Hackers Abuse OAuth Apps in Microsoft Entra ID for Long-Term Persistence

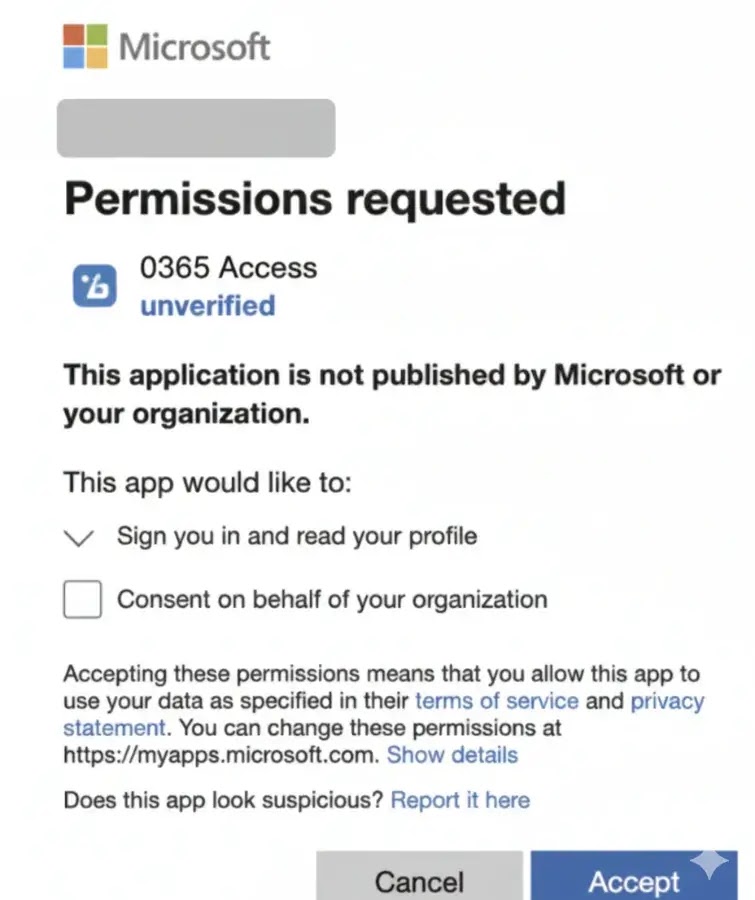
Hackers use OAuth apps in Microsoft Entra ID to stay inside networks for long periods. They create fake apps that look like normal business tools. These apps keep access even after password resets or account disables. Attackers trick users into granting consent through deceptive prompts.
Microsoft Entra ID powers authentication for Microsoft 365. App registrations create service principals across tenants. Attackers register malicious apps in their home tenant. They then push users to consent in target tenants. This grants broad permissions without raising alarms.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Persistence comes from app tokens that bypass MFA. Consent from high-privileged accounts locks in access. Redirect URLs steal tokens in phishing flows. Wiz research shows real cases blending with legitimate integrations. Proofpoint tracked 3,000 attempts in 2025 with over 50% success.
Attack Techniques Table
| Technique | Description | MITRE ATT&CK ID |
|---|---|---|
| Fake App Names | Use zero-width chars or lookalikes (0 vs O) | T1550.001 |
| Consent Phishing | Impersonate Adobe/DocuSign prompts | T1566.002 |
| Redirect Hijack | Steal tokens via custom reply URLs | T1539 |
| High-Priv Consent | Admin grants app full Microsoft Graph | T1098.003 |
Apps survive user disables. Tokens refresh independently.
How OAuth Persistence Works
Attackers register app in control tenant. They craft consent links for targets. Users see trusted publisher names. Approval creates service principal with scopes like Mail.ReadWrite.All.
Service principals live beyond user lifecycle. App-only tokens fetch data post-compromise. Detection misses them in user-focused hunts.
Common scopes abused:
- Files.ReadWrite.All
- User.ReadWrite.All
- RoleManagement.ReadWrite.Directory
Detection Rules
Hunt for suspicious OAuth apps:
- Low prevalence app IDs across tenants.
- Redirect URIs to external domains.
- Permissions mismatch app purpose.
- Recent consents from anomalous IPs.
Use Microsoft Graph API queries:
GET https://graph.microsoft.com/v1.0/auditLogs/directoryAudits
filter: activityDisplayName eq 'Add service principal'
Wiz OAuth Scout pipeline flags these at scale.
Defensive Configurations
Enable admin consent workflow. Block user consent for all apps. Review top 10 risky permissions quarterly.
| Setting | Path in Entra Admin Center | Recommendation |
|---|---|---|
| User Consent | Enterprise apps > Consent policies | Disabled |
| Admin Review | Authorization policies > Approval req | Enabled for risky |
| Service Principal Audit | Identity Governance > PIM | Weekly reviews |
Log consents in Microsoft Sentinel. Alert on app creation spikes.
Real-World Campaigns
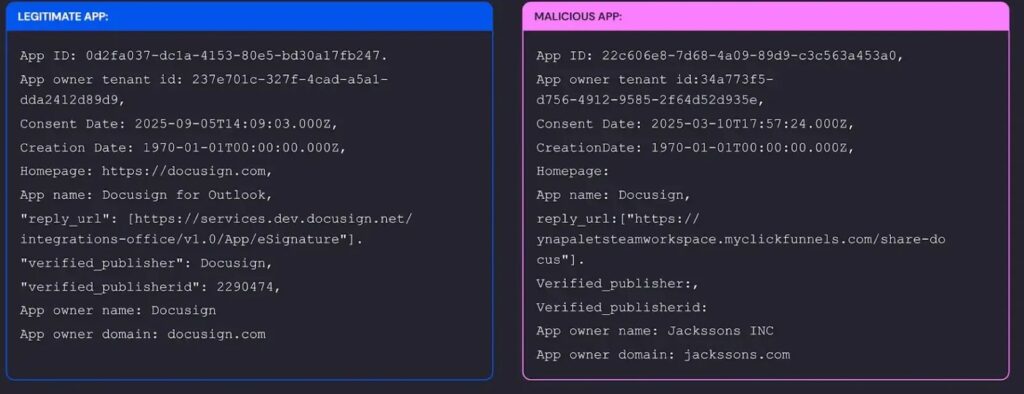
Proofpoint tied fake Teams/DocuSign apps to Tycoon phishing kits. Nearly 900 orgs hit in 2025. Wiz saw global App IDs reused maliciously.
Attackers theme apps as HR tools or integrations. Consent rates climb with social engineering.
Impact on Organizations
Compromised apps read emails forever. Exfiltrate OneDrive files. Manage groups silently. Recovery needs app deletion plus token revocation.
Entra ID cross-tenant access adds blast radius. Supply chain risks grow with app marketplaces.
FAQ
Apps use service principals with independent tokens, not user creds.
Application permissions like Directory.ReadWrite.All or Mail.Send.
No. Service principals persist separately.
Query audit logs for consents. Check appObjectId prevalence.
3,000 attempts, 900+ tenants, 50%+ success rate.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages