CharlieKirk Grabber Stealer Targets Windows Credentials, Cookies, and Session Data

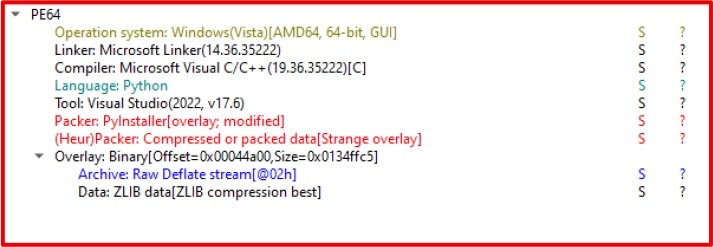
CharlieKirk Grabber infostealer hits Windows systems to grab login credentials from browsers. The Python malware arrives as PyInstaller executable. It kills browser processes, steals passwords, cookies, autofill data, and Wi-Fi profiles. Attackers exfiltrate everything via GoFile links sent to Discord or Telegram.
Cyfirma researchers found the modular builder lets operators customize C2 channels. The malware uses political branding from Turning Point USA for phishing lures. Delivery happens through emails, cracked software, game cheats, and social media. Once running, it profiles the victim machine and bundles loot into ZIP archives.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
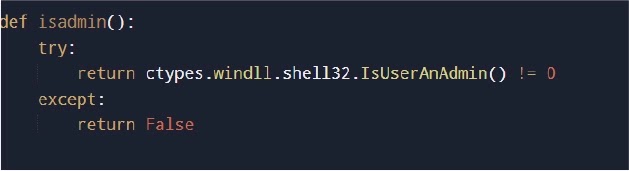
CharlieKirk lives off the land with Windows tools. It calls TASKKILL to stop browsers, NETSH for Wi-Fi passwords, and SYSTEMINFO for hardware details. PowerShell adds exclusions to Defender. UAC prompts may appear during execution. Data uploads fast before users notice.
Key Indicators Table
| Indicator Type | Value |
|---|---|
| File Name | CharlieKirk.exe |
| File Size | 19.58 MB |
| MD5 | 598adf7491ff46f6b88d83841609b5cc |
| SHA-256 | f56afcdfd07386ecc127aa237c1a045332e4cc5822a9bcc77994d8882f074dd1 |
| First Seen | February 2026 |
| C2 Channels | Discord webhook, Telegram bot |
| Exfil Site | gofile.io |
Block these hashes enterprise-wide.
Target Data Types
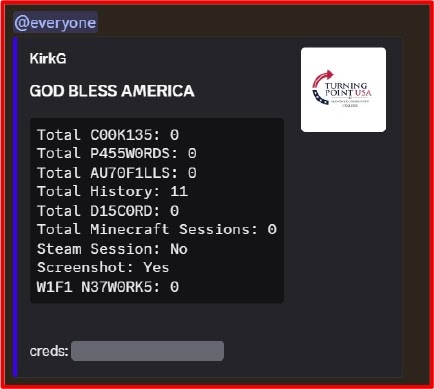
CharlieKirk steals comprehensively:
- Browser passwords (Chrome, Firefox, Edge).
- Cookies and session tokens.
- Autofill form data.
- Browsing history.
- Wi-Fi credentials via NETSH.
- Discord tokens for account takeover.
ZIP archive sent via HTTPS C2.
Attack Chain Breakdown
- Delivery: Phishing/cracked software drops PyInstaller EXE.
- Profiling: Grabs username, hostname, UUID, external IP.
- Anti-Forensics: TASKKILL kills browsers, unlocks databases.
- Collection: Enumerates all credential stores.
- Evasion: PowerShell adds Defender exclusions.
- Exfil: ZIP to GoFile, link via Discord/Telegram.
Smash-and-grab completes in seconds.
Living Off the Land Techniques
Uses only Windows binaries:
- TASKKILL: Stop Chrome.exe, firefox.exe processes.
- NETSH:
netsh wlan show profile name=* key=clear. - SYSTEMINFO: Hardware fingerprinting.
- PowerShell:
Add-MpPreference -ExclusionPath "C:\temp". - whoami /all: Current user privileges.
No suspicious DLLs or droppers.
Delivery Vectors
Common infection paths:
- Phishing emails with game cracks.
- Torrent sites offering premium software.
- Discord servers sharing “free” cheats.
- Fake Turning Point USA content.
Social engineering leverages political branding.
Detection Rules
Sigma/YARA signatures to deploy:
name: CharlieKirk Taskkill Browser Processes
conditions:
Image|endswith: '\taskkill.exe' and CommandLine|contains: 'chrome.exe'
Monitor GoFile traffic and Discord webhook POSTs.
Immediate Mitigation Steps
Protect endpoints now:
- Block execution from %TEMP%, %APPDATA%.
- AppLocker/WDAC for PyInstaller stubs.
- Monitor browser process termination events.
- MFA everywhere. Disable browser password storage.
- EDR rules for NETSH WLAN exports.
Rotate all potentially compromised credentials.
MITRE ATT&CK Coverage
| Tactic | Technique ID | Implementation |
|---|---|---|
| Discovery | T1082 | SYSTEMINFO.EXE |
| Credential Access | T1555.003 | Browser databases |
| Collection | T1560 | ZIP archiving |
| Defense Evasion | T1562.001 | Defender exclusions |
| Exfiltration | T1567.002 | GoFile.io |
Full kill chain mapped.
FAQ
Browser credentials, cookies, autofill, Wi-Fi passwords, Discord tokens.
TASKKILL.EXE terminates Chrome, Firefox, Edge processes.
Discord webhooks and Telegram bots over HTTPS.
GoFile.io file sharing platform.
User context sufficient. UAC may prompt.
Browser process kills + GoFile traffic + NETSH WLAN exports.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages