- Track unmapped shadow inventory
Geopolitical Risk Factors
National security divergence:
- CNVD serves Chinese defense priorities
- Disclosure serves strategic objectives
- Zero-days weaponized during blackout
- Global patch cycles irrelevant
Supply chain impact:Western software dominates CNVD
Microsoft, Adobe, Oracle heavily tracked
Chinese vendors receive preferential treatment
Detection Engineering Challenges
Signature gaps:CNVD IOCs absent from Western platforms
YARA/Sigma rules lag publication
SIEM content misses shadow inventory
Threat hunting:Query CNVD by vendor/product
Monitor delay arcs >14 days
Track unmapped High/Critical entries
Validate against NVD/CVE sync
Strategic Recommendations
Immediate:Subscribe CNVD English RSS
API integration vulnerability scanners
Daily delta scans both databases
Prioritize CNVD-only High entries
Long-term:Multi-lingual threat intelligence
Automated CVE-CNVD correlation
Delay arc alerting
Shadow inventory tracking
FAQ
CNVD (unique entries, delayed disclosure) and CNNVD (CVE mirror).
CNVD delays high-severity entries weeks/months. Creates exploitation windows absent from NVD/CVE.
CNVD-tracked flaws weaponized before Western awareness. Example: OneDrive DLL hijacking.
Yes. Contains shadow inventory absent from CVE/NVD. Essential for complete coverage.
Microsoft, Adobe, Oracle heavily tracked in CNVD before CVE publication.
State actors establish persistence during intelligence blackout periods.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages