How to Stay Safe and Secure When Using Social Media

Knowing when to use reputable VPN services like Private Internet Access while surfing the net is vital. But, there are times when your identity is exposed such as when you post information to your social media accounts.
These times are a back-to-reality situation as we do “normal” things on the web such as social media, email, and web browsing to do some online shopping.
Most people feel “safe” doing this type of work on the internet and tend to let their security guard down thinking that the bad guys don’t care what you’re posting to your Facebook account and could even care less about the photos of the family at the backyard barbecue.
This all falls into a category of security I like to call common sense security. The only protection you have from doing something that will compromise critical information about you, your family, and your friends is YOU.
There is no magic pill to prevent the inadvertent release of personal information, and there is no software program to prevent it either. It’s between you, the mouse or touch screen, and the keyboard. This is where you can be your own worst enemy unless you think before you act. The scammers and cybercriminals are just waiting to collect all that third-party data you broadcast and use it to their advantage.
Let’s focus on social media and build a checklist of what to do and not do so you can keep your identity protected.
Personal Identifiable Information (PII)
What do you put in your online profiles? PII is information that can be used to put context to just your name and give the reader info to be able to contact you directly and determine your location. Keep it clean and keep it simple. You should be the one to initiate contact, not the other person
Protect your work, hobby, and travel plans
Don’t release the names of other people from your inner circle. Family, friends, and co-workers deserve your respect and protection.
Photos can be a real problem. Other than your professional picture, be particularly sensitive to posting photos of your family. Information in the background can reveal where you live, if you’re on vacation and other risk information that can make you vulnerable. Remind family friends about this too.
Create Strong Passwords
The passwords you use for email and registration on websites should not be the same as the ones you use for social media. In fact, consider using a random password generator software program to develop all your passwords and have a unique one for each instance. There are free programs for this purpose.
Yeah, I know. How to remember those passwords can be a challenge? There are free programs that will store those passwords for you so you don’t have to have a photographic memory. Some anti-virus software has a password vault that comes with the subscription. There are other, independent free programs such as LastPass.
You put all these passwords in a protected vault for a reason. Do not share your password with others or give it away for any reason.
Social Media Security Settings and Privacy
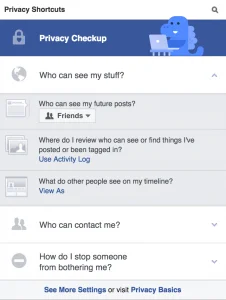
Did you know you have options for the visibility of your posts?
Find the location of those settings (try looking at the drop-down menu under your name) and study them.
Select the best option for your profile and search visibility. You may want to limit who can find you on the site.
Some social media sites give you the option to categorize your contacts and friends. Google + is well known for that. The information shared in each category can be individually tailored to only what’s necessary.
Always research friend requests to see if it is indeed someone you know or want to know and then verify via independent means that they sent you a request.
Keep your computer safe
Keep your anti-virus software subscription current and make sure you’re automatically updating changes to the threat database.
Even in social media, beware of links, downloads, and attachments that are offered to you. Verify who they are from and if they can be trusted.
Scammers use bogus apps, plug-ins, and phishing to get you to do something that leaves you vulnerable. A good rule of thumb is that if the deal looks too good to be true, it probably is. Skip it and move on.
Always look to see if the site you’re being asked to log on to is an HTTPS site or not before you log on and enter any sensitive data. The HTTPS designation along with a lock icon indicates transmission security and encryption are being used.
How does social media track your data?
Social media platforms and their partners record and monitor your data with cookies and tracking pixels. They also mine the information you openly provide on your account.
Additionally, they may collaborate with third-party data brokers and advertising networks. That way, social media can build an increasingly detailed user profile.
Yes, your data is used to improve the apps and websites from a technical standpoint. But it’s also a huge advertising money maker.
Ever wondered why you get eerily accurate advertisements for products?
Here’s more about how it’s done:
Tracking cookies
Every time your device loads content, these small text files are stored in the background.
They allow social media platforms and their partners to monitor your browsing habits. That includes the pages you visit, posts you like, and ads you click on.
Want to hear the scary part?
Different apps and sites can recognize cookies as long as they share the same advertising networks. That’s why you might see ads about camping on Twitter after visiting your favorite camping blog.
Tracking pixels
Also known as web beacons or tags, tracking pixels embed themselves within a site, app, or marketing email.
Basically, this pixel is an invisible image that gathers information about user behavior. It keeps track of your viewed web pages, opened emails, and bought products.
When the pixel is loaded, it sends data back to the host. This can include things like your IP address, browser type, and operating system.
According to Facebook, its tracking pixel is an “analytics tool that allows you to measure the effectiveness of your advertising by understanding the actions people take on your website.”
TikTok does the same thing and tracks users who don’t even have TikTok accounts.
Profile info
It should come as no surprise that social networks leverage user-provided information to expand your shadow profile. They use your account details, interests, and friends.
By analyzing this info, social media platforms categorize you into specific demographics for ad targeting and other purposes.
Data brokers
Data brokers collect information from your public profiles, loyalty programs, surveys, and endless online and offline sources.
They then sell this information to social media sites and any other outfit with the dough to purchase it.
How do social media companies use your data?
There’s an old saying that if you aren’t paying for a product, then you’re the product. That’s the price of using social apps and sites for free.
Here are some of the ways they profit from your information:
Selling your data
Social media companies may sell your personal info to advertisers. They also maintain a back-and-forth partnership with ad networks and data brokers.
In fact, Facebook began buying data from ominous-sounding brokers like Datalogix, Epsilon, and Acxiom in 2013.
These partnerships create a feedback loop of user information that grows into larger and more valuable data sets.
Selling your identity?
Facebook argues that it doesn’t ‘sell data’ in the sense of: Here’s everything we know about Bob Smith in an Excel sheet.
But it does admit to ‘selling access.’ That’s a fancy way of saying: You can use our highly targeted algorithms to reach everyone who meets your hyper-specific criteria, including Bob Smith.
This is called non-personally identifiable information. Privacy policies often contain this word and claim your privacy isn’t endangered because they anonymize your data.
The system and its algorithms might know a user is:
- 40 years old
- Likes fishing
- Uses Android
- Shops at Walmart
- Drives a Prius
- Accesses the internet with a certain IP address.
However, there isn’t a human at Facebook or their partners that know this is actually Bob Smith.
The trouble is, while Facebook might not give away identifying information or link it together, partners like Acxiom will.
The firm’s Audience Operating System allows advertisers to tie together your single identity even across different usernames.
Content ranking algorithm
Social media platforms also use your data to give you more of what you want. This is the algorithm at work.
When endlessly scrolling Twitter, the content you see, including advertisers and users you don’t follow is curated via the algorithm.
This analyzes the type of accounts you follow, your engagement, and trends or hashtags relevant to your interests. It’s all mashed together with your advertising data to present your personal timeline.
Technical improvement
Developers utilize data to gain mass insight into user behavior, engagement metrics, and platform performance.
By analyzing data patterns, platforms can:
- Identify trends
- Measure the effectiveness of features
- Make data-driven decisions to improve the overall user experience.
Still, it’s important to note that the specific data collected and its use can vary among social media platforms. Users should review each service’s privacy policies and settings to fully understand the situation.
How to stop social networks from collecting your data?
If you want to free your data from the spiderweb of social media tracking, here’s what you should do:
- Opt out and adjust privacy settings
You should limit the visibility of your posts, profile information, and personal details in your privacy settings. This will help prevent data brokers and miners from scraping your information.
Most social media platforms also provide options to control and customize ads. You can opt out of personalized or targeted advertising. This will reduce the amount of data collected about your preferences and interests. - Clear cookies and browser data
Regularly clear the cookies, cache, and history from your web browser. Social media platforms and other websites won’t have access to your stored data for tracking anymore.
- Try private browsing mode
Your browser’s private mode helps prevent the storage of cookies and browsing history. In turn, that makes it harder for platforms to track your online activities.
Even better, maybe switch to Brave – an entire browser designed to block ad tracking and maintain privacy. - Use a VPN
A VPN will take care of trackers that log your geographic location. It does this by encrypting your traffic and rerouting it through a server in another country.
The best providers give you the choice of almost anywhere in the world. For example, if you’re located in the United States, you can fool trackers into thinking you’re in Europe.
Furthermore, VPNs often come with ad blockers and safe search to automatically block tracking cookies. - Use dummy data
Even when you set your socials to private, the company itself still theoretically has access to them. One way to tackle this is to limit the personal info you sign up with.
Consider using an alias instead of your real name, for example. You could also change your birthdate and hometown, or avoid filling out biographical fields altogether, if possible.
You should also be mindful of the brands you follow if you don’t want to be linked to them for advertising. - Permanently delete your account
You might want to deactivate your social media accounts to reduce your digital footprint. However, this can be a confusing process. Moreover, your shadow profile will still exist, even when your public one is closed.
But before deactivating, you should try to remove your contact information first. That includes your mobile number, landline, or email address.
Additionally, you should consider wiping your friends and liked pages. - Request your data
Facebook and Twitter now have simple tools to download your own personal data. This might be useful when wiping and closing your account, so you can keep an offline copy.
However, the information is mostly limited to what you already posted. It doesn’t contain any of the background info compiled for tracking purposes.
Neither platform is cooperative when it comes to the EU’s GDPR legislation, which lets citizens request copies of all data.
Final Thought
Consider everything before you hit the enter key and post anything to social media! This information could go public at any time for any number of reasons. Hackers can gain access and publish it on the open web. The social media site allows third-party vendors access to posted information, and a configuration error just might release it to the wrong people. If you have any doubts about the sensitivity of the information you’re going to post, don’t post it.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more






User forum
0 messages