Advanced Crypto Mining Malware Targets Air-Gapped Systems

Sophisticated Monero mining malware spreads through external drives and infects air-gapped networks. Trellix researchers uncovered the multi-stage campaign in late 2025 that uses kernel exploits and self-healing processes. It propagates via USB devices with deceptive hidden folders and shortcuts.
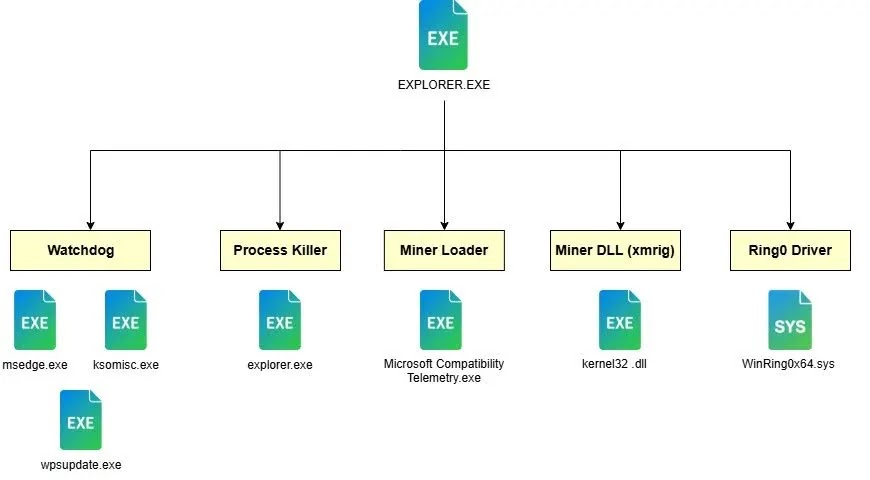
The infection starts with pirated office software bundles. Once running, it deploys controller and payload components. Watchdog processes ensure persistence by resurrecting terminated modules within seconds.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
The malware monitors USB insertions continuously. When drives connect, it copies itself automatically and creates hidden persistence mechanisms. This worm-like behavior breaches air-gapped systems through physical media transfer.
Malware Architecture
Controller handles lightweight monitoring and decision logic. Payloads execute resource-heavy mining and defense operations. Separation avoids security tool detection.
Self-healing mechanism:
- Watchdog monitors critical processes
- Termination triggers immediate resurrection
- Circular dependencies prevent full removal
- Multiple redundant components
Mining uses RandomX algorithm optimized for Monero. Kernel access boosts hashrate 15-50%.
Kernel Exploitation Details
BYOVD technique: Drops legitimate WinRing0x64.sys driver with CVE-2020-14979.
Privilege escalation: Gains Ring 0 kernel access through vulnerable driver.
CPU optimization: Modifies Model Specific Registers to disable prefetchers.
Mining boost: 15-50% hashrate improvement without custom drivers.
Signed vulnerable driver bypasses protections. No malicious kernel code needed.
Propagation Method
| Vector | Mechanism | Impact |
|---|---|---|
| USB Drives | Auto-copy + hidden shortcuts | Network lateral movement |
| External HDDs | Hidden persistence folders | Air-gapped infection |
| Pirated Software | Initial infection vector | Broad distribution |
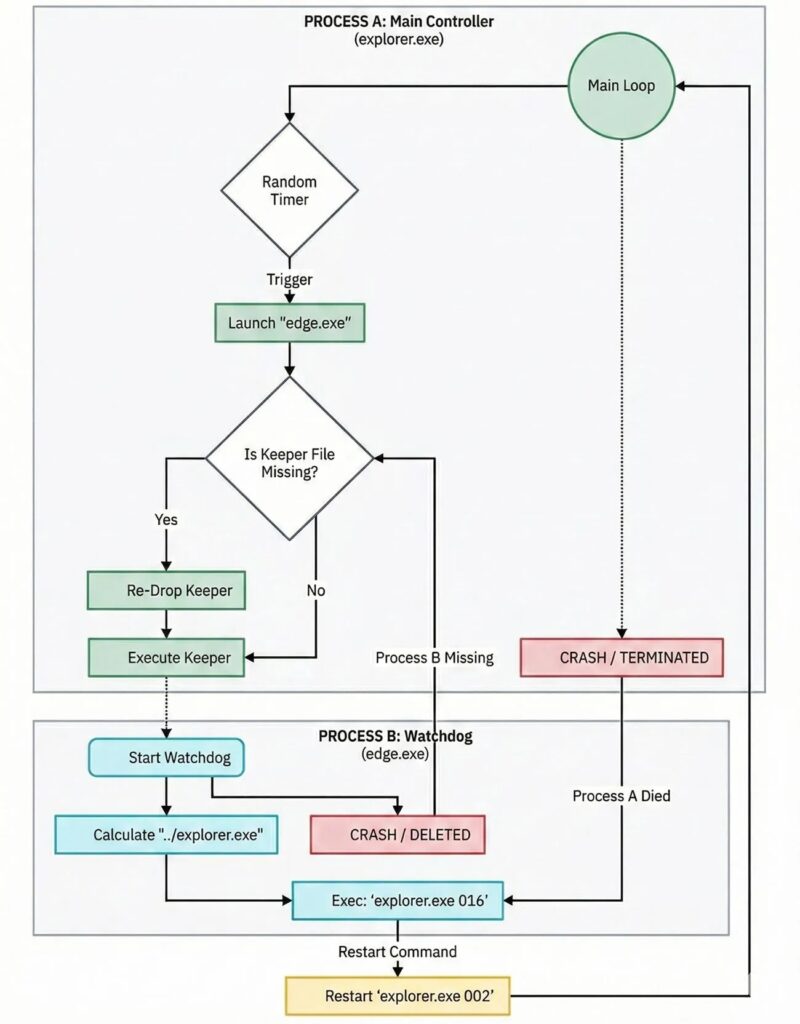
USB infection flow:
- Monitors WMI for device insertion events
- Copies malware to hidden system folder
- Creates deceptive LNK shortcuts
- Autorun.inf triggers on next insertion
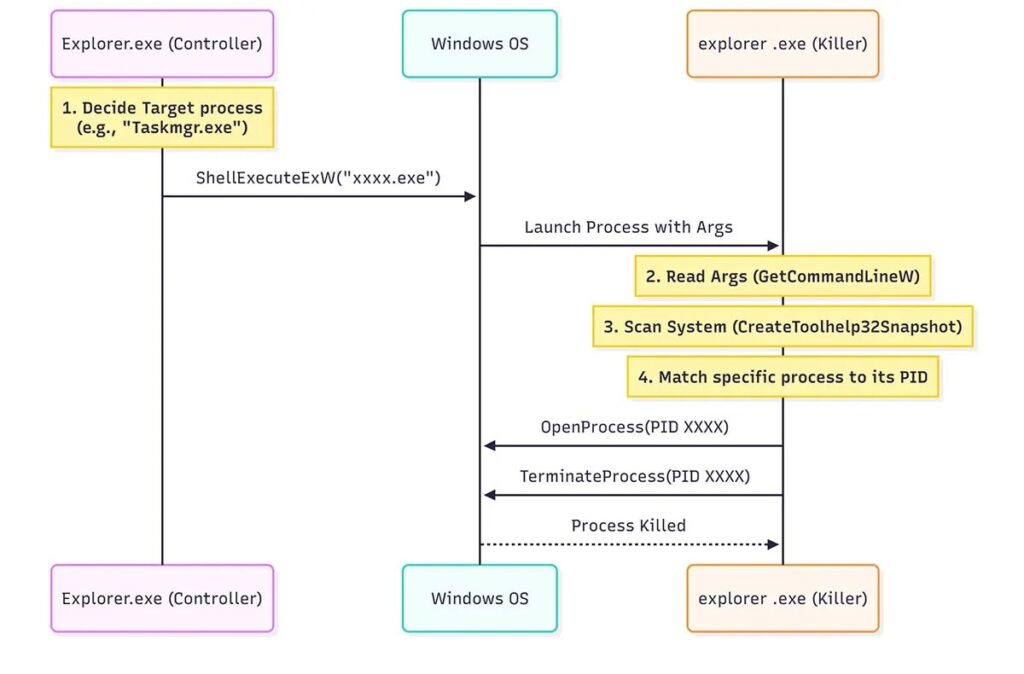
Defensive Capabilities
Malware actively terminates:
- Security software processes
- Windows Explorer (explorer.exe)
- Antivirus services
- EDR endpoints
Controller remains stealthy while payloads execute aggressive defense.
Temporal Controls
Hardcoded deadline: December 23, 2025
- Before: Full infection and mining
- After: Cleanup mode deletes files, terminates components
Suggests planned campaign lifecycle.
File Inventory Table
| Component | Purpose | Location |
|---|---|---|
| WinRing0x64.sys | Kernel access | System32/drivers |
| Controller.exe | Monitoring/decision | %AppData% hidden |
| Miner payload | Monero mining | Temp directories |
| Watchdog | Self-healing | Startup persistence |
| USB dropper | Propagation | Hidden autorun |
Detection Indicators
Process anomalies:
- explorer.exe termination events
- Unusual CPU register modifications
- WinRing0x64.sys loading
Network:
- Monero mining pool connections
- Consumer-grade pool IPs
File system:
- Hidden USB folders with LNK files
- Suspicious driver deployments
Protection Measures
Immediate:
- Enable Microsoft Vulnerable Driver Blocklist
- Device control policies for removable media
- Block WinRing0x64.sys loading
Preventive:
- Ban pirated software downloads
- Web filtering for mining pools
- USB device encryption/monitoring
Defender Actions
- Hunt for WinRing0x64.sys across endpoints
- Monitor USB insertion events
- Check CPU MSRs for mining optimizations
- Analyze explorer.exe crashes
FAQ
USB drives with hidden autorun folders.
CVE-2020-14979 in legitimate WinRing0x64.sys driver.
Yes, through physical USB media transfer.
Watchdog resurrects terminated components instantly.
Disables CPU prefetchers via MSRs; 15-50% hashrate boost.
December 23, 2025 triggers cleanup mode.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more





User forum
0 messages