Reverse Proxy Security Concerns & How to Protect Yourself
9 min. read
Updated on
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more
A reverse proxy is vital for accelerating web and cloud applications. Moreover, businesses use it to secure critical systems against online attacks.
But there’s a problem:
Reverse proxies handle sensitive information like personal data, payment details, user logins, etc. While this improves service delivery, cybercriminals consider it a high-value target.
And you’ve got every reason to worry. Security breaches can paralyze your operations and expose you to potential lawsuits.
Luckily, we’re going to explore reverse proxy risks and ways to safeguard yourself. We’ll also share compliance regulations to follow to avoid legal tussles.
Ready? Let’s go!
Common reverse proxy security concerns
Although reverse proxies provide security, they’re vulnerable to attacks. Below are security issues they face worth your attention:
Attacks on reverse proxy servers
Reverse proxies are systems that sit between web applications and clients. They receive requests, analyze/change them, and forward them to backend servers.
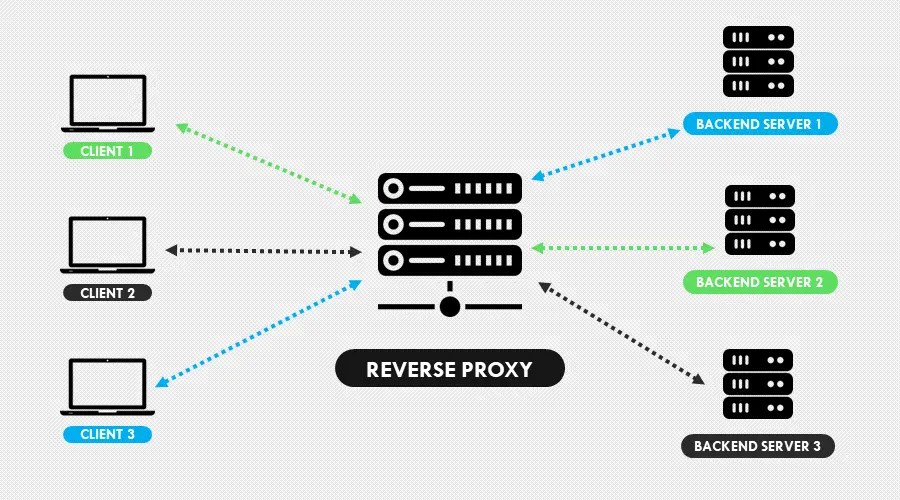
But as mentioned earlier, they handle sensitive information when processing queries. This makes them potential targets to cybercriminals that are after the data.
Other times, bad guys can invade such setups to disrupt business operations. Even worse, the intruders may hold organizations, hostage, until they pay a ransom.
But how does this happen?
Reverse proxy security vulnerabilities
The common ways for targeting reverse proxy servers comprise:
- Distributed denial-of-service (DDoS) attack: This cyber threat involves taking down an online platform by overwhelming it with unwanted traffic. Doing so prevents legitimate users from accessing services associated with the resource. However, this can happen due to improper configuration on the reverse proxy server.
- HTTP request smuggling: This is an attack where hackers use specially crafted queries to hoodwink a reverse proxy. When successful, the intruder can hijack client sessions and steal information.
- Session hijacking: In this technique, the attacker intercepts sessions between the client and reverse proxy. The approach allows the attacker to access applications on the target server.
- Risk of failure: Like other systems, reverse proxies can also fail. Such an incident can potentially expose the applications it shields to the public. Accordingly, bad actors will have it easy when launching attacks.
- Information leakage: Poor setup can also create loopholes, which hackers exploit. This occurs when the reverse proxy lacks security headers that hide information about the apps it shields. Moreover, using wildcard characters during configuration can have the same effect.
- Weak authentication: Reverse proxies authenticate users to ensure only legitimate clients access web applications. However, insecure protocols can give cybercriminals access to sensitive data.
The above reverse proxy related attacks come with dire consequences for your business. You risk data breaches, unwanted downtimes, and unnecessary costs for mitigating the threats.
The good news – we have a solution.
How to mitigate the security risks in a reverse proxy setup
You can reduce the risks by employing various measures to harden your setup. To start with, enforce rate limiting to block DDoS attacks from taking down your reverse proxy server.
The technique prevents a surge of requests from exhausting system resources. Additionally, include traffic shaping to streamline traffic inflow and outflow within the network.
Encrypt connections using secure socket layer (SSL) and transport layer security (TLS) protocols. The approach protects information in transit between clients and the proxy.
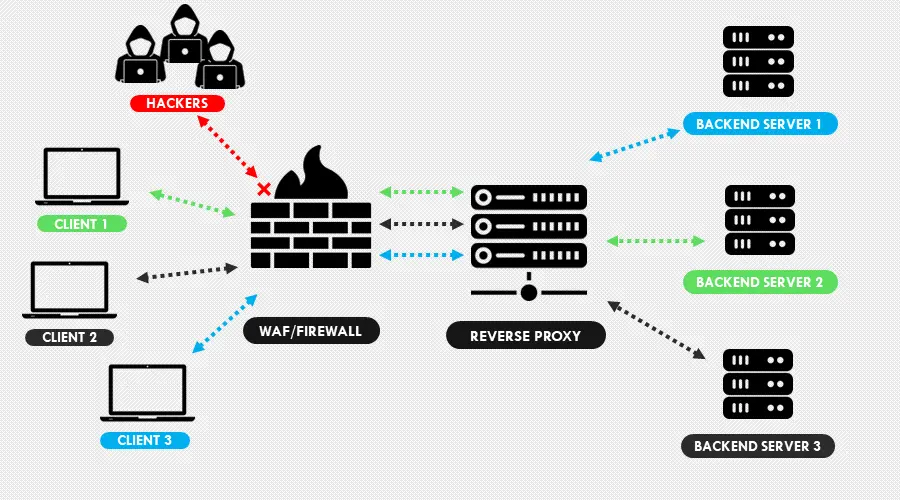
Furthermore, install a web application firewall (WAF) to filter our malicious requests from genuine traffic. The implementation additionally blocks intruders from accessing unauthorized data.
But that’s not all.
How to secure a reverse proxy setup?
Stopping reverse proxy security risks takes more than just mitigating the attacks. You need to secure your setup from the ground up to keep the threats low.
For that reason, we recommend the following:
Authentication/Authorization
Integrate strong authentication/authorization techniques to harden connections and block session hijacking. Start with access tokens to verify clients before permitting connections to the proxy.
Use OAuth 2.0 to grant secure access to the server without revealing user credentials. That way, intruders won’t find sensitive information when they eavesdrop on the connection.
Include Security Assertion Markup Language (SAML) to authenticate reverse proxy requests to the backend servers. The protocol also allows the swift processing of client requests without compromising security.
Secure backend servers
Encrypt connections to the backend servers using SSL/TLS protocols. This enables traffic to and from the proxy and internet to remain confidential.
Adding an internal firewall does come in handy here as well. Configure it to limit critical areas of your system from unauthorized persons.
You can further enhance the setup by including role-based access controls (RBAC). The measure restricts vulnerable areas of your system to trusted individuals.
Moreover, regularly update apps and software running on your servers. This undertaking brings bug fixes and security patches to protect your setup adequately.
Intrusion detection/prevention system (IDS/IPS)
This tool monitors your server for suspicious activities and security policy violations. Should there be any, it alerts system administrators about a looming threat.
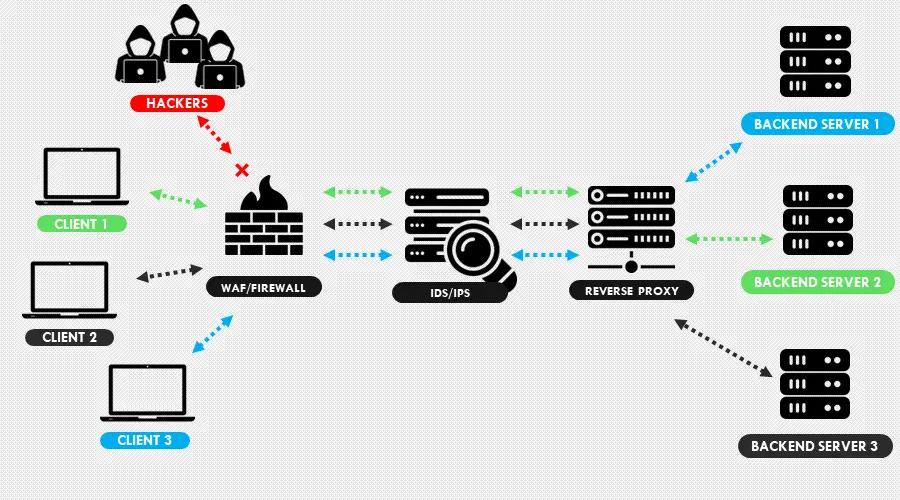
A perfect IDS/IPS setup requires a firewall as the first line of defense. Its inclusion assists in filtering malicious traffic when responding to cyber threats.
Furthermore, you can include machine learning to boost effectiveness against attacks. Such a combination prevents flagging legitimate clients by likening them to cyber criminals.
Perform vulnerability scans
Conduct regular vulnerability tests to determine security weaknesses in your system. You can do this using your in-house team or through bug bounty programs.
Make sure you accelerate your team to fix any issues that you discover. Once done, rerun the tests to confirm you’ve successfully resolved the risks.
What if there’s an easy way out?
Use third-party security solutions
Keeping your reverse proxy secure isn’t an easy walk in the park. It costs time and money to keep up with emerging threats.
Luckily, you can offload all that work to third-party security providers. The industry leaders include Cloudflare, Sucuri, Amazon Web Services, etc.
Such vendors offer robust solutions to protect your setup against external threats. These include DDoS, zero-day attacks, SQL injections, HTTP request smuggling, etc.
And the numbers don’t lie:
Cloudflare is on record for stopping the world’s largest DDoS attack. The threat originated from multiple botnets, peaking at 71 million requests per second (RPS).
Ordinary threats, which average 250,000 RPS, can take down enterprise systems. Now imagine the damage from something 28,000% larger.
Away from that, third-party vendors offer affordable and flexible pricing. The costs are super low that an in-house security team will seem unnecessary.
How about playing by the rules?
Reverse proxy security and compliance regulations
There are no specific regulations that touch on reverse proxy setups. But laws and industry standards exist which necessitate businesses to comply.
These revolve around how organizations should secure their systems and protect user data. Sometimes, the failure to comply may attract class-action lawsuits and hefty penalties.
HIPAA compliance
The Health Insurance Portability and Accountability Act (HIPAA) regulates the handling protected health information (PHI). It applies largely to organizations in the healthcare industry within the United States.
The law sets the standards for storing, processing, and sharing patient data. A significant part of the policy enforces strict confidentiality to prevent privacy breaches.
Accordingly, encrypt connections to and from your reverse proxy to prevent session hijacking. Likewise, employ OAuth 2.0 to reduce the risk of exposing login credentials.
Having role-based access controls on your backend servers is equally important. It will thwart intruders bypassing the reverse proxy from obtaining patient health data.
GDPR Compliance
The GDPR is the acronym for the General Data Protection Regulation. The law strengthens the protection of data and individual rights regarding personal information.
It requires businesses to seek consent from clients before collecting sensitive info. These include names of people, location history, physical addresses, online identifiers, and more.
GDPR also necessitates you implement concrete measures to protect the data. Besides that, it compels you to report data breaches publicly.
You need a firewall, IDS/IPS, and properly-configured backend servers to comply. Moreover, using RBAC will reduce the chances of personal data leaking through hacking.
Breaching this directive attracts fines of about $22 million or 4% of a company’s turnover.
PCI DSS
PCI DSS stands for Payment Card Industry Data Security Standard. It came about in 2004 through Mastercard, JCB, American Express, and partners’ joint efforts.
It outlines procedures for securing credit/debit card transactions from fraud. Furthermore, the policy recommends measures for safeguarding user financial data from breaches.
PCI DSS certification applies to businesses and organizations that accept payment cards. While there’s no legal mandate to comply, it’s a must-have.
Compliance requires you to have a firewall protecting your server installations. You also need to encrypt connections using SSL/TLS when processing transactions.
Organizations need to monitor the systems and conduct vulnerability tests regularly. Additionally, you’ll require a security management program for patching bugs and exploits.
Data breaches may attract severe consequences to a business. Some include fines from payment card issuers, lawsuits, and a total ban.
NIST guidelines
NIST stands for the National Institute of Standards and Technology (NIST). It’s a US government agency that develops policies for promoting science and innovation.
It provides guidelines to help federal agencies and organizations comply with other data protection policies. However, there are no legal requirements to adhere to NIST’s recommendations.
The framework entails the following:
- Identifying the data you need to protect.
- Establish protocols to safeguard the data.
- Conduct regular risk assessments.
- Formulate strategies to mitigate risks.
- Monitor agency-level risk depending on the protocols you’ve in place.
- Continuously monitor and improve your security controls.
Following NIST guidelines help you to leave no stone unturned. They’re for strengthening the approach toward securing your reverse proxy setup.
Summary
Every internet-powered business needs a reverse proxy to turbocharge its services. The tool is also essential for securing applications behind a web server.
On the downside, the sensitive information it processes makes it a hot target for cybercriminals. Possible online attacks can lead to data breaches, information leakage, unnecessary downtimes, etc.
Thankfully, you can avoid all reverse proxy security concerns by having a solid/secure setup. The good thing is we’ve shared tons of recommendations to achieve it.
All that remains is for you to implement the necessary measures to safeguard your business.







User forum
0 messages