Hacking Groups Target OpenClaw AI Framework in Mass Attacks

Multiple hacking groups now exploit OpenClaw instances to steal API keys and drop malware. Over 30,000 compromised setups spread stealers via Telegram channels. The open-source AI agent gained fame in late January 2026 but fell to attacks within 72 hours.
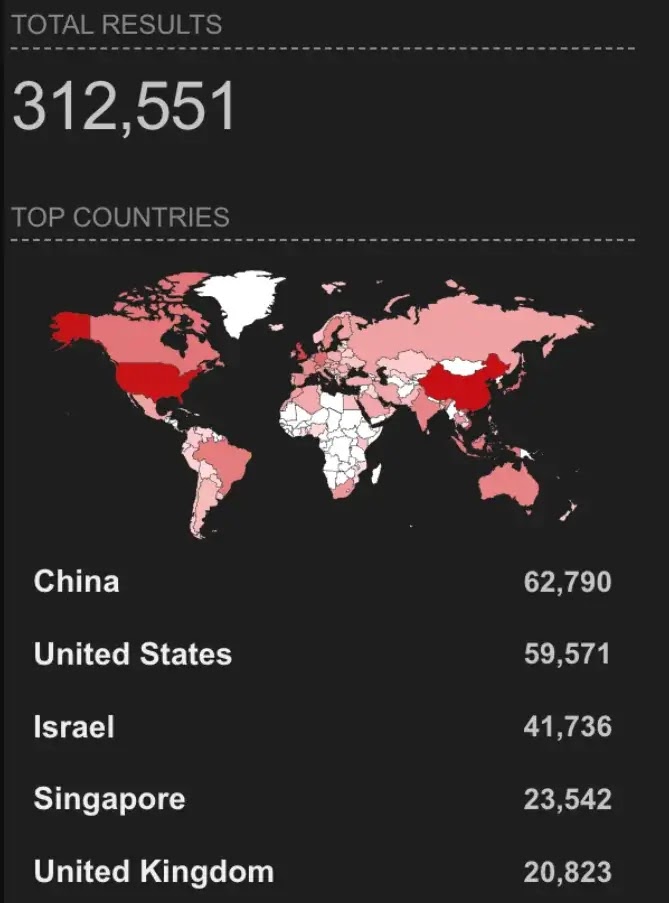
OpenClaw gives agents full system access, memory, and service links. This design drew threat actors fast. Key flaws include CVE-2026-25253 for remote code execution plus supply chain tricks. Default port 18789 stays wide open on many installs. Shodan found 312,000+ exposed units by February 18.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Attackers hit admin panels with no auth checks. Misconfigured proxies treat outside traffic as local. Full control follows. Honeypots catch probes in minutes.
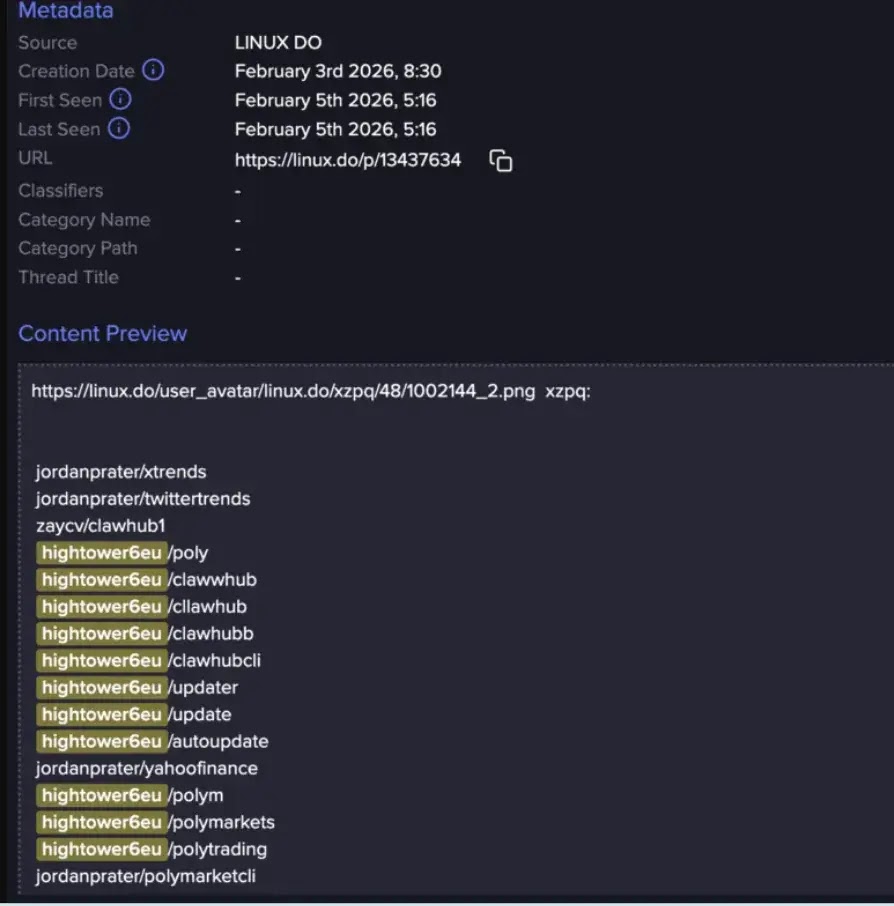
ClawHavoc Campaign Details
ClawHavoc kicked off January 29 under “Hightower6eu” on GitHub. Fake setup scripts pushed Atomic Stealer for macOS and Windows keyloggers. Victims thought they grabbed crypto tools.
Malware pulls browser data, cloud creds, and Keychain files. ClickFix tricks users into self-infection via guides. Enterprise lateral moves tap OpenClaw memory.
Second wave hit ClawHub marketplace. No code review let backdoored skills run shell commands. OAuth tokens and passwords flow out live.
Key Vulnerabilities
| CVE ID | CVSS Score | Type | Impact |
|---|---|---|---|
| CVE-2026-25253 | 8.8 | RCE via WebSocket | Full gateway control |
| CVE-2026-26322 | 7.6 | SSRF | Internal access pivot |
| CVE-2026-26319 | 7.5 | Missing auth | Webhook takeover |
Patches rolled for most by version 2026.1.29. Exposed instances topped 549 with breach signs.
Attack Vectors
- Exposed localhost via bad proxies grants admin rights.
- Malicious links leak auth tokens through browser pivots.
- Poisoned skills execute remotes sans checks.
- No auth on default port invites scans.
Flare advisory: “Secure API keys. Isolate workloads now.”
Protection Steps
- Bind services to localhost only. Block port 18789 public.
- Add auth to all admin interfaces.
- Vet ClawHub skills from trusted sources.
- Scan for malware from fake setups.
FAQ
Open-source AI agent framework from Peter Steinberger, now OpenAI.
Over 30,000 confirmed. 312,000+ exposed via Shodan.
RCE letting attackers run commands via malicious links. Patched in 2026.1.29.
Fake GitHub scripts, poisoned ClawHub skills, exposed panels.
API keys, OAuth tokens, chats, passwords, browser creds.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages