How Does VPN Encryption Work? [All You Need To Know]

Are you concerned about your online privacy and security? Probably, you’ve heard that VPN encryption helps with that.
But, the issue is, you want to know exactly how VPN encryption works.
If that’s you, you’re in the right place. Soon, you’ll understand the nitty-gritty of VPN encryption.New to VPNs? Start with our step-by-step guide on how to set up a VPN before diving into encryption details.
First, there are multiple types of encryption out there, and we’ll explain everything they do and how they’re different.
And if you don’t know precisely if you need encryption, we’ve also outlined all its essential benefits for the day-to-day internet user.
What is VPN encryption?
Encryption is a technique used to transform information from its original form, called plaintext, into an encrypted form, known as ciphertext.
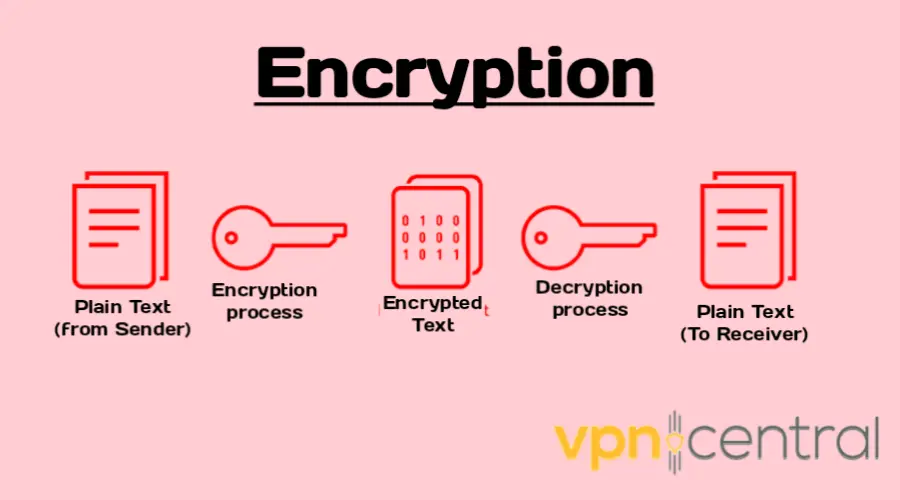
It aims to protect the confidentiality and integrity of your online information.
For example, when you browse a website, your device sends a request to the server asking for the page content, which is then transmitted back to your device.
Encryption ensures that only authorized individuals with the appropriate decryption key can decode the ciphertext and access the original plaintext.
Note that an encryption/decryption key is a sequence of characters (usually numbers and letters) used to transform plaintext into ciphertext (encryption) and vice versa (decryption).
In other words, it’s a code that enables data to be encrypted so that it can only be read by someone with the corresponding key to decrypt it.
How does VPN encryption work?
The encryption process is like a lock and key. Your internet traffic is the lock, and the VPN server is the key.
- When you connect to the VPN, your device and the server agree on a secret key that they will use to encrypt and decrypt your traffic.
- Once your traffic is encrypted, it’s sent through the secure tunnel to the VPN server.
- The server decrypts your traffic and sends it out to the internet, and any data sent back to you is encrypted before being sent back through the same tunnel.
This key is unique to your connection and changes every time you connect to the VPN, making it almost impossible for anyone to crack.
When data is encrypted using a key, it undergoes a complex mathematical transformation that makes it appear as gibberish to anyone who doesn’t have the key.
This ensures that the data remains confidential and secure, even if it’s intercepted by a third party or cybercriminals during transmission or storage.
With encryption, you can rest assured that your online activities are private and secure.
VPN encryption characteristics
Although VPN encryption has a simple definition anyone can understand, some other complex parts and characteristics make the whole process successful.
In the following section, we’ll define some of them. So, let’s get started.
VPN encryption key length
You probably know your VPN has 256-bit or 128-bit encryption, but do you know what those numbers are and how they’re relevant for security?
Basically, they tell how long your encryption keys are.
The length of the encryption key refers to the number of bits used in the key, with longer keys providing greater security.
A longer key means more possible combinations, making it more difficult for an attacker to crack the encryption.
For example, a key length of 128 bits means that there are 2^128 possible combinations, which is an astronomically large number.
In contrast, a key length of 64 bits would have only 2^64 possible combinations, which is significantly easier to crack.
Therefore, key length is a critical aspect of VPN encryption that can significantly impact the security of your data.
Symmetric vs asymmetric encryption
There are two ways in which encryption uses secret keys: symmetric and asymmetric encryption.
Here’s how both VPN encryption types work and how they’re different:
Symmetric encryption
The symmetric encryption algorithm involves using a single secret key to encrypt and decrypt the information.
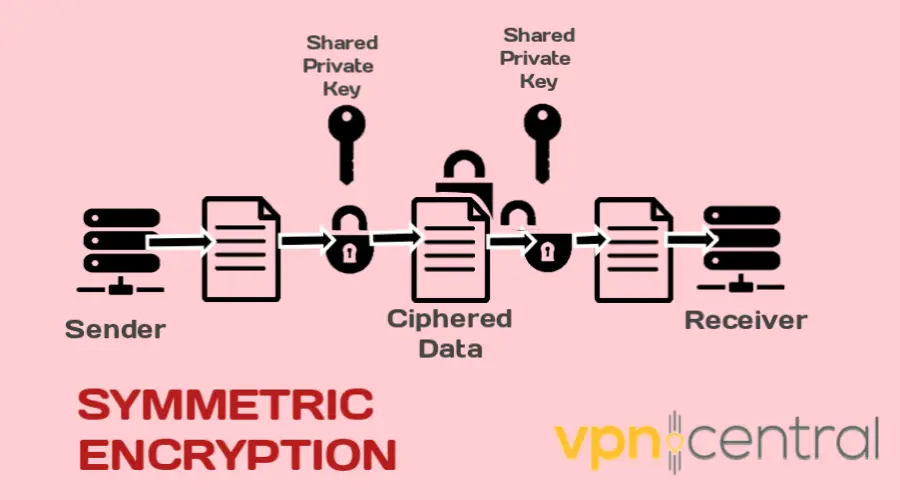
The same key is used for both processes, which makes it faster and more efficient than asymmetric encryption.
However, the downside is that both the sender and the recipient must have access to the same secret key, which can be challenging to manage for large groups of people.
Some examples of symmetric encryption algorithms VPNs use include AES, TLS/SSL, and Triple DES.
Asymmetric encryption
On the other hand, asymmetric encryption involves using two different keys for encryption and decryption.
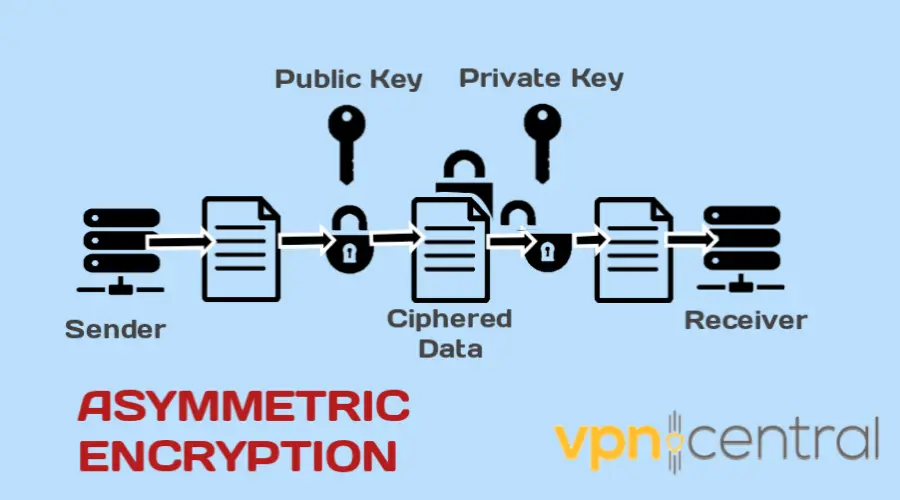
These keys are mathematically related but not identical, and they are known as the public key and the private key.
The public key is freely available to anyone, while the owner keeps the private key secret.
When someone wants to send a message, they encrypt it using the recipient’s public key, and the recipient can only decrypt the message using their private key.
This approach provides a higher level of security than symmetric encryption, as only the private key owner can decrypt the message.
However, it is slower and more resource-intensive than symmetric encryption.
Some examples of asymmetric encryption algorithms VPNs use include RSA and Diffie–Hellman key exchange.
For day-to-day examples of encrypted browsing and data protection, check everyday VPN security practices in 2025.
Different types of encryption algorithms
An encryption algorithm is a method an encryption key uses to alter data.
It does it in such a way that even though encrypted data will appear random, it can be converted back into plaintext using the decryption key.
There are a lot of different encryption algorithms, but we outlined the most popular ones that are used by VPNs and explained how they work.
1. AES
The Advanced Encryption Standard (AES) is a widely trusted encryption algorithm by the United States government, military and other organizations.
It uses 128-bit, 192-bit, or 256-bit keys to encrypt data and is considered invulnerable to all attacks, especially when the key is large enough.
AES is fast and efficient and is expected to become the standard for encrypting data in the private sector.
2. Triple DES
Triple DES is a symmetric encryption algorithm developed as a successor to the original Data Encryption Standard (DES).
It applies the DES algorithm three times to each data block. However, most VPNs no longer use it in favor of more secure algorithms like AES-256.
3. Blowfish
Blowfish is a symmetric encryption algorithm that was designed to replace DES. It breaks messages into 64-bit blocks and encrypts them individually.
Blowfish is faster than 3DES and more flexible, and the OpenVPN encryption protocol uses it as a default encryption cipher.
As a result, it is in use by some VPN providers.
4. Twofish
Twofish is a successor to Blowfish, a license-free symmetric encryption algorithm that can decrypt 128-bit data blocks.
It always encrypts data in 16 rounds, regardless of the key size.
Although this encryption cipher is considered secure, it is no longer in use due to its slower speeds.
5. Rivest-Shamir-Adleman (RSA)
RSA is an asymmetric encryption algorithm based on factorizing two large prime numbers.
Only users with knowledge of these two numbers can decode the message successfully. Digital signatures commonly use RSA, but it can be slow when encrypting large volumes of data.
Although it’s one of the earliest public-key cryptography systems, it remains popular today.
RSA has various purposes, such as establishing VPN connections and encrypting emails.
Common VPN encryption protocols
VPNs use various security protocols to establish a secure connection between your device and the server.
Each VPN protocol has unique features that determine how the tunnel is established.
Choosing a VPN protocol is determined by various factors, such as your device and online activities.
While some VPN protocols prioritize access speed, others focus on encrypting data. Here are some of the most popular options:
1. OpenVPN: popular and secure option
One of the most popular VPN protocols is OpenVPN. It is open-source, which means anyone can inspect the code for vulnerabilities. Plus, it can bypass most firewalls.
It uses AES-256 encryption with a 160-bit SHA1 hash algorithm and 2048-bit RSA authentication, making it virtually unbreakable.
The SHA-1 (Secure Hash Algorithm 1) is an additional tool used in computer security to ensure information is kept safe.
It takes a piece of information as input and creates a unique code of 40 letters and numbers called a “message digest.”
This code is like a fingerprint for the original information and it can verify the authenticity of the data.
2. Secure socket tunneling protocol (SSTP): Microsoft-backed option
SSTP was created by Microsoft as a replacement for the less secure PPTP and L2TP/IPSec protocols.
Although SSTP is commonly used to secure Windows VPN connections, it also supports Linux and Mac.
While it can bypass firewalls that block certain ports, it lacks modern security features. The encryption cannot be cracked, but SSTP is fairly easy to detect and block by ISPs and network admins.
3. Internet key exchange version 2 (IKEv2): A stable option for mobile VPNs
IKEv2, built on IPsec, is a tunneling protocol that creates a secure VPN connection between VPN devices.
It’s faster than other options, such as OpenVPN, but it’s easier to restrict/block. Nevertheless, it’s still used by many VPN service providers.
4. WireGuard: modern cutting-edge protocol
Unlike most VPN protocols that rely on AES-256 encryption, WireGuard uses a newer form of authenticated encryption called ChaCha20.
The primary distinction between AES-256 and XChaCha20 encryption is that the former is a block cipher, whereas the latter is a stream cipher.
Essentially, block ciphers need to convert data into blocks before the encryption, while stream ciphers skip this process.
However, WireGuard implementation is still in the early stages and has yet to be widely available through consumer VPN providers.
5. Point-to-point tunneling protocol (PPTP): fast but vulnerable option
This is an older protocol that was the first widely available VPN protocol.
It provides the fastest speed, making it popular for streaming content. But it’s vulnerable to hackers.
This vulnerability lies in its authentication protocol. It uses MSCHAP-v2 protocol which is fairly easy to breach unless you use a strong, lengthy password.
As a result, it is less secure than other protocols.
6. Layer 2 Tunneling Protocol (L2TP): widely available but slow option
It can accept many different encryption protocols.
However, because it encapsulates data twice, it is one of the slowest protocols available. It’s not ideal also because it’s easy to detect.
What are the benefits of VPN encryption
At present, VPN encryption has become more critical than ever.
Here are some of the benefits it offers you.
1. Improved online privacy
Data transmission over the internet is one of the most vulnerable aspects of online communication.
Whether sending emails, transferring files, making financial transactions, or simply browsing the web, your data is vulnerable to attacks.
VPN encryption hides all data transmitted between your device and the VPN server – ensuring that your online activity is for you alone.
Ultimately, it protects your online activity from tracking by advertisers and other third-party organizations.
2. Provides data integrity and authenticity
Encryption helps to ensure that the information has not been tampered with or altered during transmission or storage, assuring that the data is authentic.
It also can provide authentication and verification of the identity of the sender or receiver of the data, ensuring that the communication is genuine and not from an imposter.
3. Cost savings for businesses
VPN encryption can help businesses save money by reducing the need for expensive cybersecurity measures.
Businesses can use a VPN to protect their data and online activity without investing in expensive hardware and software.
What are the downsides of VPN encryption?
VPN encryption also has its downsides. And it’s good that users are aware to avoid them. These include:
1. Slower internet speeds
VPN encryption can slow down internet speeds due to the additional processing required to encrypt and decrypt data.
This can be especially noticeable when using VPNs with strong encryption methods or accessing content from far-away servers.
2. Doesn’t protect against all cyber attacks
While VPNs can protect against eavesdropping and data interception, they cannot prevent all types of cyber attacks.
For instance, distributed denial of service (DDoS) attacks can still disrupt internet connections even with encryption in place.
DDoS attacks overwhelm a target’s servers with traffic, making it difficult or impossible for legitimate users to access the targeted website or service.
While VPNs can help protect against DDoS attacks by masking the user’s IP address, they cannot prevent the attack from occurring.
Also, VPN encryption alone can’t stop viruses, malware, phishing, or other attacks that target personal information directly.
3. Compatibility issues
Some VPNs may not be compatible with specific devices or software, making it difficult to use them in certain contexts.
For example, some VPN encryption may not work with certain routers or operating systems. Moreover, some only work with IPv4 and not with IPv6.
This can result in problems accessing websites, using specific applications, or connecting to certain networks.
Summary
While a VPN is a powerful and widespread tool, only some understand how VPN encryption works.
As we’ve explained, it uses mathematical algorithms to encode data and ensures that only the intended recipient can decrypt and read it.
This is so important in protecting your privacy and securing personal data. We hope this guide answered all your questions about how VPN encryption works.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages