ZeroDayRAT Spyware Targets Android and iOS Devices

ZeroDayRAT emerged as a new cross-platform mobile spyware on February 2, 2026. The tool attacks Android versions 5 through 16 and iOS up to version 26. Attackers sell it openly through Telegram channels with browser-based control panels.
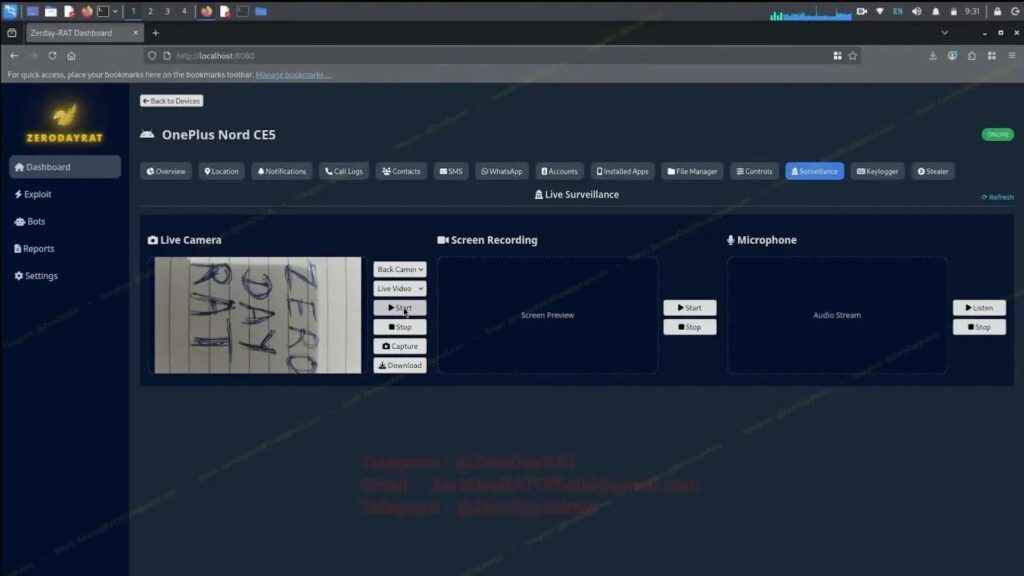
Operators monitor infected phones in real time. They access GPS location, notifications, SMS messages including OTP codes, live camera feeds, microphone audio, screen recordings, and app-specific keylogs. The platform lists registered accounts and supports crypto clipboard hijacking plus banking overlays.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
iVerify researchers discovered ZeroDayRAT while analyzing commercial spyware markets. No advanced skills needed after installation. Attackers deploy it through smishing texts, phishing emails, fake app stores, and social media links leading to malicious APKs or iOS payloads.
Spyware Capabilities
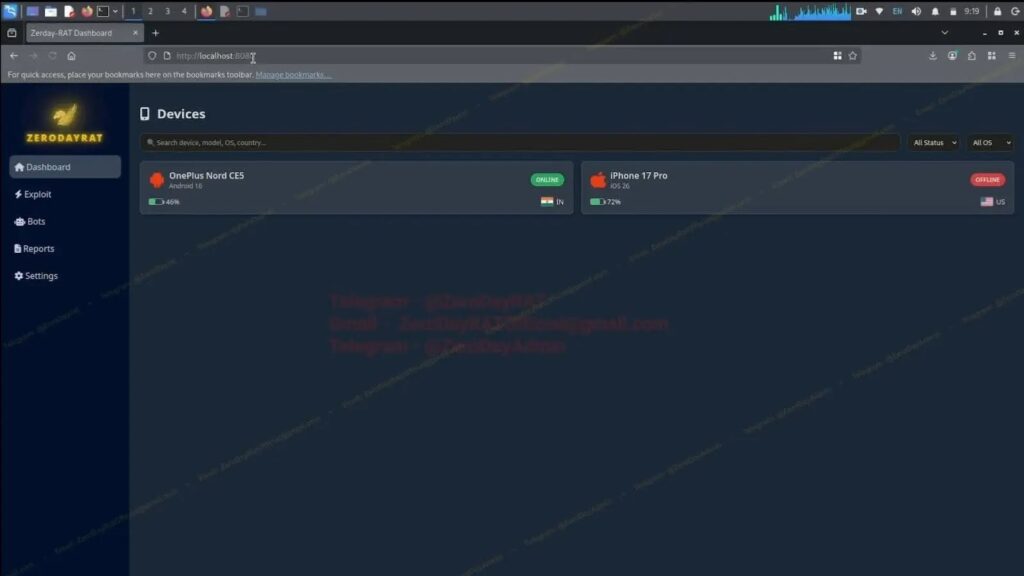
The web dashboard provides complete device control. Operators view device model, OS version, SIM carrier, app usage patterns, and location history. Live feeds show camera, microphone, and screen activity simultaneously.
SMS interception exposes banking alerts and two-factor codes. This enables account takeovers and financial fraud. Crypto wallet addresses get swapped during clipboard operations. Fake banking overlays capture credentials directly.
Infection chains create urgency through messages. Links lead to legitimate-looking download pages. Users install rogue apps granting accessibility services and full device permissions.
Supported Features
| Capability | Android Support | iOS Support |
|---|---|---|
| GPS Tracking | Yes | Yeskudelskisecurity |
| SMS/OTP Capture | Full access | Full access |
| Live Camera Feed | Real-time | Real-time |
| Microphone Recording | Continuous | Continuous |
| Screen Recording | Full sessions | Full sessions |
| Keylogging | App-specific | App-specific |
| Crypto Clipboard | Address swap | Address swap |
Delivery Methods
- Smishing texts with urgent download links.
- Phishing emails mimicking HR or IT departments.
- WhatsApp and Telegram shared malicious links.
- Fake app stores hosting trojanized applications.
- Social engineering pages requesting app installs.
Operator Dashboard
Device overview shows lock status, country location, and activity timeline. Multiple infections display simultaneously with India and US examples noted. Profiling speeds targeting decisions for high-value victims.
Once active, implants report to C2 servers automatically. Attackers pull full message histories and notification streams. Battery drain and permission prompts signal compromise.
Defensive Measures
- Install apps only from Google Play and Apple App Store.
- Disable sideloading on Android devices.
- Verify SMS links before clicking, especially urgent ones.
- Replace SMS 2FA with app-based authenticators.
- Monitor for unusual battery drain or accessibility grants.
- Organizations deploy mobile threat detection tools.
Enterprise Risks
“Corporate devices face highest exposure through BYOD policies. Stolen credentials lead to email compromise and data exfiltration. Rapid triage limits damage from suspected infections.” – iVerify
FAQ
Cross-platform Android/iOS spyware sold via Telegram with real-time control.
Android 5-16, iOS up to 26.
Smishing, phishing, fake apps through social engineering lures.
SMS/OTPs, GPS, camera/mic feeds, screen recordings, crypto wallets.
Battery drain, unknown accessibility services, sudden permission requests.
Mobile threat monitoring, app whitelisting, SMS 2FA replacement.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages