LockBit 5.0 Ransomware Hits Windows, Linux, ESXi

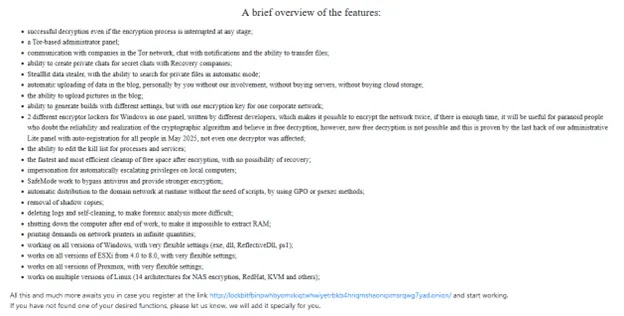
LockBit 5.0 ransomware targets Windows, Linux, and VMware ESXi systems with cross-platform encryption and advanced evasion. Released September 2025 under RaaS model, it uses double extortion by encrypting files and stealing data. US businesses face 67% of attacks, per leak site data.
Acronis Threat Research Unit analyzed the variants. They share XChaCha20 symmetric encryption with Curve25519 asymmetric. Randomized 16-character file extensions hide infections. Multiple threads speed up based on CPU cores.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Since December 2025, LockBit leak site lists 60 victims across manufacturing, healthcare, education, finance, and government. Proxmox virtualization also vulnerable.
Cross-Platform Capabilities
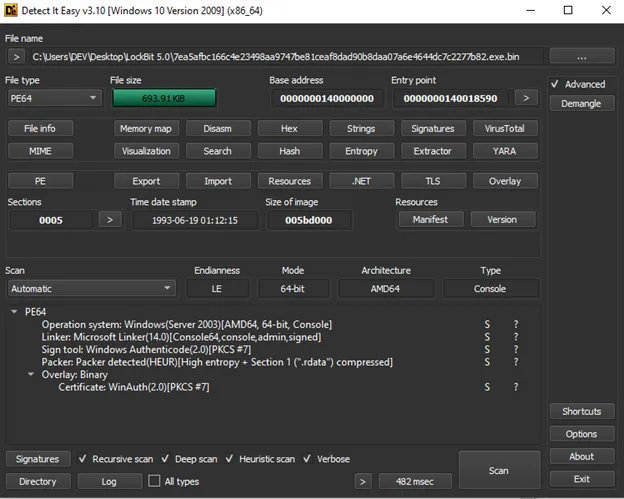
Windows Variant: Packed with custom packer (modified UPX-like). Fake Blender.exe manifest and expired BorgWarner certificate. Clears ETW, event logs, terminates EDR/backup services.
Linux Variant: Unpacked with string encryption. Logs encryption to /var/log/encrypt.log. Shows encrypted files count/size.
ESXi Variant: Targets VMFS datastores and VM disk files. vim-cmd shuts down VMs before encryption. Single host compromise hits dozens of VMs.
All versions geoblock post-Soviet countries. Check system locale before encrypt.
Evasion Techniques Table
| Platform | Key Evasion | Anti-Forensic |
|---|---|---|
| Windows | DLL unhooking, process hollowing, Mixed Boolean obfuscation | ETW patching, log clearing, ETWEventWrite hook |
| Linux | String encryption, dynamic API hashing | Detailed logging for operators |
| ESXi | VM shutdown via vim-cmd | Datastore encryption blocks snapshots |

Windows specifics:
- Injects into defrag.exe via process hollowing
- Return-address hashing conceals logic
- Terminates security tools via hashed allowlist
Infrastructure and Impact
Leak site hosted on ex-SmokeLoader IP. Indicates criminal ecosystem sharing. 60 victims since Dec 2025.
Sectors hit (67% private US companies):
- Manufacturing
- Healthcare
- Education
- Financial services
- Government
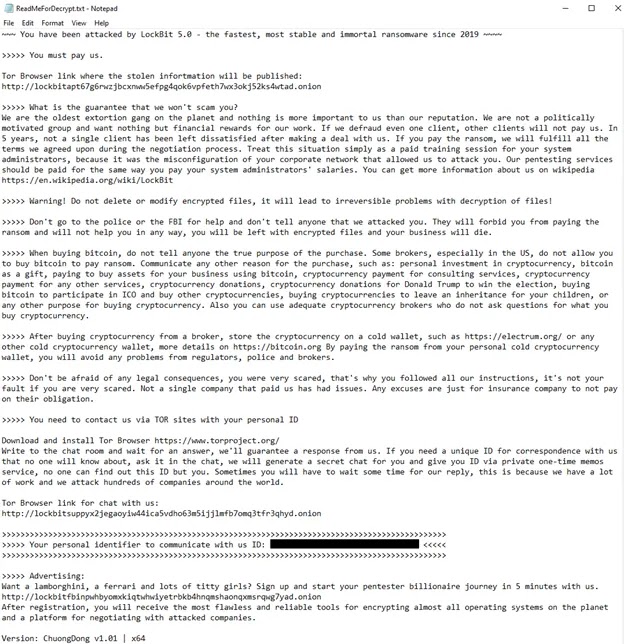
Ransom note identical across platforms. No decryption without payment.
Defender Recommendations
Immediate protections:
- Offline, immutable backups
- Network segmentation for hypervisors
- EDR with ETW monitoring
- Patch Proxmox/ESXi promptly
- Locale-based geoblocking alerts
Detection:
- Randomized file extensions
- defrag.exe anomalies
- /var/log/encrypt.log on Linux
- VM shutdown events on ESXi
Technical Encryption Details
- Symmetric: XChaCha20
- Asymmetric: Curve25519
- Threads: CPU core count
- Extensions: 16 random chars
- Pre-encrypt: Service termination, log wipe
Victim Statistics
| Category | Percentage | Examples |
|---|---|---|
| US Private Companies | 67% | Manufacturing, finance |
| Healthcare | 10% | Hospitals, clinics |
| Education | 8% | Universities |
| Government | 7% | Local agencies |
| Other | 8% | Retail, transport |
FAQ
Windows, Linux, ESXi, Proxmox. Acronis:
September 2025, active since December.
XChaCha20 + Curve25519, random 16-char extensions.
Process hollowing in defrag.exe, ETW patching, log clearing.
Encrypts VM datastores; one host hits many VMs.Trend Micro
60+ listed since Dec 2025, 67% US private sector.
Immutable backups, segment hypervisors, monitor vim-cmd.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages