Lotus Blossom Hackers Breach Notepad++ Hosting Infrastructure

State-sponsored hackers from the Lotus Blossom group, linked to China, breached Notepad++’s official hosting infrastructure from June to December 2025. They targeted users in government agencies, telecoms, and critical sectors by redirecting update traffic to malicious servers.
The group first compromised the shared hosting provider. This access let them intercept and swap legitimate updates for malware. Victims focused on Southeast Asia saw the most hits, with spread to South America, the US, and Europe.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Notepad++ is a free, open-source code editor used by millions. Admins and engineers depend on it for quick edits on secure servers. Its lightweight design fits air-gapped systems where heavy tools fail.
Notepad++ lead developer Don Ho posted on the official site. He confirmed the hijack started in June 2025 and ended by December.
Palo Alto Networks Unit 42 released a full report. They detail the infrastructure compromise and payloads.
Attack Breakdown
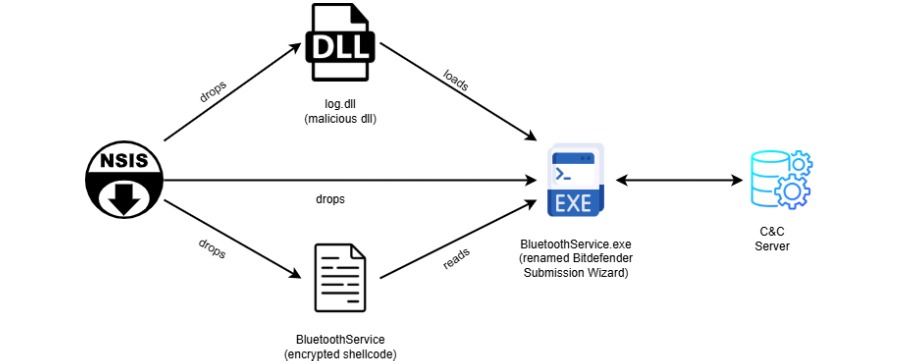
Hackers exploited weak verification in old WinGUp updaters. Victims downloaded fake update.exe files, triggering two chains.
One path used Lua scripts and EnumWindowStationsW API for Cobalt Strike beacons. The other sideloaded DLLs via legitimate BluetoothService.exe to drop the Chrysalis backdoor.
Chrysalis hid with Microsoft Warbird obfuscation and API hashing. C2 servers at 45.76.155[.]202 and 45.77.31[.]210 handled commands from August to November.
| Stage | Technique | Outcome |
|---|---|---|
| Access | Shared host breach | Traffic hijack |
| Delivery | Malicious NSIS installer | Fake updates |
| Path 1 | Lua injection | Cobalt Strike |
| Path 2 | DLL sideloading w/ log.dll | Chrysalis backdoor |
| Evasion | Warbird, API hash | Stealth persistence |
Targets Hit
- Government and telecom in Southeast Asia.
- Energy, finance, manufacturing globally.
- Cloud hosting and software devs.
- Limited to select users, not mass attack.
Beacons lit up seconds after downloads. Sessions ran for weeks, focused on recon.
Notepad++ Fixes
Version 8.9.1 adds certificate checks and signed XML responses. A new host with better security is live. Version 8.9.2 tightens verification further.
No ongoing activity reported. Update now and scan systems.
FAQ
Compromise of the shared host let attackers redirect updates.
China-linked APT group targeting Asia-Pacific high-value sectors.
All before 8.9.1, due to WinGUp flaws.
No, selective targeting of specific regions and sectors.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages