What is a VPN Tunnel? [All You Need to Know]
4 min. read
Updated on
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more
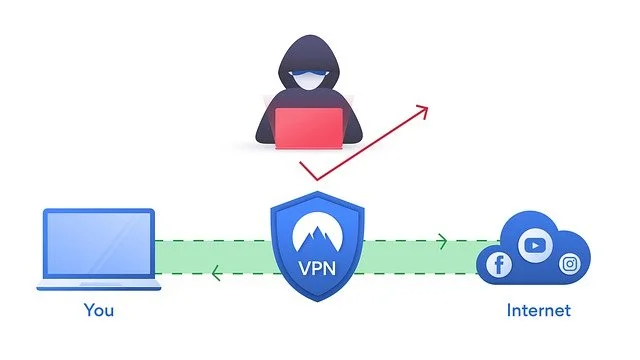
VPNs form a critical technology that ensures secure sharing of data on the internet.
Only a handful can explain how one works, even though most do have a basic understanding of its function and uses.
So, let’s dive deeper into what a VPN tunnel is, what it does, and what its types are.
VPN tunnel explained
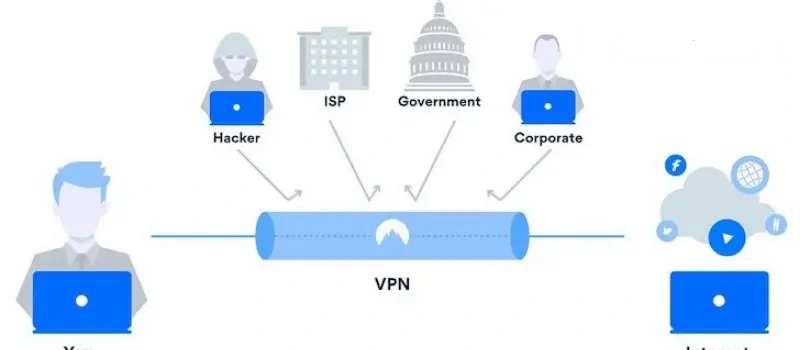
A VPN tunnel is the encrypted link that connects your computer or mobile device with an outside network. It shields your activities from invasive snooping and ensures your privacy.
Overall, the VPN tunnel refers to the encrypted connection the app creates.
Imagine an actual tunnel built from your device to the destination you want to visit. The data exchange happens inside the tunnel, and no one outside can see it.
Additionally, the data traversing inside the tunnel gets encrypted. So, even if someone would use a virtual hammer to smash the tunnel, the scrambled info would be useless to them.
How does VPN tunneling work
This technology functions through three main mechanisms:
Encrypting your traffic
A VPN encrypts the connection between your device and the internet, thereby protecting you from third parties snooping on you.
Hiding your IP address
While using a VPN tunnel, your traffic is funneled to a VPN server that hides your IP address. With your IP address concealed, no one can identify your location online. This change also prevents IP-based tracking.
Securing you on Wi-Fi hotspots
Encrypting your data and hiding your IP address help ensure your security when you use public Wi-Fi.
A VPN tunnel is put to work after you get yourself a VPN service. More specifically, it is set up after you’ve connected to the desired server.
After that’s done, your ISP can’t see anything of what you do online. Your IP address is hidden, while third parties get to see only the IP address of the VPN server.
Your online privacy and security are therefore ensured courtesy of the encryption technology and hiding of your IP address.
Most VPN services claim that they strictly maintain a no-logs policy, which implies that there’s no monitoring or storing of any data that can reveal your online identity or activity.
That said, you would do best to install a VPN from a reputable provider that has gone through an independent audit.
Now, with that said, let’s take a deeper look into the different VPN tunnel protocols:
Types of VPN tunnel protocols
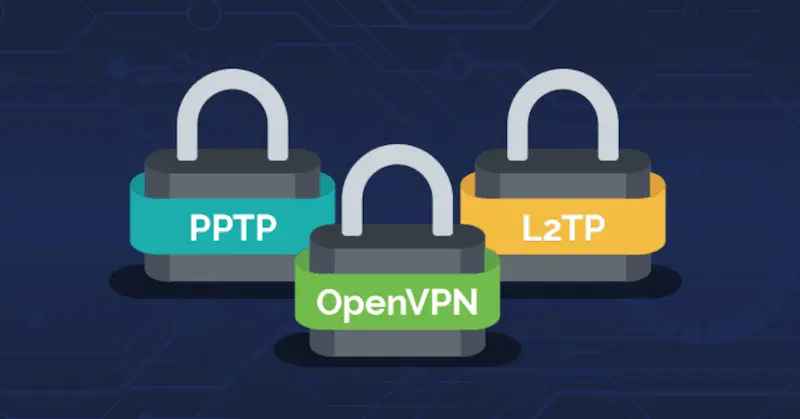
Your online privacy can’t be protected with the same effectiveness by all VPN tunnels. How strong a tunnel is typically depends on what type of tunneling protocol is used by your VPN provider.
The data encryption provided by some protocols may not be as strong as you would want them to be as they are outdated. Such a VPN tunnel fails to provide the desired level of security and privacy.
You would therefore do well to install your VPN from a provider that ensures a strong tunneling protocol. Here’s more on the top protocols.
- WireGuard – This is arguably the best and fastest tunnel protocol on the market. It uses superior encryption technology to protect your data. It comes with a lightweight code of only 4000 lines, which makes its auditing and implementation easy. WireGuard is also free of any of the shortcomings that are intrinsic to older frameworks.
- Open VPN – This protocol remains the most popular tunneling protocol. However, with the emergence of WireGuard, its dominance is under threat. Still, Open VPN continues to offer excellent speeds and security.
- IKv2/IPSec – A robust protocol that many reliable VPN services equip. It guarantees the highest protection while also maintaining quality performance. This protocol is also great at reconnecting users when they lose their connection.
Conclusion
Now you know whay a VPN tunnel is.
We explained the practical details of the technology, so you know what goes into protecting yourself online. We advise you to download a VPN from a trusted and reputable provider for the best service with the best protocols.
The provider must have a no-logs policy that ensures no monitoring or storing of your data. Keep yourself safe with a good VPN.







