SSHStalker Botnet Uses Legacy Exploits and IRC C2 to Hijack Linux Systems

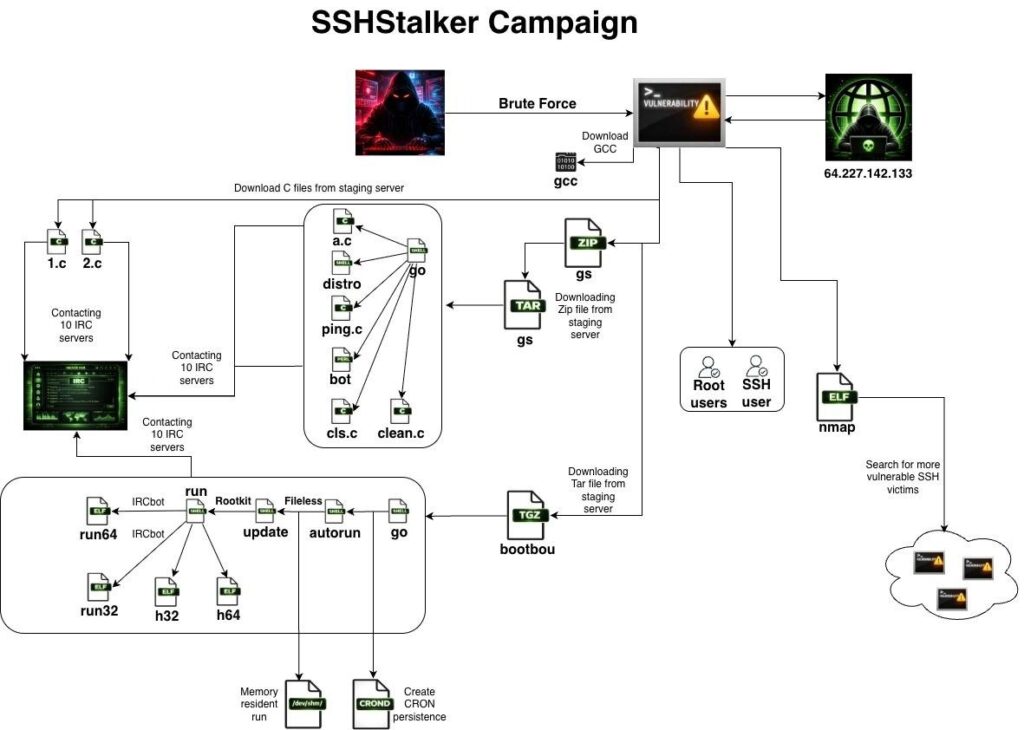
Cybersecurity researchers have uncovered a new Linux botnet operation known as SSHStalker, which targets exposed SSH servers and uses the classic Internet Relay Chat (IRC) protocol for command-and-control (C2). The botnet leverages a large catalog of old Linux kernel vulnerabilities to compromise systems, maintain persistent access, and enroll infected hosts into IRC control channels.
According to the research team at Flare, SSHStalker is a previously undocumented threat that blends IRC botnet mechanics with automated SSH scanning and legacy exploitation to build a large network of compromised Linux systems.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Flare said in its technical analysis “The toolset blends stealth helpers with legacy-era Linux exploitation… These are low value against modern stacks, but remain effective against ‘forgotten’ infrastructure and long-tail legacy environments,”
The botnet has been observed infecting thousands of systems by scanning for open SSH ports, exploiting weak authentication and unpatched kernel flaws from as far back as 2009. Once a host is compromised, SSHStalker drops a variety of IRC bots and persistence mechanisms to expand and sustain control.
How SSHStalker Works
The SSHStalker infection chain follows several key stages, combining outdated techniques with mass compromise automation:
- SSH Scanning and Brute Force: The botnet uses automated scanners written in Golang to probe internet-accessible Linux servers on port 22 and attempt access using weak credentials.
- Legacy Kernel Exploitation: Compromised hosts are further exploited using a catalog of dated Linux kernel vulnerabilities, including those from 2009 and 2010 families such as CVE-2009-2692.
- IRC Command and Control: After initial compromise, SSHStalker enrolls hosts into IRC channels hosted on public networks, where the botnets receive commands from remote operators.
- Persistence via Scheduled Tasks: The malware creates cron jobs that relaunch components every minute if terminated, ensuring long-term presence on infected systems.
Unlike many modern botnets that use bespoke C2 frameworks, SSHStalker relies on classic IRC because it is simple, resilient, and broadly interoperable.
Legacy Exploits Used by SSHStalker
SSHStalker’s exploit modules include multiple Linux kernel CVEs that date back over a decade. These flaws are no longer effective against modern Linux distributions, but they remain dangerous in legacy environments that still run older kernels.
Here are some documented kernel issues used in the botnet’s toolkit:
| CVE Identifier | Description |
|---|---|
| CVE-2009-2692 | Socket operations not initialized correctly, allowing NULL dereference exploitation |
| CVE-2009-2698 | Privilege escalation vulnerability in older kernel versions |
| Others (2009–2010 era) | Includes similar privilege escalation and root access bugs |
Legacy exploits like these remain effective in long-tail environments such as old virtual machines, abandoned servers, or embedded Linux appliances that haven’t been updated in years.
Botnet Architecture and Payloads
Once a server is compromised, SSHStalker deploys several components to establish control:
- Multiple C-Based IRC Bots: These connect infected hosts to IRC servers and join control channels.
- Perl IRC Clients: Used for redundancy and communication with C2 infrastructure.
- Log Cleaning Tools: Shell and C programs erase SSH authentication logs (utmp, wtmp, lastlog) to conceal intrusion traces.
- Keep-Alive Services: Scripts and cron jobs relaunch primary bot components within seconds if they terminate.
While many botnets focus on post-exploitation activities such as cryptomining, distributed denial-of-service (DDoS), or proxying traffic, SSHStalker’s researchers note that it currently shows persistent access without immediate secondary activity.
This dormant pattern suggests the compromised infrastructure may be used later for staging, testing, or other strategic purposes.
Expert Insight
Security experts point out why even old tools remain relevant:
“SSHStalker is a sharp reminder that old does not mean ineffective,” said Jason Soroko, senior fellow at Sectigo. “The campaign leans on IRC command-and-control, noisy cron-based persistence, and a pile of long-known Linux kernel exploits because a small but meaningful slice of internet-facing Linux systems still runs legacy software.”
This reinforces that outdated infrastructure remains a major security risk, especially where administrators have not kept systems patched for years.
Why This Matters
SSHStalker highlights several key security lessons:
- Legacy systems on the internet continue to be compromised at scale because attackers can still exploit dated flaws.
- IRC C2 communication remains useful to botnet operators who prefer stability and low-cost infrastructure.
- Mass SSH scanning campaigns can infect thousands of exposed hosts in days.
- Automated persistence mechanisms allow malware to survive cleaning efforts without complex evasion.
For organizations that manage Linux systems, especially cloud and virtual environments, exposed SSH services without strict credential policies or up-to-date patching represent a persistent threat vector.
Indicators of Compromise
Security teams should watch for:
- Unusual SSH login failures from repeated IP addresses.
- Cron jobs running suspicious scripts every minute.
- IRC processes or unexpected network connections to IRC servers.
- Modified utmp/wtmp/lastlog logs with gaps or inconsistencies.
FAQ: SSHStalker Botnet
SSHStalker is a newly identified Linux botnet that uses SSH scanning and IRC command-and-control to compromise and manage infected systems.
Research indicates around 7,000 systems were infected across regions including the United States, Europe, and Asia-Pacific.
The botnet’s operators leverage legacy kernel vulnerabilities because many legacy Linux systems remain unpatched.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages