How Does A Reverse Proxy Add Security? [Explained]
6 min. read
Updated on
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more
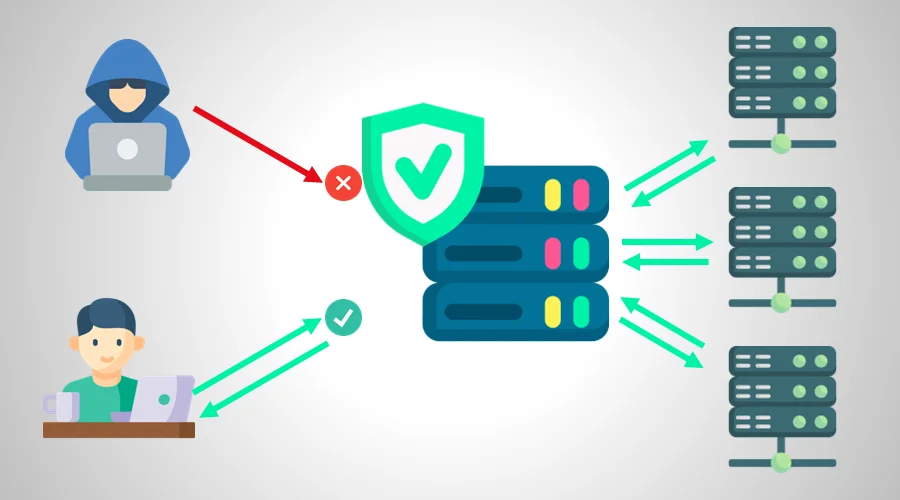
The security and performance of web applications are critical to every organization. Even a slight downtime can result in the loss of potential clients.
Luckily, you can avoid all the trouble by using a reverse proxy. It will act as a shield that safeguards your installations to stop intruders in their tracks.
But:
How does a reverse proxy add security? Find below what it is, how it works, benefits/downsides, and why you should get one.
Let’s check it out:
What’s a reverse proxy?
A reverse proxy is an intermediary that sits between the client and the origin server. It acts as a middleman that accepts and forwards requests to the appropriate backend applications. So, no user interacts directly with the systems, which results in better security.
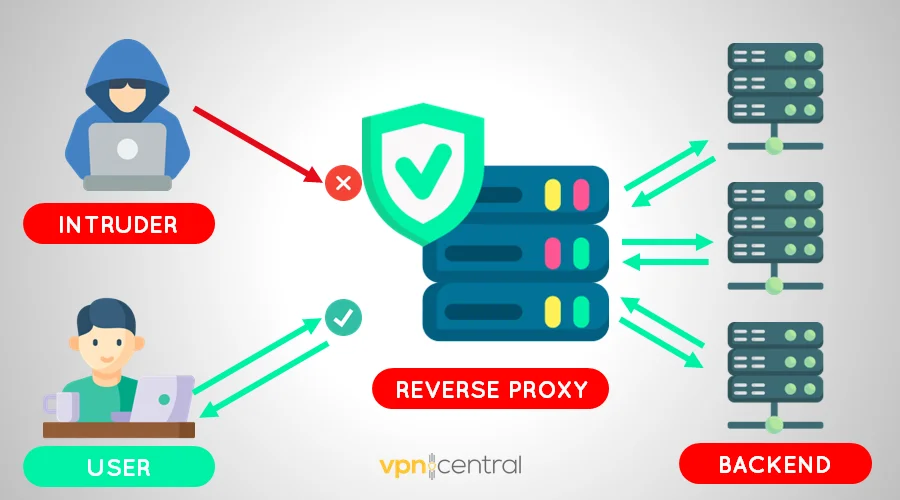
How does a reverse proxy work?
To understand how a reverse proxy works, let’s take a closer look at the process:
- Client sends a request: When you try to visit a website, your browser sends a request. This is like asking for a specific page or piece of information.
- Reverse proxy intercepts the request: It closely examines the client’s query. This is necessary to determine where to redirect the request.
- Request forwarding: The proxy sends the request to the relevant backend server for further processing.
- Server processes the request: The chosen server gets to work. It finds the information or page you asked for and gets it ready.
- Server responds to reverse proxy: The server sends the required data back to the reverse proxy.
- Reverse proxy delivers the response: The client receives the information or page requested earlier, completing the process.
- Caching (Optional): Sometimes, the reverse proxy caches the data. This way, if someone asks for the same thing, it quickly provides it without repeating the process.
The question is…
How does a reverse proxy add security?
Let’s delve into how it enhances application security. Here are several ways a reverse proxy achieves that:
Hides origin server IP
A reverse proxy can conceal the IP of the backend servers. Doing so prevents them from becoming a target to the attackers.
All incoming connection requests pass through it and get assigned the proxy’s address. This makes it challenging for attackers to deploy IP-specific attacks like DDoS.
Filters requests
You can configure a reverse proxy to filter all incoming requests. This can be based on predefined rules and signatures to eliminate unwanted queries.
You’ll find this valuable for blocking malicious activities. Moreover, it stops intruders from exploiting your applications.
SSL termination
This refers to the process of decrypting SSL-encrypted traffic using a reverse proxy. It also allows it to inspect and filter out potential vulnerabilities and threats.
It’s worth mentioning that the process is resource-intensive. As such, offloading the task from the backend server helps boost performance.
Implement WAF
You can integrate a reverse proxy with a Web Application Firewall (WAF) to harden security. This makes it superior at inspecting incoming requests for possible threats.
Some examples include SQL injection attacks, cross-site scripting (XSS) attacks, and others. You’ll appreciate better uptime of your web apps and smooth service delivery.
Content caching
Reverse proxies come in handy for caching static web content. These comprise text, images, videos, scripts, etc.
This minimizes the number of requests directed to the backend servers. As a result, you’ll experience faster speeds due to the reduced load.
But there’s more:
Caching provides some level of protection from malicious attacks. That’s because a reverse proxy serves cached content without querying the backend.
Load balancing
Load balancing is another indirect security benefit of reverse proxies. It can distribute traffic across multiple servers in the backend to streamline workload.
This reduces disruptions as a result of overloading a single server. Furthermore, it improves service availability, making it harder for attackers to cause disruptions.
Logging
Reverse proxies centralize logging and monitoring, providing valuable insights about an organization’s traffic. Accordingly, you can check for any suspicious patterns at ease.
It’s necessary for identifying security threats and mitigating the risks early. Sounds good, right?
But how does it differ from a forward proxy?
Differences between a reverse proxy and forward proxy
Both reverse proxies and forward proxies act as intermediaries in network communication. But they serve distinct roles.
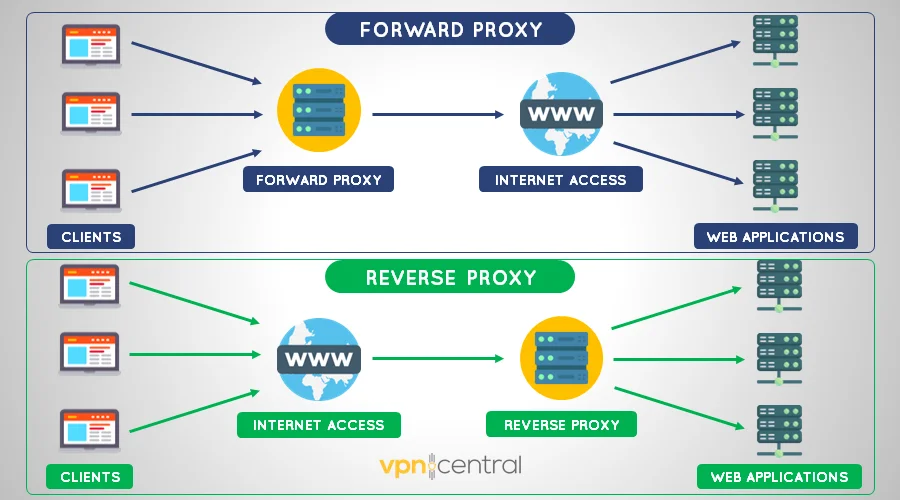
Find below the side-by-side comparison:
| Feature/Functionality | Forward Proxy | Reverse Proxy |
|---|---|---|
| Representation | Represents the client or group of clients. | Represents the server or group of servers. |
| Traffic Direction | Controls outgoing traffic from an internal network to the internet. | Controls incoming traffic from the internet to the internal network. |
| Primary Purpose | Provides centralized access and control, enforces security policies, and caches content. | Optimizes server load, enhances security, provides SSL termination, and caches content. |
| Identity Concealment | Hides the identity of the client. | Hides the identity of backend servers. |
| Usage | Used to control and monitor outbound traffic, enforce internet usage policies, or bypass regional restrictions. | Essential for load balancing, ensuring high availability, protecting backend servers, and accelerating web application delivery. |
Understanding their differences is crucial for making informed decisions about your security. As you can see, their purposes and benefits vary widely.
So…
Why should you use a reverse proxy
Let’s take a moment to understand why you should implement this technology:
- Enhanced security: As mentioned earlier, a reverse proxy adds an extra layer of security to the application infrastructure.
- Improved performance: Through features like content caching and SSL termination, reverse proxies can significantly speed up content delivery.
- Scalability and high availability: As your web application grows, so do the requests. Reverse proxies can distribute this traffic across multiple servers.
- Simplified infrastructure: Managing multiple servers can be a daunting task. You can consolidate your setup under a single system with a reverse proxy.
Benefits and drawbacks
While reverse proxies offer many advantages, they also come with other challenges. Here are the ones that you should consider.
Benefits
They’re as follows:
- Enhanced security through IP concealment and request filtering.
- Improved website performance with content caching.
- Scalability with efficient load balancing across servers.
- Simplified infrastructure management and SSL certificate handling.
- Centralized logging for better traffic analysis and anomaly detection.
Drawbacks
They include:
- Complexity in initial setup and configuration.
- Potential latency if not properly optimized.
- Maintenance overhead with regular updates and patches.
- Possible single point of failure if not configured for high availability.
- Increased infrastructure costs for high-end reverse proxy solutions.
Summary
How does a reverse proxy add security? As you’ve seen, it’s a robust shield that safeguards your web applications from bad guys.
Supercharging performance is another thing that it does best. It filters out unwanted requests while accelerating the delivery of content to users.
Overall, a reverse proxy is crucial in strengthening your organization’s systems. That way, you get to scale up without compromising on quality.
Before you go, check out this comparison between reverse proxies and VPNs. We also tested the top vendors on the market, which might interest you.








User forum
0 messages