Can A Network Admin See VPN Traffic? [All You Need To Know]
Network administrators typically work for businesses and organizations that need several computers to perform essential tasks.
They typically have access to configuration information for all the devices on the network, including routers, switches, firewalls, and servers.
In addition, they can monitor and analyze network traffic logs to identify issues and potential security threats.
That being said, strict policies and procedures regarding the handling of confidential information generally bind them.
However, if you’re concerned about your privacy, you may consider using a VPN. But does it work or can a network admin see VPN traffic?
Let’s break it down.
Can network admins see VPN traffic?
No. Network admins cannot see VPN traffic. That is if you use a third-party VPN. If you’re on a company’s corporate VPN, then yes, they probably do.
Here’s how traffic logs work:
When you are not using a VPN, network admins can see your internet traffic, including the websites you visit, the applications you use, and any data you transmit over the network.
Specifically, network admins can see your device’s IP address and all the requests sent from that device.
They can also see the amount of data you transmit and receive and potentially the content of unencrypted data packets.
Whether a network admin can see your VPN traffic depends on 2 major things:
- VPN quality – whether or not it can actually mask your IP and encrypt data
- the type of VPN you’re using – if you are on an organization’s VPN, the admin managing it most likely sees (and is supposed to) your traffic
Let’s explore what exactly a network admin can see.
? Work network admin
When you connect to a VPN using a work network, the network administrator can figure out that you are using a VPN, whether you’re using a VPN tunnel or bridge.
However, just because they know you use it doesn’t mean they know what you’re doing:
? Case 1: If the VPN is a work VPN bridge that links co-workers for easier data sharing, the network admin managing the VPN network is aware of your activities.
They’ll be able to see all the websites you access, the apps used, and the amount of data used. This is not a security concern because they’re supposed to manage the VPN network.
However, beware of everything you do on this network, and don’t access any websites you’re not meant to i.e. not work-related websites.
? Case 2: On the other hand, if you want to use a third-party VPN on your work network, the story is different. The network admin will see that you connected to the VPN, but that’s it.
Any other activity will be routed through the VPN server with the VPN’s IP, making it impossible for the admin to see what you’re doing.
That being said, even though admins can’t know what you do when you connect to VPN, they can block VPNs. They can use IP blocking, deep packet inspection, port blocking, etc.
Some organizations try to ban third-party VPN usage on their internal networks. Also, if VPN usage is strictly prohibited in your organization’s terms, don’t use it.
Your data is safe, but they can see you use a VPN, which can seem suspicious, especially when it’s not allowed.
? A general network admin
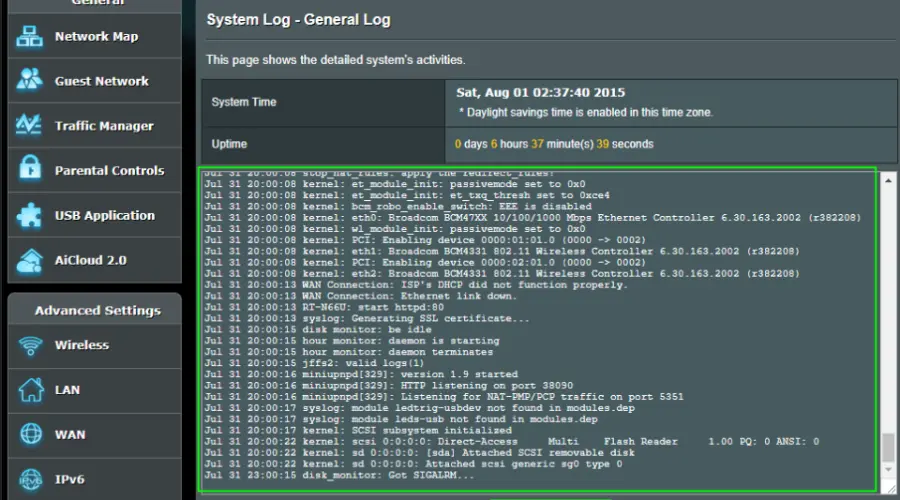
Most modern routers keep a log of connected devices, event timestamps, bandwidth used, and visited website URLs with their IP addresses.
The router’s owner or any other person with admin credentials can see the traffic logs of all devices connected. They just have to access the router management’s back end.
Nonetheless, a VPN helps to hide your data ? thanks to the encryption added to your traffic.
However, network admins can see that you use a VPN and the amount of data transmitted over the VPN.
That being said, they can’t see your browsing history or the specific data you’re sending over the internet.
Just like work network admins, a general network admin can block the usage of VPNs by blocking certain ports or protocols, or even specific VPN IPs.
How can the network admin monitor VPN traffic?
As mentioned, VPN admins can’t see traffic logs if you use a third-party VPN.
However, if you’re on a corporate VPN, they most likely monitor the connection. They need to ensure the security of the connection.
Whichever is the case, below are some of the methods network admins can use to monitor traffic and the type of information they can get when using them.
1. VPN logs
→ For VPN owned by the organization, the network admin may have access to the VPN log.
The VPN log contains inbound and outbound traffic, user connections, login times, IP addresses, and data usage across the VPN.
Network managers can use these logs to spot suspicious activity and pinpoint potential security risks.
→ On the other hand, they may only access the VPN logs indirectly if the organization uses a third-party corporate VPN service.
In this case, the VPN provider is likely responsible for maintaining the logs and providing access to their records.
The organization may have a service-level agreement (SLA) with the VPN provider that defines the terms and conditions for accessing the logs.
→ As for third-party VPN clients used by individual users, there’s no way the network admin can get ahold of the logs. Moreover, most of these services keep no logs, to begin with.
2. Traffic analysis
Network managers can use tools for traffic analysis to spot trends and irregularities in traffic. That way, they can detect that the devices connected use a VPN.
This can give away the fact that you use a VPN if you enable extra security measures. They may not directly detect your VPN’s IP, but they’ll be able to find irregularities in your activity that hint at VPN usage.
VPNs encrypt all the traffic sent over the VPN server.
However, before connecting to the VPN server, you have to connect to the internet first. This means that the VPN admin will most likely see that you’ve accessed the VPN.
They can also see the amount of data used and possibly for how long you’ve connected. However, when it comes to exact traffic information like the websites accessed, that will remain hidden.
3. Firewall logs
Using the firewall, network administrators can detect VPN activity and the port used by the VPN.
Ports are an essential component of the VPN tunneling process that ensures the connection is established.
However, even when they’re visible, if your VPN encryption actually works and the VPN hides your IP, your browsing activity is safe.
After the connection, the firewall logs all inbound and outbound traffic, including VPN traffic.
Once the admin identifies the ports the VPN protocols use, they can configure the network’s firewall or router to block those ports.
Nevertheless, advanced firewall log analysis is still needed because port blocking can also prevent non-VPN traffic.
4. Packet inspection
Network administrators can also examine individual packet data. Packets are small units of data containing information about your device, the websites visited, and actual traffic.
The process of packet inspection can reveal that you use a VPN in a number of ways:
? Operating system inconsistencies
Operating systems have specific packet values attached to them. If you connect to the VPN, these packet values can change.
Supposing the network admin knows the OS of the device you’re using, an inconsistency can determine VPN usage.
Note that almost all VPN servers run on Linux- or Unix-compatible servers.
? All packets with the same IP destination
People and computers typically utilize the internet to seek data from various websites.
These websites have unique IP addresses, but when you use a VPN, the packet sent will only head to the VPN server.
This is an obvious giveaway since it’s almost impossible to access only one IP address over a long period of time.
5. Quality of service (QoS) filtering
Network admins primarily impose a security measure through QoS filtering to minimize packet loss, network jitters, and latency over the internal VPN.
QoS has the ability to block unwanted or suspicious data traffic in its path to make it a vital component of a more secure network infrastructure.
Hence, traffic classification, traffic marking, and policing are the general stages of controlling traffic and preventing network collapse.
Consequently, this allocates weightier importance to specific data delivery types and routes other traffic into a monitored queue.
Network administrators look for the best practices to guarantee that their organization’s VPN traffic is secure as cyber threats continue to evolve.
This practice isn’t meant to monitor your activity, but to ensure the security of the network.
How to stay safe
When you use a third-party VPN tunnel, the network admin cannot see what you do online.
They can see you use the VPN, and may be able to block it, but that’s about it.
To make sure your data stays safe, enable the security killswitch on your VPN app.
This will ensure that you don’t send any traffic information over the internet until your VPN is able to re-establish a connection.
Note that it’s possible to block ports and VPN IPs, but you can’t block all of them. When you’re having an issue, the simplest fix is to switch to a different VPN protocol or change your server.
It’s best you use a VPN that offers a lot of servers, so you’ve got plenty of unblocked options.
Wrap up
If you use a VPN tunnel, the network admin can see you use VPN but can’t see traffic logs.
However, when on a company’s VPN, the admin that manages the VPN can see the traffic, but that’s not a security concern.
It is always a smart option to use a reliable VPN service and be conscious of the potential dangers of using public or unsafe networks.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages