OpenVPN Obfuscation - What it is & How it Works

As internet censorship and surveillance continue to rise in various parts of the world, like China, Russia, and Iran, VPNs have become necessary for protecting online privacy and security.
OpenVPN, in particular, has been a popular choice among VPN protocols, as it offers a high level of security and flexibility for users.
However, this VPN traffic can sometimes be detected and blocked by ISPs or other entities, which defeats the purpose of using it in the first place.
This is where OpenVPN obfuscation comes in. In this guide, we’ll discuss how to use this feature to access the internet freely and without fear of bans.
What is OpenVPN obfuscation?
OpenVPN obfuscation is a technique that allows users to mask their VPN traffic so it looks like regular traffic. This makes it less detectable by ISPs, governments, or other entities that may be monitoring online activity.
The technique is useful in countries like China, where the Great Firewall monitors and censors online content. It’s also helpful if you try to access sites or apps that block VPNs.
It works by creating a secure and encrypted connection between a user’s device and the VPN server, which then scrambles the traffic to make it harder to detect and block.
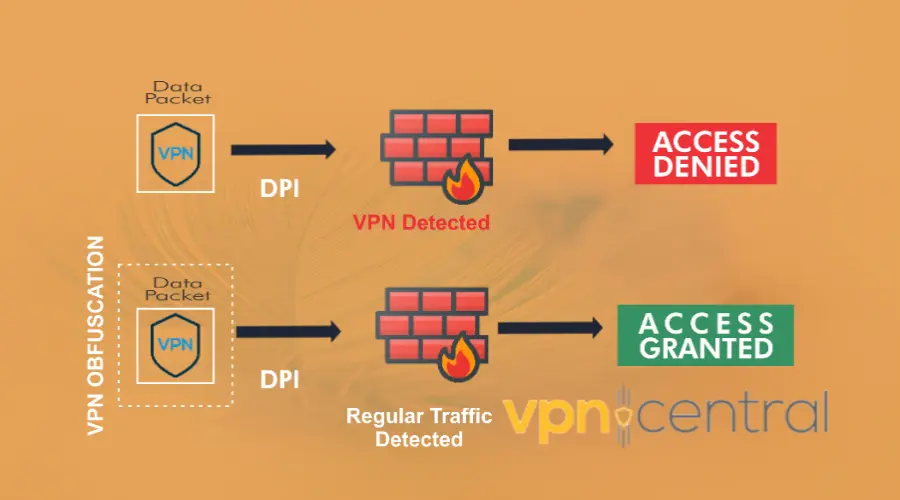
How to obfuscate OpenVPN traffic?
Manual setup
As you’ll see below, there are several ways to obfuscate traffic. One of the most commonly used that’s also very reliable is using obfsproxy which makes OpenVPN traffic look like regular HTTPS traffic.
Here’s how to change a regular OpenVPN server to an obfuscated server:
- Open the config file you use to connect to your OpenVPN server normally. Create a copy of the file and rename it to obfuscated server (so you can differentiate between them).
- Modify the renamed config file by adding the following lines:
socks-proxy-retrysocks-proxy 127.0.0.1 10194
- Save the file with the .ovpn extension.
Automatic setup
If you use a VPN service provider that has built-in obfuscation features, all you have to do is enable it from the app.
- Launch your VPN.
- Navigate to the server list and select Specialty servers.
- Select Obfuscated servers.
- Pick a server location and connect.
Keep in mind that some VPN apps have built-in obfuscation that can’t be manually enabled or disabled. Instead, they use it on all servers all the time.
If that’s the case, all you have to do is connect to a VPN server in your VPN app.
OpenVPN obfuscation tools and features
Here are some of the most common tools used to obfuscate OpenVPN and their features:
1. Obfsproxy
This is an enhanced OpenVPN protocol that scrambles internet traffic to maximize security. It works by adding a layer of encryption to the VPN traffic and masking it as HTTPS traffic.
Consequently, this makes it difficult for firewalls and deep packet inspection to identify and block.
Another good thing about Obfsproxy is that it ensures complete privacy of your internet activity. This is because its obfuscation protocol does not contain any identifiable data patterns.
2. Stunnel
Another tool is Stunnel, which encrypts OpenVPN traffic and tunnels it through the SSL/TLS protocol. This makes it difficult for firewalls to detect and block the traffic.
Stunnel acts as a mediator between the OpenVPN client and server, encrypting and decrypting data as needed.
It also helps to improve the security of OpenVPN connections by adding an extra layer of encryption.
3. Shadowsocks
In countries like China, where internet censorship is rife, the open-source proxy protocol, Shadowsocks, comes in handy.
It employs the SOCKS5 proxy protocol, which disguises encrypted VPN traffic as HTTPS traffic.
Since HTTPS is a commonly accepted security protocol, it avoids suspicion and effectively bypasses VPN blockers and DPIs.
4. OpenVPN over SSL
OpenVPN over SSL provides an additional layer of security by encrypting the traffic twice.
This double encryption makes it difficult for Deep Packet Inspection (DPIs) to detect the VPN traffic, and all they see is standard HTTPS data.
While both OpenVPN over SSL and Shadowsocks use encryption to hide VPN traffic and bypass censorship, they differ in their encryption protocols.
OpenVPN over SSL encrypts traffic twice, first through OpenVPN protocol and then through SSL encryption. Shadowsocks uses the SOCKS5 proxy protocol to disguise VPN traffic as HTTPS traffic.
5. OpenVPN scramble
This VPN obfuscation feature uses XOR obfuscation to hide the VPN signature. It transforms the VPN traffic into meaningless code and renders it invisible to Deep Packet Inspection.
How to optimize OpenVPN obfuscation performance and security
Here are some recommended steps to improve the safety and performance of your OpenVPN obfuscation:
1. Choose the right obfuscation technique
Different obfuscation tools have different strengths and weaknesses, and choosing the right one can significantly impact performance and security.
Consider factors such as encryption strength, speed, and compatibility with your VPN provider when choosing an obfuscation tool.
2. Use the latest version of OpenVPN
Older versions of OpenVPN may have vulnerabilities that attackers can exploit.
Make sure to use the latest version of OpenVPN to ensure that you have the latest security patches and improvements.
You can check the OpenVPN version from the graphical user interface (GUI) of the OpenVPN client if you have it installed. To do this:
- Open the OpenVPN client on your system.
- Click on the Help menu at the top of the window.
- Click on About OpenVPN.
- The version of OpenVPN installed on your system will be displayed in the window that opens.
Alternatively, you can obtain the version information by executing the command openvpn –version in the terminal window.
If the version is not up to date, install the latest version of OpenVPN.
3. Configure your firewall properly
Firewalls can interfere with OpenVPN obfuscation by blocking or throttling VPN traffic. Configure your firewall properly to allow OpenVPN traffic and minimize interference.
4. Use a high-quality VPN provider
If you’re using a third-party VPN app, choose a reputable VPN provider with strong encryption, fast servers, and obfuscation options
Not all VPN providers give the same experience, and some may have weaker security or slower performance than others.
5. Optimize your network settings.
You can improve OpenVPN obfuscation performance by optimizing your network settings.
Configure the obfuscation tool and OpenVPN to use UDP instead of TCP for faster performance.
Also, adjust the MTU (Maximum Transmission Unit) setting to improve performance and reduce latency.
Pros and cons of OpenVPN obfuscation
OpenVPN obfuscation can be an effective way to bypass VPN blocks and avoid firewall detection. However, it has its pros and cons.
Pros of OpenVPN obfuscation
The following are the benefits:
1. Enhanced security
OpenVPN obfuscation adds an extra layer of security to the already secure OpenVPN protocol.
It protects against deep packet inspection and other surveillance techniques, increasing privacy and security while using a VPN.
2. Bypass VPN blocks
OpenVPN obfuscation is an effective way to bypass VPN blocks. By disguising VPN traffic as regular internet traffic, it helps you access to content that might otherwise be restricted in your region.
3. Good firewall compatibility
Also, it is possible to bypass network firewalls that might be blocking VPN traffic through OpenVPN obfuscation.
By using any available port on TCP or UDP, obfuscated traffic can easily pass through firewalls undetected.
4. Works on multiple platforms
Similarly, it is compatible with various platforms, including Windows, Linux, MacOS, Android, iOS, and more. You can use it on any device, regardless of the operating system.
Cons of using OpenVPN obfuscation
The potential drawbacks include:
1. Slower speeds
While OpenVPN obfuscation can help bypass firewalls and other blocks, it can also slow down connection speeds due to the extra encryption and obfuscation steps.
2. Configuration complexity
Setting up OpenVPN obfuscation can be more complex than a standard OpenVPN connection, which may require more technical knowledge and skill.
3. Increased bandwidth usage
The additional encryption and obfuscation steps in OpenVPN obfuscation can increase the amount of bandwidth used, which can be a concern for those with limited bandwidth or data caps.
4. Possible performance issues
Sometimes, using OpenVPN obfuscation can lead to performance issues such as increased latency or dropped connections.
Summary
As governments and ISPs continue to restrict online content and monitor user activity, VPN obfuscation technology has become a crucial tool for maintaining privacy.
OpenVPN obfuscation is a great option for bypassing VPN blocks and avoiding firewall detection.
Although it can have drawbacks, such as slower speeds and increased complexity in setup, it remains a reliable option for ensuring online security.
FAQ
Yes, OpenVPN does have obfuscation capabilities. When enabled, it will camouflage the traffic to look like a regular internet.
You can use a third-party VPN that has obfuscation features and just enable them. For the manual configuration, you have to download the OpenVPN configuration file and modify it with obfuscation commands.
Yes, OpenVPN does have obfuscation. When enabled, it will camouflage the traffic to look like regular traffic instead of a VPN.
Yes, but it’s unlikely.
Obfuscated VPNs cannot be easily detected because they alter the appearance of data packets to evade recognition by systems looking for VPN traffic.
The packets are disguised to pass undetected, so the only way a VPN connection could be discovered is if someone manually inspects your traffic, which is unlikely.
Go to your VPN app’s Settings and find the obfuscation feature. Select it and enable it. Depending on which VPN you use, the obfuscation feature may have a branded name, such as Stealth VPN, VPN Cloaking, VPN Stealth Mode, Traffic Obfuscation, Cloaking Technology
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages