Digital Footprints: How Tech Giants Monetize Your Online Behavior
A deep dive into the business of personal data.

The number of internet users is rapidly increasing. A recent study by Statista found that 4.95 billion people, or 61.4% of the world’s population, are on social media. Social media platforms become remarkably integrated into people’s daily lives—for instance, the average person accesses 6.6 social media platforms monthly.
Most social media services do not impose fees on their users. For example, you can make phone calls using WhatsApp without paying a penny. But if social media platforms are free, then how do these giant companies cover their expenses?
In terms of running costs, Facebook needs to hire a large number of technicians to run its massive data centers around the globe and ensure the high availability of its services. These costs are still covered by its users. But how does this work? Social media platforms collect and sell data on your behavior to advertisement companies and other interested parties, including government intelligence services and commercial data brokers, which return a huge sum of money to them.
In this post, I will discuss the various information gathered by social media platforms, online applications, and other web services when using their applications. Surprisingly, you will learn that even if you are not using a particular social media platform, such as Facebook or Twitter, they can still track your browsing activities across the internet and exploit that data for commercial gain.
Key takeaway:
- 4.95 billion people (61.4% of the world’s population) are social media users.
- Social media platforms like Threads, Instagram, and Facebook track 86% of users’ personal data.
- The average USA adult spends over 4 hours of their daily online time on mobile. 88% of that time is spent on apps.
- Out of all social media apps, Instagram shares the largest amounts of personal data with third parties – 79%. Facebook comes second with 57%.
- eBay tracks 40% of its user’s personal data.
- Telegram shares users’ personal data with companies located in Dubai and the British Virgin Islands.
There are various parties interested in acquiring internet users’ private information online. Non-tech-savvy users may argue that they have nothing to hide when using the internet, and thus, they do not care about someone tracking their online activities. However, this idea is entirely wrong, as individuals’ online activities may reveal a significant amount of information about them and impact their lives in various ways.
Let me give you an example:
Some patients use search engines to find medicine or herbal treatment for sensitive health issues, such as sexual and mental health. What if the search engine provider or other commercial entities collect these search queries, connect them to the searcher’s real identity, and then sell them to a third-party data broker? I’m sure this could be embarrassing; however, if such data finds its way into your future employer or insurance company, you could suffer from discrimination without even knowing the actual reason.
So, let’s move to the critical question:
Who collects internet users’ data?
Several entities are interested in acquiring your personal information for various reasons.
Social media platforms
Social media platforms, such as Facebook, Twitter, Instagram, and TikTok, gather enormous amounts of user data. For example, Facebook collects a plethora of information about their users in addition to the info provided during registration (basic account information: name, email, phone number).
Facebook and other similar platforms collect additional important information that is strictly related to the person and can identify them across the web, such as:
Profile information
Such as username, profile picture, and cover photo.
Contact list
When installing social media applications on your smartphone, such as the Facebook and Instagram app. They will request to gain access to your phone contact address book. If a user grants such permission, the app will get a copy of all your connection’s names along with their phone numbers.
Demographic details
Such as user geographic location (country, state, town), gender, and language preferences.
Device technical information
This includes the technical information of the computing device used to access the social media service, such as:
- Device model
- Operating system type
- Screen resolution
- Web browser
- Application version
- And other information related to the device itself.
Information about user connections
For example, your connections on Facebook, the pages and people you follow, and your searches on the platform.
Content shared by users
This includes all types of content you share on the platform:
- Photos
- Videos
- Comments
- Posts
- Location data (check-ins and location tags).
We can also consider interactions on the platform, such as “Like” and “Share” as a type of content related to the user.
Private messages
Facebook and similar messaging applications will record metadata about a user’s private conversation with others, such as the date/time of the conversation and the people involved in the conversation.
Although social media platforms assure the confidentiality of private communications, we cannot assume full privacy. For instance, the provider can technically access the private message contents even though they are encrypted.
Other interactions on the platform
When a user clicks on a specific advertisement or views some commercial video, then the social media provider will record this information to customize ads with similar content/advertisement while using the service.
Digital files metadata
Almost all digital files contain metadata within them. Metadata is defined as data about data. For example, a personal picture of a user posted online could have different metadata details hidden within it, such as:
- Capturing device type
- Date/time when the photo was taken
- GPS coordination of the physical location where this photo was taken – if this feature is enabled in the capturing device.
Cookies, tracking pixels
Cookies have been famous since the early days of the internet for remembering some settings about a user’s device when they repeat their visit to a website. However, cookies have developed to become more long-term. For instance, some types, such as Flash and persistent ones, can remain on user devices indefinitely and can regenerate themselves even after they’re deleted.
Tracking pixels, however, are embedded within web pages to collect information about users. When combined with cookies, they can follow your browsing history across the web.
Login events
When a user accesses their social media account, such as Facebook, it will record different information about this event (the login event), such as:
- The date/time of the login
- Location (known from IP address)
- The device/web browser type – such as smartphone, desktop, or tablet.
Third-party applications
Many online services allow us to use our credentials from social media accounts, such as Facebook or Google, to access their protected resources. For example, in Figure 1, we can see Medium allows signing in using different social media accounts, such as Facebook, Twitter, Apple, and Google.
These third-party applications could access some of the user data kept by the social media provider, revealing important personal information (see Figure 2).
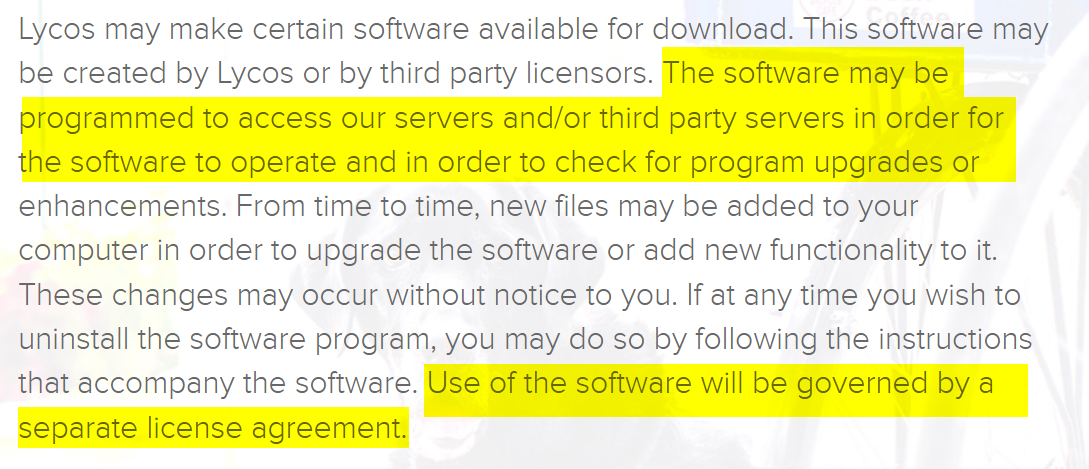
Figure 1 – Medium allows login to its service using different social media services in addition to an email address.
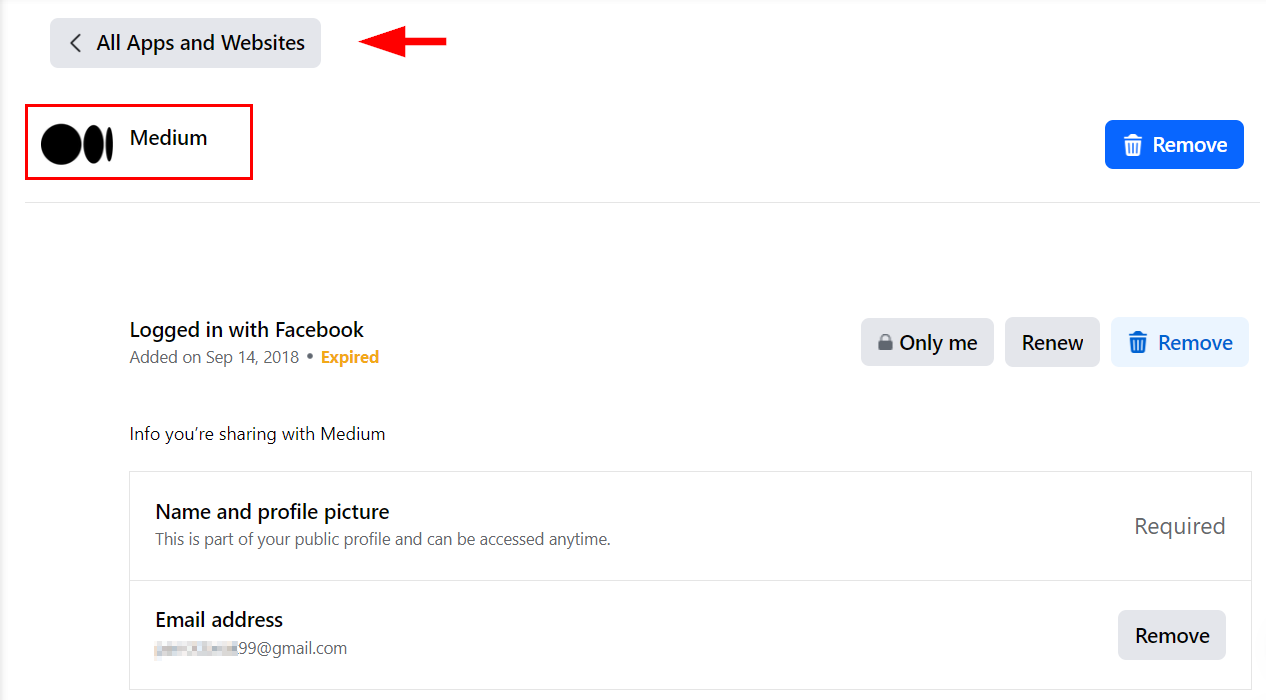
Figure 2 – Third-party applications can access some information about a user account on social media platforms when using social login to access some online services.
Device permissions
Some social media applications request permissions to access the user’s underlying computing device resources upon installation, such as:
- Microphone
- Camera
- Contact list
- Photo gallery
This access can be abused in one way or another to gain important information about the user.
Behavioral information
A social media service will record different usage information about its users, such as
- Time spent on the platform
- Preferred date/time when you typically access the platform
- What device you’re typically accessing the platform on
For instance, some people access their Facebook through a smartphone on the go, while others prefer to access it using a tablet or laptop when at home. Such information can be used to target users with particular commercial advertisements based on their device type and location.
Search engines
Like social media platforms, search engine providers collect important user information. For instance, Google and Microsoft (Bing) provide a free email service (Gmail and Outlook, respectively).
When you conduct a search using any of these two engines while logged into your email account, the search engine can easily connect your search queries with your real identity.
Typical information collected by search engines about their users includes the following:
Search queries
Search engines typically gather their users’ search queries. This gives insight into what people care about or are looking for.
Geographical information
By knowing a user’s IP address, search engines can know their geographical location in addition to the Internet Service Provider (ISP) they are accessing the internet through.
Web history
Say the user is already logged into their email account, such as Outlook, Gmail, or Yahoo!, and is using the associated email service of the search engine provider. Then, the search engine can connect their web browsing history to their email account and thus reveal a significant amount of information about their web usage and interests.
Embedded scripts
Some search engines provide embedded services for website owners to analyze their performance. For instance, Google Analytics allows website owners to track visits to their website and collect various analytical information, such as which pages are more visited and visitor’s geographic locations. Google can use its embedded scripts to track and profile Internet user’s visits across the web.
Which search engines collect the most personal data?
Now, I will give some examples of the most intrusive search engines when it comes to privacy. According to my research, these are the worst search engines in terms of tracking their users’ web browsing activities.
Ask
Ask is among the early search engines (first launched in 1996) that launched in the early days of the internet. Although it is no longer a high-ranked search engine, it is still used by millions of people to search within specific niches, such as references, health, lifestyle, and money news.
What makes us put Ask at the top of the worst search engines for privacy is its Privacy Policy terms. According to it, the company collects all sorts of personal information and shares it with other third parties. Here is what it collects:
- The user’s IP address is utilized to access ASK services. As we know, the IP determines the visitor’s geographical location. ASK shares this information with external vendors, such as hosting and content delivery companies.
- ASK uses the Google Analytics service, which means Google will also receive your IP address and can combine it with other information, such as your IP when accessing Gmail (see Figure 3). That way, it can identify your real identity.

Figure 3 – ASK Privacy Policy states that Google receives visitors’ IP addresses for Analytical purposes.
- ASK assigns a unique ID for each user’s browser and stores it as a web cookie in their computing device. This allows the company to distinguish repeating website visitors when using the same web browser/device.
- the search engine employs a browser fingerprinting technology – via tiny pixel images- to collect technical info about its visitors.
The problem with this is that ASK shares this information with different advertisers and digital advertising technology intermediaries to help them display targeted advertisements for ASK users based on their web browsing activities. This will allow third parties to track visitors’ web histories across the internet.
- When installing any ASK application, such as its web browser toolbar or ASK for mobile apps, the company will get the unique identifier (“ID”) that is connected to your app store account ID (such as Google Play or Amazon Appstore).
- ASK will also record where you were coming from (the previous website) before installing the ASK app.
- The company will record the following information and tie it to your browser ID:
- Your visits
- Search queries
- Search results you click on
- URL of the webpage you were last visiting before clicking on the ASK site
- Pages viewed
- Any installation of a browser extension or mobile app, comments posted where applicable
- Duration of visit
Additionally, information such as installs, uninstalls, bookmarks, adding to the device home screen, and use of new tabs will get recorded when using the ASK app on your mobile device.
All this information will be shared with advertisers, digital advertising technology intermediaries, and other service providers, such as retargeting companies and social media platforms like Facebook.
- ASK collects technical information about the computing devices used to access ASK websites, such as:
- Device type
- Mobile device ID number
- Screen resolution
- Web browser information
- Operating system type
- Timezone
- Installed fonts and language.
ASK does not clearly define with whom it will share the technical information of users’ devices.
It keeps this information on its US servers, so the USA’s California Consumer Privacy Act (CCPA) is implemented to govern the collection and processing of visitors’ personal information).
Visitors from EU countries should expect to be subject to less restrictive privacy laws when using ASK services than those implemented in their countries.
Lycos
Lycos, Inc. is a search engine and web portal established in 1994 in the USA. It is not one website. It has many connected websites that provide different web services, such as email, web hosting, social networking, and entertainment. All Lycos-connected websites use the same privacy policy terms.
Going to the company’s Privacy Policy, we can find that it is talking about its compliance with the EU GDRP. However, diving deep into the rest of the terms, we discover that there are many worrying privacy issues concerning users’ personal data:
- Lycos collects visitors’ IP addresses when using its services or making search queries. They define the IP address as anonymous information. However, combined with other data, it could identify the internet user across the internet.
- Other anonymous information collected for each visitor by default includes the web page visited by the user before clicking over to the Lycos network site and technical details on visitor computing device type such as web browser type and operating system.
- The search engine frequently runs promotions and contests across its sites. These are often sponsored by third-party companies. Any data gathered during promotions gets shared with the sponsoring partners.
- Lycos uses cookies to enhance the surfing experience across its network of sites. The privacy issue here is that third-party advertising networks for Lycos may issue cookies and web beacons on its network of sites. Lycos has no access to the information collected using cookies by its third-party vendors and advertisers (See Figure 4).
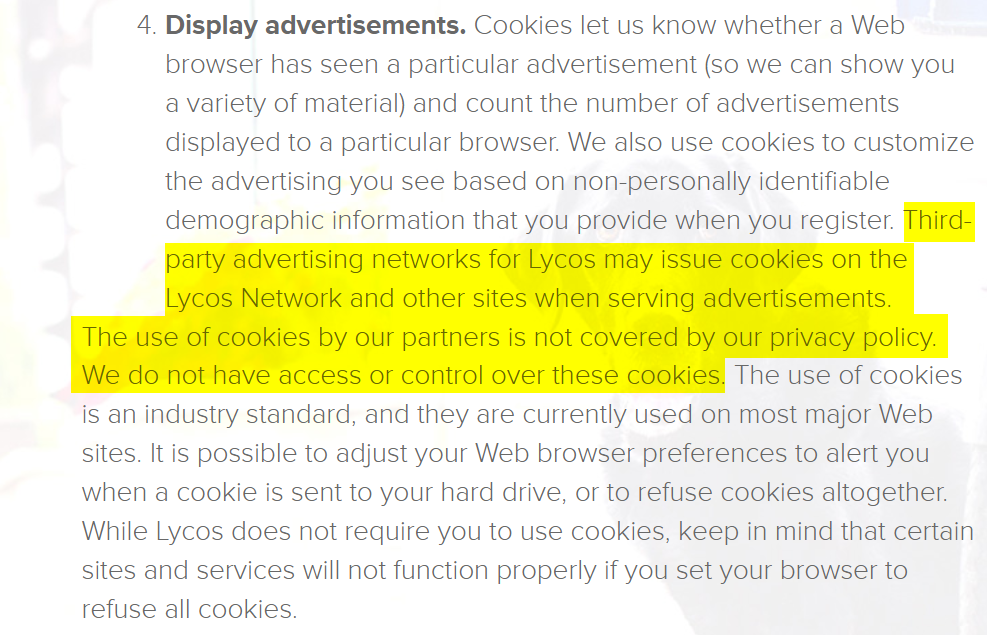
Figure 4 – Lycos Privacy Policy states that third parties may install tracking cookies on Lycos visitor’s computing devices, and this is not governed by Lycos privacy agreement.
- Lycos uses social media widgets, such as Facebook’s “Like” and “Share” buttons. We already covered that Facebook widgets contain JavaScript code to track you across the web. These widgets will also install a tracking cookie on the visitor’s device, even though they are not a Facebook user.
- Lycos may share user information with third parties, such as advertising companies. Although Lycos requires these third parties to agree to keep personal data confidential per Lycos’ privacy policy. However, when users’ data is scattered across different servers in different jurisdictions, keeping all this data safe becomes challenging and complex.
- Lycos may advertise specific applications for users to download. These apps could be created by Lycos or other third-party companies. Lycos says these apps may establish connections with servers outside the Lycos network to function.
These servers could be residing in other countries worldwide (see Figure 5). Although, there is a separate privacy agreement for accessing each app. We do not know if the connections with external servers will leak sensitive personal information.

Figure 5 – Lycos Privacy Policy states that some Lycos software could access external servers of third-party vendors.
- Lycos provides vague details on where they store data, including international destinations. For instance, Lycos states it may store user data in the USA and unspecified overseas locations. For example, if Lycos has a data center in China, users’ personal information could be transferred there. This raises privacy concerns, as some countries have weaker protections concerning users’ personal information.
Google is the most popular search engine worldwide, as it handles an immense volume of search queries. Users initiate around 99,000 searches per second on it. This averages out to over 8.5 billion searches daily. Annually, Google estimates that its systems process about 2 trillion search queries globally.
In terms of privacy, the company gathers various information when using its devices, applications, and services. For instance, using any service connected to it, such as Search, Gmail, YouTube, Digital Assistant, and online purchases handled by Google, to name a few, will send some unique information about the user to Google.
Google does not hide the fact that it’s collecting personal data. However, it puts this practice in the direction of better servicing its users. According to its official “Privacy and Terms” policy, the company collects users’ information to:
“deliver services, maintain and improve them, develop new services, measure the effectiveness of advertising, protect against fraud and abuse, and personalize content and ads you see on Google and our partners’ sites and apps“
If we continue reading the “Privacy and Terms,” we will reveal more ways it collects user data. This data collection does not stop at Google services alone. Whenever you visit a website that utilizes Google AdSense or Analytics, the company automatically gathers some of your information. It captures your IP address when they land on these partner sites. Additionally, Google may plant cookies on visitors’ devices to track those users as they browse other sites (see Figure 6).

Figure 6 – Third-party websites using Google services share some visitors’ information with Google.
Now, suppose the user is simultaneously signed into Gmail when they access these external sites. In that case, Google can connect the collected data with the user’s real identity tied to that account. By integrating with advertising and analytics services embedded widely across websites, Google expands its surveillance operations beyond its own platforms. This allows comprehensive individual tracking across the web.
E-commerce websites
Online marketplaces, such as Amazon, eBay, and other stores, collect information about their customers to process their online purchases. They can utilize such data to understand customers’ preferences, target them with customized advertisements, and personalize their recommendations.
Here is what info online marketplaces collect on their users:
- Customer account information: To shop online, you often need to create an account with the merchant’s website or app. This account will contain personal information provided by the customer, such as:
- Customer name
- Email address
- Phone number
- Mailing address for delivery and billing purposes
- Purchase history: A record of all previous purchases for each customer, which includes product name, price, and shipping address
- Search queries: A user typically searches for products through the merchant’s internal search engine. The online store will record all these search queries along with all pages visited and how long the visit lasted for each webpage.
- Technical information about the computing device: Online merchants will use different tracking techniques to acquire technical information about your computing device and web browser, such as cookies, tracking pixels, and digital fingerprinting. The customer’s IP address is also recorded and is used to identify demographics.
- Payment information: The payment method the customer uses to make the purchase is recorded, such as PayPal, credit card, gift card, or digital wallet ID, such as Bitcoin.
Mobile apps
The mobile app industry is growing at an explosive rate. For instance, there are 3.55 million apps on Google Play, while the Apple store comes next with 1.6 million available apps for iOS. According to Statista, in 2022, the number of global mobile subscribers has reached 6.4 billion and is expected to exceed 7.7 billion by 2028.
eMarketer found that most Americans’ mobile time spent takes place in apps. For instance, the average USA mobile user spends 4 hours daily, and 88% of these are spent using mobile apps.
The widespread usage of mobile apps makes them among the top collectors of internet users’ information. Here are the main examples of data collected by mobile apps:
- Personal information: Many mobile applications request some identifying information from their users. Such as name, email, and phone number or request access to their associated social media accounts, such as Facebook, Google, or Apple, to finish the registration process, which gives them access to user social data.
- Location data: Many mobile applications are location-aware. Hence, they can collect your geographical location while using the app. This allows them to map a user’s movements over time.
- Contact list: Many mobile apps request access to the user contact list. This allows the application to know who your friends and social contacts are and, maybe, target them with customized advertisements.
- Web browsing history: Some mobile applications can record users’ web browsing history (because they already have an integrated web component) when using some applications.
- Usage patterns: Mobile apps may be able to record usage patterns and connect them to your identity to profile you when browsing the internet. For example, financial apps may record all your monetary transactions and link them to your web browsing (such as online purchases).
Combined with a contact list and previous purchase history, an app can formulate a complete profile about each user.
- Technical details: Mobile apps can record various tech information about user computing devices, similar to social media platforms and search engines.
Which apps collect and share the most personal information?
Social media and food delivery apps are the most intrusive.
A study by Home Security Heroes shows that Meta apps like Instagram, Threads, and Facebook collect the largest amounts of user data – 86%. Another study by pCloud found that Instagram and Facebook share 79% and 57% of that data with third parties, respectively. LinkedIn and Uber Eats hold the third and fourth spots with 50% each (see Figure 7).
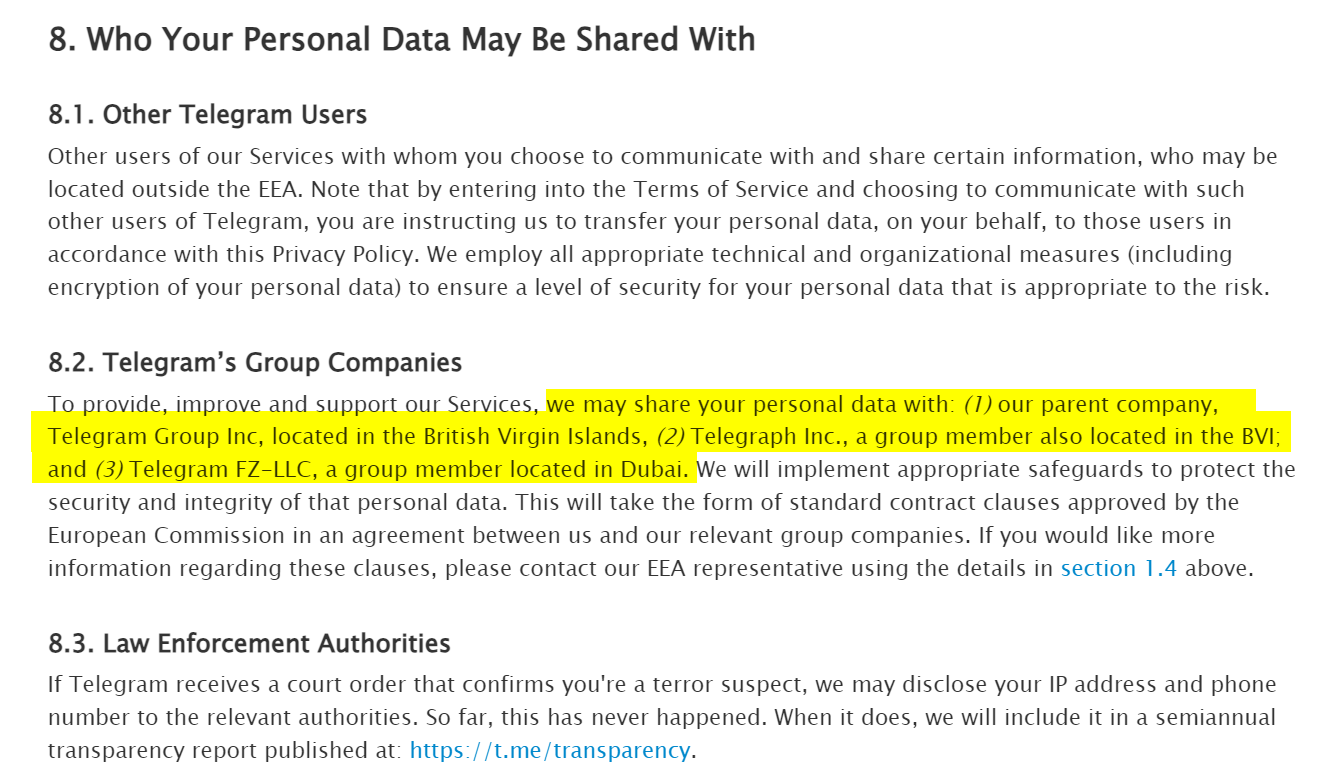
Figure 7 – Top applications sharing your data with third parties | Source: pCloud.
According to Data.ai (see Figure 8), the following 10 applications were the most downloaded until Q1 2023. The final charts for the year 2023 are not available yet. However, the first quarter still reflects the most downloaded application in 2023.
- TikTok
- WhatsApp Messanger
- CapCut
- Snapchat
- Telegram
- Facebook Messanger
- WhatsApp Business
- Spotify

Figure 8 – Top applications by download worldwide | Source: Data.ai.
Now, let’s discuss what information each application collects about its users:
TikTok
For the second year in a row, TikTok remains the most downloaded application in both Apple and Google Play stores. TikTok’s privacy policy lists the different information it collects, including:
- Profile information, such as:
- Name
- Age
- Username
- Password
- Language
- Phone number
- Social media account information
- Profile image
- User-generated content like:
- Comments
- Pictures
- Livestreams
- Audio recordings
- Videos
- Text
- Hashtags
- Virtual item videos
- Metadata, such as when, where, and by whom the content was created
- Your messages when using the TikTok messaging functionality
- Your communication with the TikTok visual assistant
- Information stored on the user device clipboard, such as text, images, and videos
- Contacts stored on your phone
- TikTok receives extensive data about user activities outside its platform from external partners like advertisers and analytics firms. This includes information about:
- Actions on other sites, apps, and even in physical stores
- Mobile advertising IDs
- Hashed emails
- Cookie IDs
- Offline purchase records
TikTok automatically collects the following information about all users when using its platform:
- IP address
- Geolocation-related data
- Device technical information, such as:
- User-agent
- Mobile carrier
- Time zone settings
- Identifiers for advertising purposes
- Model of your device
- Device system
- Network type
- Device IDs
- Screen resolution and operating system
- App and file names and types
- Keystroke patterns or rhythms
- Battery state
- Audio settings and connected audio devices.
- TikTok automatically assigns a device ID and user ID for each account
- Browsing and search history
- TikTok installs cookies
Instagram is a part of Meta Platforms, Inc., which includes Facebook (including the Facebook mobile app and in-app browser), Instagram, Facebook Messenger, and other Meta products, such as:
- Meta Portal-branded devices
- Meta Platforms Technologies Products such as Meta Horizon Worlds or Meta Quest (when using a Facebook or Meta account)
- Shops
- Meta Spark
- Meta Audience Network
- NPE Team apps
- Meta Business Tools
The privacy policy of Meta Platforms applies to all these products. So, in this section, I will cover the following applications:
- WhatsApp Messenger
- Facebook Messenger
- WhatsApp Business
The Facebook and Instagram applications are among the most intrusive applications when it comes to end-user privacy. For instance, when installing these apps, they will request access to the following permissions on your mobile device, smartphone, or tablet:
- Location info: Access user location using a device GPS sensor or cell tower signals.
- Metadata: Such as the GPS coordination of the uploaded content (photo or video). This information will not appear in photos published publicly, but Facebook will keep it.
- Contacts: Access the contact list stored on your mobile device. This feature is used to find friends to connect with on Facebook.
- SMS: The Facebook app may request access to SMS to send and view SMS text messages to verify user accounts upon registration and to enable two-factor authentication in some instances. It may also access call log history on the user’s mobile device.
- Content view: Pages you follow, people you interact with, and the content you view on the platform.
- Camera: Access to mobile camera to take pictures and record videos.
- Microphone: Access the mobile device microphone to record audio.
- Device storage: Access to files, media, and documents stored on the phone’s storage to enable content uploading to Facebook platforms.
- Device ID and call information: Access unique device identifiers and call-related data. This feature is used for analytics, fraud prevention, and ads.
- Device information: Meta collects various technical information about the devices used to interact with its services, including:
- Computers
- Phones
- connected TVs, and other web-connected devices.
The company combines this information across your different devices to formulate a complete profile of your usage patterns. The technical information collected from such devices includes:
- Device attributes: Operating system, hardware and software versions, battery level for mobile devices, signal strength, available storage space, browser type, app and file names and types, and installed plugins.
- Device signals: Meta collects information about nearby Wi-Fi access points, beacons, and cell towers.
- Network and connections: Name of ISP or mobile operators, language, time zone, mobile phone number, IP address, connection speed.
CapCut
CapCut is an AI-powered video editing platform. It allows novice users to create and edit videos with a few clicks using various templates. As of August 2023, it had over 490 million users on both iOS and Android phones.
Both CapCut and TikTok are owned by the same company – ByteDance. Being easy to integrate with TikTok has boosted the usage of CapCut worldwide.
What makes us worry about the CapCut video editing app is the amount of personal information it collects. For instance, according to a class action lawsuit filed in an Illinois federal court, CapCut gathers large quantities of private user data, including facial scans, from its over 200 million daily active users.
This extensive data collection generates massive profits for CapCut and its sister company, TikTok. However, the data harvesting also raises concerns about the Chinese government potentially accessing user information, according to the lawsuit allegations.
Aside from information collected from users upon registration, CapCut also collects tons of data automatically:
- IP address
- Device ID
- Network connections
- Mobile and device model
- App version number
- Country
- Operating system
- Device resolution
- System language and installed fonts
- Location data based on SIM card and/or the IP address
- Different information about images and videos to facilitate editing files
- CapCut and its business partners use cookies to track you
Its privacy policy document states that CapCut may share all this data with service providers and business partners. This is a significant privacy concern because CabCut doesn’t mention who those partners are.
Besides, combining information collected by CapCut with that collected by TikTok forms a detailed profile about each user.
Additionally, CapCut stores user info in data centers in both the USA and Singapore. This means your data may be stored outside your country of residence, which can result in the implementation of less restrictive privacy controls and regulations.
Snapchat
Snapchat is a popular messaging and video calling application. According to its privacy policy, it collects three main types of user information:
- Data you provide manually
- Info Snapchat gets when you use its services
- Data Snapchat gets from third parties
The following information is collected across the three categories above:
- Basic account information like:
- Name
- Username
- Password
- Email address
- Phone number
- Date of birth
- Profile and Avatar pictures
- Device information such as:
- Device hardware model
- Operating system version
- Device memory
- Advertising identifiers
- Unique application identifiers
- Installed applications
- Unique device identifiers
- Device usage data
- Browser type
- Keyboards installed
- Language
- Battery level
- Time zone
- Information from device sensors – such as accelerometers, gyroscopes, compasses, and microphones
- Information about network connections, such as:
- Mobile phone number
- Service provider
- IP address
- Device phonebook after gaining user permission
- Access to device camera and microphone
- Location information taken from the GPS sensor
- Snapchat installs cookies and other tracking mechanisms, such as: web beacons, web storage, and unique advertising identifiers
Snapchat also receives user data from third parties, such as advertisers, app developers, and publishers. This allows the company to form a more complete picture of your usage patterns and habits.
Telegram
Telegram is a popular internet messaging application, first launched in 2013. However, it began gaining popularity in 2020 after protesters in different countries around the world began using it to organize protests. By 2024, it is estimated that the Telegram will reach 1 billion users.
When using Telegram, you can access your account across different devices. This feature is convenient for users who own multiple computing devices and wish to view their Telegram messages whenever they go. But it also means Telegram will keep your messages on its servers, which makes them susceptible to data breaches.
Communications between your device and the Telegram server are encrypted. However, if you initiate a conversation with another user, you need to activate the “secret chat” option in order to encrypt it.
According to Telegram’s privacy policy, it collects a minimal amount of information about its users. This information, which includes email address, phone number, and username, lets you open a Telegram account.
Telegram does not employ regular tracking techniques to track its users across the internet. It is also aligned with the GDPR, which means it provides a high level of protection in relation to personal data.
One thing that raises privacy concerns about Telegram is the external parties with whom Telegram shares users’ information.
For instance, according to Telegram’s Privacy Policy, it “ may share your personal data with:
(1) our parent company, Telegram Group Inc., located in the British Virgin Islands, (2) Telegraph Inc., a group member also located in the BVI; and (3) Telegram FZ-LLC, a group member located in Dubai” (see Figure 9).

Figure 9 – Telegram may share its users’ data with business partners located in different countries | Source: Telegram.
Spotify
Spotify is the world’s most popular on-demand music and podcast streaming app. It collects different types of information about its users. While some data is necessary to open an account, it still collects a lot of extra personal details.
According to Spotify’s privacy policy document, it collects different information about its users. Aside from personal information for opening a user account. Spotify collects the following information:
- Search queries
- Streaming history
- Playlists you create
- Audio library
- Browsing history
- Account settings
- Interactions with other Spotify users
- Usage of third-party services, devices, and applications in connection with Spotify
- Content you provide when participating in Spotify promotions, such as contests or sweepstakes
- Users’ content posted to the Spotify Service, such as images, audio, text, titles, descriptions, communications, and other types of content
Spotify also collects various technical information about your devices and network connections, such as:
- URL information
- Online identifiers such as cookie data and IP addresses
- Information about the devices you use such as:
- Mobile device IDs
- Network connection type (e.g. WiFi, 4G, LTE, Bluetooth)
- Internet or ISP provider
- Network and device performance
- Browser type
- Language
- Information enabling digital rights management
- Operating system
- Spotify application version
- Information that enables Spotify to discover and connect with third-party devices and applications. Such as device name, device identifiers, brand, and version.
Spotify will also record payment information of users if they purchase items from Spotify’s online store.
X
X, formerly Twitter, is not among the 10 most downloaded applications in Q 2023. However, I chose to include it here because it’s one of the most popular apps in terms of monthly active users – over 245 million.
X requests different permissions from user mobile devices to function correctly. While some of these are needed for proper functionality and to provide some services, other access permissions could be used for tracking purposes. Here are the primary access permissions required by the X app:
- Precise location (GPS and network-based): Access to device location derived from GPS, WiFi networks, cell towers, and sensors.
- Contacts: Access to contact list information stored on the device to suggest connections and accounts to follow.
- Install widget: This permission allows the X app to install shortcuts on your mobile device’s home screen.
- SMS: Ability to read device SMS messages used for account verification during sign-up. This permission is also required if you use your phone number to connect with friends on the X platform.
- Microphone: Permission to record audio using the device’s microphone.
- Camera: Access to take photos and video using the device’s cameras.
- Device ID & Call Info: Access to unique identifiers for the device and call-related data.
- Network Connection: Ability to view WiFi and mobile network connections.
If you have already installed the X app on your Android device, you can find a list of the permissions the app uses in your phone’s Applications Manager (see Figure 10).

Figure 10 – Viewing the X application permission on Android devices.
Internet Service Providers (ISPs)
ISPs are our gateways to the internet. Without them, we cannot access the web. ISPs can record all their users’ web browsing history because they can easily intercept all traffic passing through their servers when customers use their service to access web content.
IP address tracking is the primary technique ISPs employ to track your online activities.
Government entities
Government agencies, especially security services and law enforcement, gather significant amounts of information about citizens. Superpower states, for instance, use different online tracking techniques to profile internet users on a global scale. They do this to solve different issues related to national security, make more informed decisions, predict future economic and social trends worldwide, and see how this affects their country.
Government agencies commonly use data collected by ISPs to discover the browsing history of a particular person. However, they can quickly expand their tracking through more advanced techniques to track an internet user’s online activity across the web and record their historical locations using smartphones’ GPS data.
Data brokers
Many people do not know about data brokers. These are companies specialized in collecting internet users’ personal information from different public sources. After that, they analyze and organize this data and then resell it to interested parties, such as government agencies, adversities, and other commercial organizations.
There are various ways data brokers collect user data, such as:
- Government records: These include all public records maintained by governments or other organizations, such as property records, court files, etc.
- Social media platforms: Personal information of social media users.
- Websites: Data brokers use specialized software programs called web scrapers to harvest large volumes of data from websites.
- Mobile apps: Many mobile applications sell their users’ behavioral and online web browsing history to data brokers directly.
What is a digital footprint?
There are vast arrays of personal data we leave behind while online. This is known as a digital footprint, and it can be utilized to distinguish an internet user across the web.
Anything an individual does online will leave a footprint, for example, visiting websites, sending and reading emails, playing online games, buying or selling products online, using search engines to find something, using artificial intelligence (AI) tools such as ChatGPT, registering for online courses and using mobile applications. All these are examples of online activities that can be used to track your web usage and create a detailed profile on you.
It is worth noting that people actively socializing on social media platforms have the most significant digital footprint. Those people tend to post a considerable amount of information about themselves on social media, such as posts, comments, shares, personal photos, videos, and geolocation data for the places they visit or intend to visit.
We can differentiate between two types of digital footprints: passive and active footprints.
Active digital footprint
These footprints are shared directly by the internet user or with their consent. For example, when posting photos and videos to Facebook and sharing your current location, you intend to allow others to see your data publicly.
Passive digital footprint
In this type, the external party, such as online stores, search engines, or social media platforms, collects information about your online activities without your knowledge. For example, websites deploy cookies to remember users visiting them and collect data about their website usage and behavior.
On the other hand, some social media platforms, such as Facebook and Twitter, spread their “Like” and “Tweet” buttons across the web. For example, when a user visits a website containing the Facebook “Like” button, Facebook will be able to track them without their knowledge as the button includes a JavaScript tracking code to track internet users’ activities across the web, even though, they are not signed into their Facebook account.
How does online tracking work
I mentioned several online tracking techniques, such as cookies, tracking pixels, search engines, social media tracking, and digital fingerprinting. Detailing how each tracking technique works needs another guide. However, I will conclude this article by discussing how the most popular tracking technique (digital fingerprinting) works.
Digital fingerprinting
Digital fingerprinting is the process of gathering different technical information about a user’s computing device and/or browser to identify and track them online.
Here is how it works:
When someone visits a website, a hidden script code (commonly Java or JavaScript) executes within the user’s web browser. It attempts to extract different technical details about the device and the web browser, like screen size, computer fonts, installed languages, operating system, and installed software versions, to name a few. These attributes are combined to form a unique digital “fingerprint” to represent that device online.
Now, websites store the fingerprint and link it to the activities performed during that browser session. When the same device is revisited later, its digital fingerprint is calculated again, and the new fingerprint gets matched against existing records. The user device is identified as a repeating visitor if a match is found.
Unlike cookies, fingerprints use the technical details built into a user’s device or web browser and persist even when cookies get cleared. Over time, sites can build extensive behavioral profiles, following users from site to site to compile their browsing, search, and purchase history by matching fingerprints across different domain names.
Fingerprinting has become a robust way for companies to circumvent cookie restrictions and provide consistent user tracking by leveraging their device’s technical attributes against them.
Pros and cons of having a digital footprint
There are many advantages to having a digital footprint:
- Get targeted ads: Monitoring your online web browsing history allows advertisers and websites to show you personalized content based on your preferences (previous searches, comments, subscribing services, following pages). For example, searching on Google for ways to reduce your digital footprint may display suggestions in addition to showing anonymity commercial services.
- Credit decisions: Financial firms increasingly use information collected from social media platforms and other websites to base their loan qualifications and decide their rating model for individuals. Having a good reputation online will help you in this direction.
- Background checks: Employers now leverage online sources more than ever to make their employment decisions. For example, prospective employees’ social media profiles are expected to be checked before hiring them officially. This allows employers to discover many things about their employees before hiring them.
- Legal proceeding: In lawsuits, evidence to support charges of unlawful behavior or to disprove claims of criminal behavior can be fetched from online data. For example, someone can prove their existence in a particular location by checking their smartphone geolocation data and social activities online (with the support of the tech platform).
These were some use cases of the benefits of having a good digital footprint; however, what are the disadvantages of publicly revealing too much information about your online behaviors?
- Privacy issues: As stated previously, many parties are interested in collecting digital footprints, often intending to invade user privacy. For example, search engines may display customized search results based on your previous searches. This can limit the effectiveness of searches and narrow results to only what matches the user’s existing online profile.
- Reputation: Many people change their ideas as they become older. For example, your past Facebook posts and Twitter tweets may contain extreme ideas about some issues or events that can impact your relations in the current time.
- Security risks: Hackers and other threat actors search for publicly available information using OSINT (open-source intelligence) techniques and tools. They aim to collect as much information as possible about their targets before executing social engineering attacks. Revealing excessive personal details online can enable these malicious actors and have severe negative security consequences.
How to know your current OS or web browser digital fingerprint
There are different online services to check your OS/web browser fingerprinting. These websites use JavaScript code designed to run within a user’s web browser. Upon loading the webpage, the JavaScript routing will run and collect various technical information about the visitor’s computing device and web browser.
Here are two popular ones:

Figure 11 – Check your device’s digital fingerprinting using EFF service | Source: Coveryourtracks.eff.org.
Conclusion
Our online behavior, web browsing histories, posted social media content, and web engagement leave extensive digital traces that form permanent digital footprints that can identify us across the web. Companies leverage such data trails to customize advertisements, make credit decisions, perform background checks, and more, while governments and cybercriminals pose other threats to personal data published online.
In this article, I attempted to outline the different types of user information collected by various online entities and how they can use this data to their advantage. In an upcoming article, I will discuss the main online tracking techniques in more detail and provide suggestions on how we can take measures to avoid them.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages