Single Threat Actor Drives 83% of Ivanti EPMM RCE Exploits

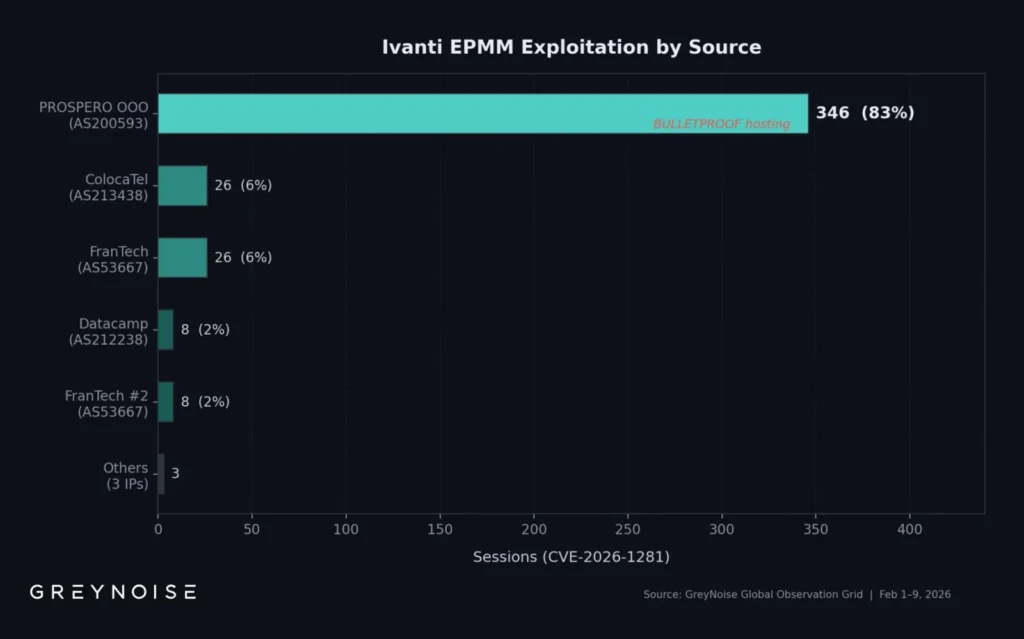
One threat actor caused 83% of recent attacks on Ivanti Endpoint Manager Mobile. They exploited CVE-2026-21962 and CVE-2026-24061 for unauthenticated remote code execution. GreyNoise tracked 417 sessions from February 1-9, 2026, mostly from IP 193.24.123.42 on bulletproof hosting.
The IP belongs to PROSPERO OOO AS200593. It hit a spike of 269 sessions on February 8, 13 times the average. 85% used OAST DNS callbacks for access checks, like initial brokers do. Automation rotated 300 user agents across browsers and OSes

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
.
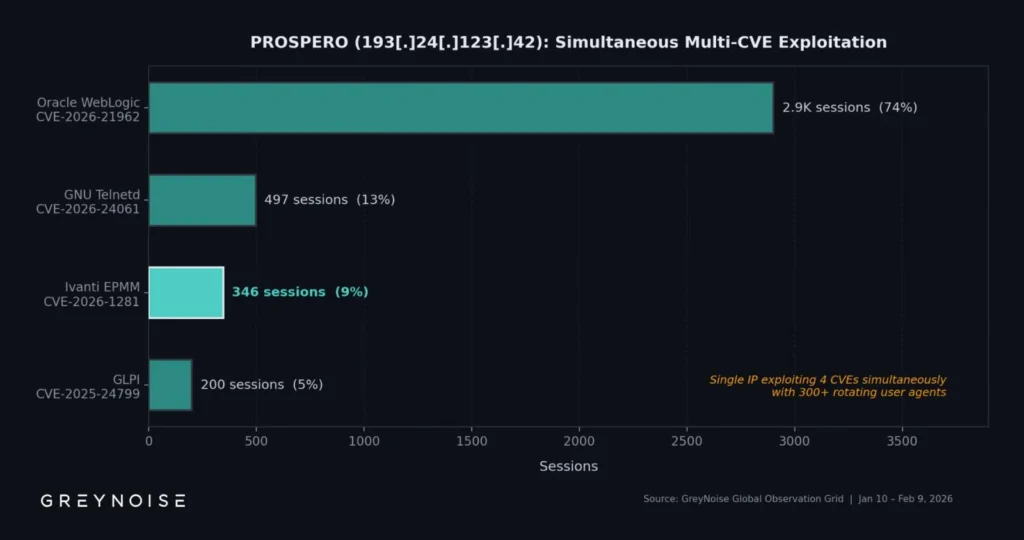
This actor also scanned Oracle WebLogic (CVE-2026-21962, 2,902 sessions), GNU Telnetd (CVE-2026-24061, 497 sessions), and GLPI (CVE-2025-24799). Published IOCs miss this main source.
GreyNoise reports: “Exploitation is accelerating. 269 sessions on February 8 alone, up from a daily average of 21. Defenders with unpatched, internet-facing EPMM instances should assume they have been scanned.”
Ivanti spokesperson: “Customers who have not yet patched should do so immediately… The patch requires no downtime and takes only seconds to apply.”
Exploitation Stats
| Vulnerability | Sessions | % of Total | Notes |
|---|---|---|---|
| Ivanti EPMM (CVE-2026-21962/24061) | 417 (83% from 1 IP) | High | 354 OAST callbacks |
| Oracle WebLogic (CVE-2026-21962) | 2,902 | Dominant | Same actor |
| GNU Telnetd (CVE-2026-24061) | 497 | Medium | Automated |
| GLPI (CVE-2025-24799) | 200 | Low | Multi-target |
Attack Patterns
8 unique IPs total. Bulletproof AS hides the main one. No downtime patches available now. Full fix in EPMM 12.8.0.0 Q1 2026. Use RPM 12.x.0.x/12.x.1.x meantime.
Ivanti urges rebuild/migration for safety. CISA lists CVE-2026-1281 as exploited.
Defense Steps
- Apply RPM hotfixes now.
- Hunt OAST callbacks in DNS logs.
- Block 193.24.123.42 and PROSPERO IPs.
- Review for code execution signs.
| Action | Urgency | Resource |
|---|---|---|
| Patch RPM | Immediate | Ivanti hub |
| IOC Scan | High | GreyNoise SITREP |
| Rebuild EPMM | Conservative | Forums guide |
| Log Review | Ongoing | DNS/traffic |
FAQ
Single IP 193.24.123.42 caused 83% of 417 sessions.
CVE-2026-21962, CVE-2026-24061 in EPMM.
Hotfixes out; full in 12.8.0.0 Q1 2026.
OAST DNS callbacks, command tests.
WebLogic, Telnetd, GLPI by same actor.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages