Crazy Ransomware Gang Abuses Employee Monitoring Tool to Stay Hidden Inside Corporate Networks

Cybersecurity researchers have confirmed that a member of the Crazy ransomware gang abused legitimate employee monitoring software and a remote support tool to maintain persistence inside breached corporate environments. The attackers used trusted administrative tools instead of traditional malware to avoid detection and quietly prepare for ransomware deployment.
The activity was uncovered by researchers at Huntress, who investigated multiple intrusions where threat actors installed Net Monitor for Employees Professional alongside the SimpleHelp remote support client. By blending malicious actions with legitimate IT activity, the attackers maintained hands-on control over compromised systems for extended periods.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
According to Huntress, the same operator appears responsible for at least two observed incidents, based on overlapping infrastructure and reused filenames.
What Happened in the Attacks
In both cases, attackers gained initial access using compromised credentials, including SSL VPN accounts. Once inside, they did not immediately deploy ransomware. Instead, they installed legitimate software to quietly control the network and monitor activity.
The primary tools abused were:
- Net Monitor for Employees Professional
- SimpleHelp remote support client
These programs are designed for legitimate administrative and workforce monitoring purposes. However, when installed by attackers, they effectively function as remote access trojans.
Official Statements From Huntress
On how the monitoring tool was weaponized:
“Net Monitor for Employees Professional… bundles a pseudo-terminal (winpty-agent.exe) that enables full command execution. Threat actors leveraged this capability for hands-on-keyboard reconnaissance… effectively turning an employee monitoring tool into a fully functional RAT.”
On evidence linking the intrusions to the same operator:
“The same filename (vhost.exe) and overlapping C2 infrastructure were reused across both cases, strongly suggesting a single operator or group behind both intrusions.”
On cryptocurrency monitoring configured by attackers:
“The SimpleHelp agent… was configured with keyword-based monitoring triggers targeting cryptocurrency wallets, exchanges, blockchain explorers, and payment platforms…”
How the Attack Chain Worked
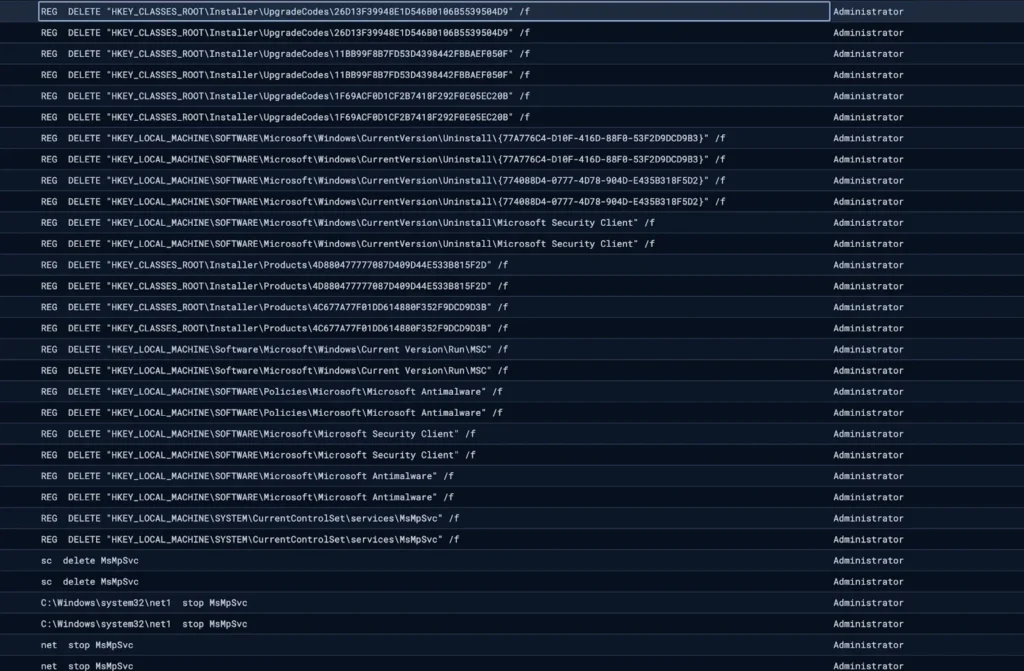
The intrusions followed a structured pattern.
1. Initial Access : Attackers entered the network using stolen or compromised VPN credentials.
2. Deployment of Monitoring Software: They installed Net Monitor for Employees Professional using standard Windows installation methods such as msiexec.exe. This allowed them to:
- Perform reconnaissance
- View desktops in real time
- Execute system commands
- Transfer files
3. Redundant Remote Access: To ensure persistence, the attackers installed SimpleHelp via PowerShell. In some cases, the executable was disguised using filenames such as:
C:\ProgramData\OneDriveSvc\OneDriveSvc.exeThis naming tactic helped the malicious software blend in with legitimate services.
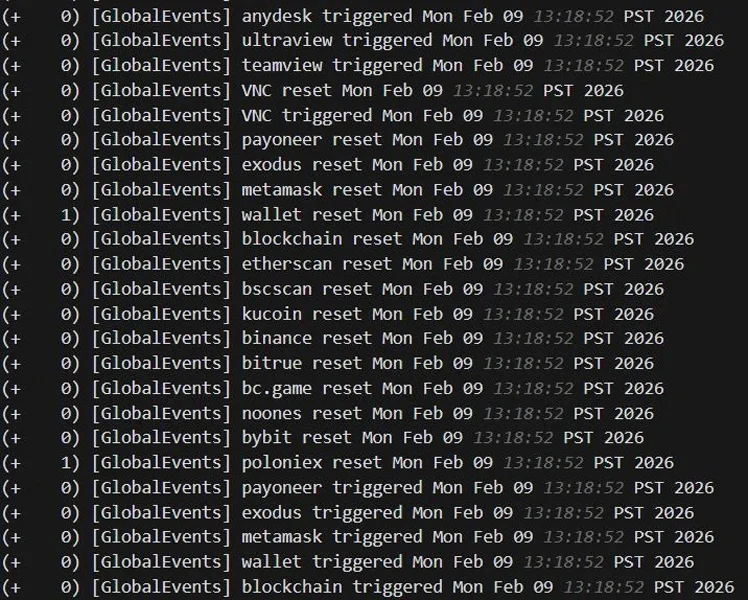
4. Surveillance and Preparation: The attackers configured monitoring rules inside SimpleHelp to track:
- Cryptocurrency wallet keywords
- Exchange platforms like Binance and KuCoin
- Blockchain explorers
- Remote access tools such as RDP and TeamViewer
This suggests preparation for ransomware deployment and potential cryptocurrency theft.
5. Ransomware Deployment: In at least one incident, the attackers proceeded to deploy the Crazy ransomware payload.
Tools Abused in the Intrusions
| Tool | Legitimate Use | How It Was Abused |
|---|---|---|
| Net Monitor for Employees Professional | Workforce monitoring | Command execution and remote control |
| SimpleHelp | IT remote support | Persistent backdoor access |
| Windows Installer (msiexec.exe) | Software installation | Silent deployment of monitoring agent |
| PowerShell | Administrative automation | Installation of disguised remote client |
Why Attackers Prefer Legitimate Tools
The abuse of legitimate software has become a growing trend in ransomware operations. Instead of dropping obvious malware, attackers use trusted administrative tools to reduce detection risk.
Benefits for attackers include:
- Blending into normal IT traffic
- Avoiding traditional antivirus detection
- Maintaining redundant access points
- Reducing forensic indicators
This approach is sometimes called “living off the land” because it relies on legitimate tools already trusted within corporate environments.
Security Recommendations From Huntress
Huntress advises organizations to strengthen defensive measures, especially around remote access.
Access Controls
- Enforce Multi-Factor Authentication on all VPN and remote services
- Limit administrative privileges
Monitoring and Detection
- Audit installations of remote monitoring and RMM tools
- Alert on unauthorized installation of employee monitoring software
- Monitor unusual PowerShell execution
Network Security
- Investigate outbound traffic linked to unknown monitoring tools
- Track suspicious filenames such as
vhost.exe
Organizations should treat remote management tools as high-risk assets that require strict oversight.
Frequently Asked Questions
Crazy is a ransomware operation observed deploying file-encrypting malware after establishing persistent access inside victim networks.
The breaches were enabled through compromised SSL VPN credentials.
The attackers used legitimate, signed administrative software rather than traditional malware, allowing them to evade standard detection methods.
Only one confirmed case led to ransomware execution, but infrastructure overlaps suggest the same operator was involved in both.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages