How to Encrypt Your Internet Connection [The Ultimate Guide]
Protect your browsing traffic, email communications, and messaging
14 min. read
Updated on
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more

In the age of mass surveillance and internet user profiling, knowing how to encrypt your internet connection is essential. There are various parties interested in intercepting and monitoring your online activities, such as:
- Advertisers
- Tech giants
- Data brokers
- Internet service providers (ISPs)
- Governments agencies
- Cybercriminals
All these parties seek to leverage your web browsing data for their own interests. This makes understanding how to encrypt internet traffic critical for ensuring online privacy.
In this guide, I’ll show you various encryption techniques to secure your browsing traffic, email, and messaging.
How to encrypt your internet connection?
When saying we should encrypt internet connections, we’re not only aiming at encrypting web browsing activities. For instance, email and internet messaging (IM) are also used to transmit sensitive information and should be encrypted as well.
But before we begin talking about the best internet encryption methods, it’s essential to secure our entrance to the web. When we are at home, we use a Wi-Fi router to access the internet. So, I’ll begin by showing you how to secure it.
Secure home Wi-Fi network
A small vulnerability in your home router will make your internet connections vulnerable to different cyber attacks.
Here’s how to prevent that:
Change Wi-Fi SSID
The first thing we need to do is change the Wi-Fi SSID (Service Set Identifier).
Each manufacturer provides a default name for their SSID, typically their company name. Changing this name to something that doesn’t reflect your real name or point to the router manufacturer is advisable.
This makes discovering vulnerabilities related to your router more difficult for potential hackers.
Here’s how to go about it:
- Type your route’s IP address into a web browser to access its settings.
- Use your username and password to log in.
- Locate your router’s wireless local area network (WLAN) settings.
- Under SSID, write a new name for your Wi-Fi network.
Use a strong password
You should also use strong passwords to secure your router. Many users leave the default router manufacturer password, which is a terrible idea, as hackers can easily guess it and access your router admin panel.
Various websites list default routers’ dashboard passwords, such as:
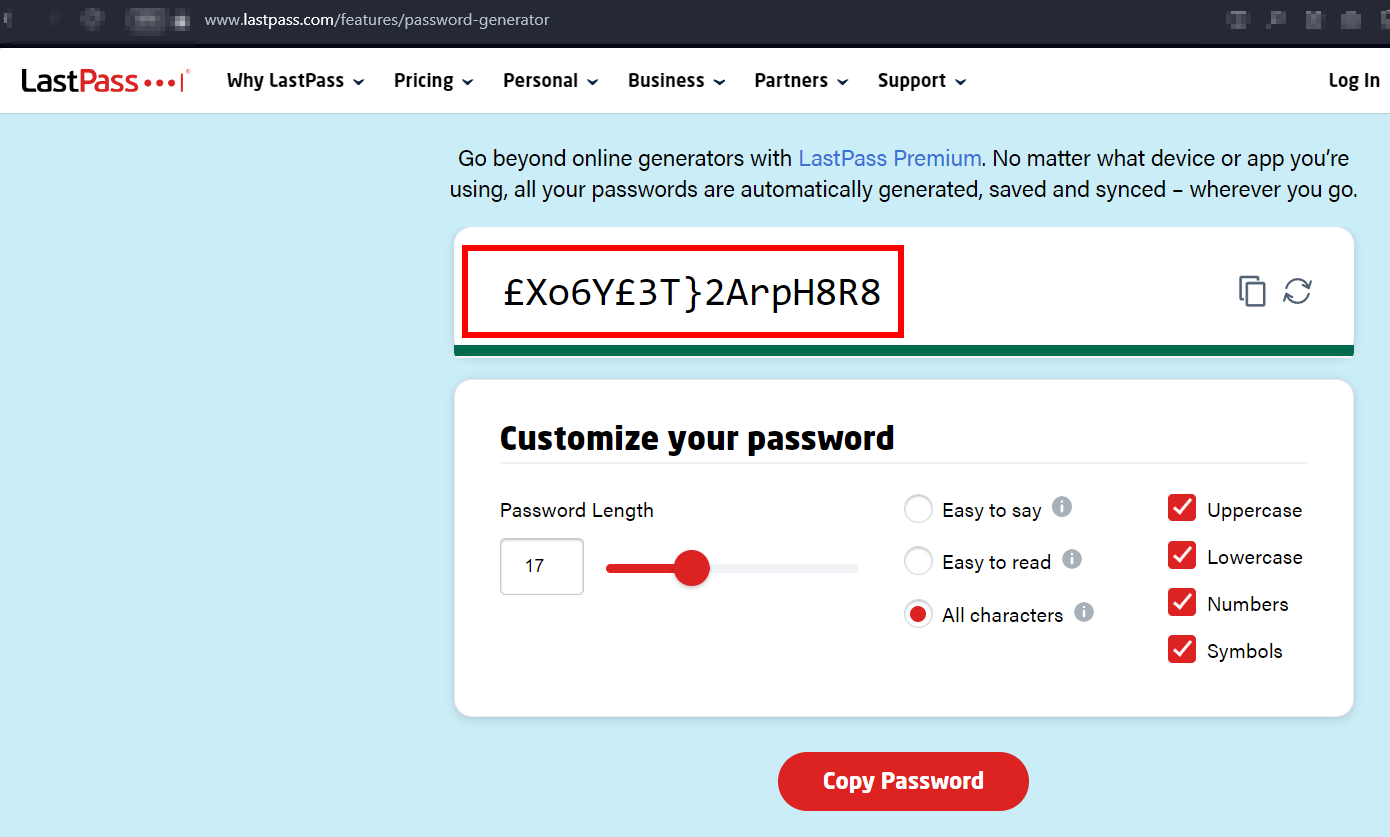
You can use a random password generator such as the LastPass online tool.
Turn on Wi-Fi encryption
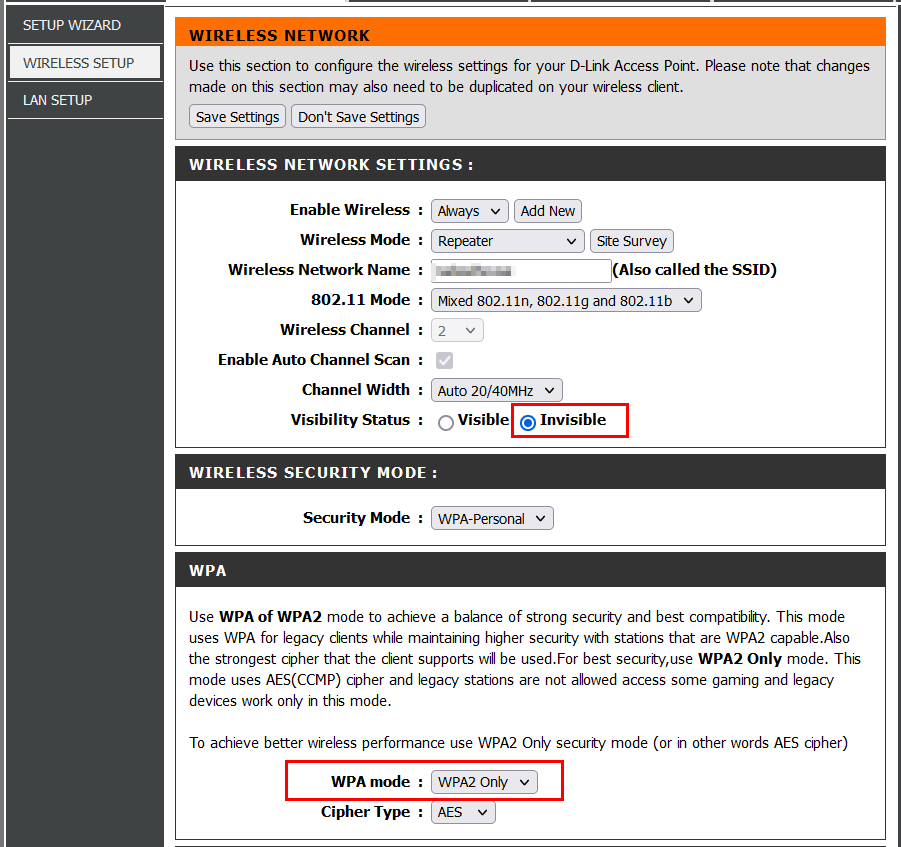
All modern Wi-Fi routers come with an encryption feature. Make sure to turn it on and select WPA3 or WPA2 as the encryption standard, as it provides enhanced security.
You can ensure your Wi-Fi is using WPA2 or WPA3 encryption protocol by going to the Wireless setup page on your Wi-Fi router.
Keep it current
Make sure to keep your home router firmware up to date. A router firmware is a piece of software program. It’s open to security vulnerabilities similar to any software program installed on your computing device.
Firewall
Some Wi-Fi routers come pre-shipped with a built-in firewall. If your router has one, make sure it’s turned on. If not, be sure to install a firewall on your computing devices to ensure optimal security.
There are different firewall solutions suitable for home users, such as:
Use a Virtual Private Network (VPN)
A Virtual Private Network (VPN) is a technology that creates a secure, encrypted connection over the internet between a user’s device and a VPN server.
All data passing via this encrypted tunnel is fully scrambled and can’t be read by unauthorized parties.
This lets you access the internet as if you were on a private network, even if you’re connecting via a public Wi-Fi network.
By encrypting your internet traffic before leaving your computing devices, a VPN prevents ISPs and other third-party observers from logging your online activities.
VPN will also mask your real IP address, showing only the VPN provider’s IP instead. This will add an extra layer of anonymity while browsing and increase your online privacy.
VPN security concerns
Despite the many benefits of using VPN services, it still comes with many drawbacks.
- It decreases internet speed. This is because traffic encryption and rerouting are bandwidth-heavy processes.
- The trust issue. When using a VPN service, you’re allowing all your traffic to pass via the VPN provider. For instance, many free VPN providers may record users’ traffic for commercial gain. They may also record your DNS queries, which reveal your visited websites.
- Not all VPNs offer the same level of security. This means your entire online security depends on the provider’s security measures, which could be vulnerable.
I won’t describe, or recommend, how to configure a particular VPN client because each company uses its own software that needs specific configuration. However, it’s worth noting the following points when selecting a VPN service:
- Security features: Select the VPN provider that uses robust encryption protocols (e.g., AES-256). It is also advisable to have access to different protocols like OpenVPN, WireGuard, or IKEv2.
- Usage policy: Choose a service with a no-logs policy. If the provider requests to keep your actual IP address for some time, understand who has access to your IP address and for what purpose.
- Server locations: Select a provider with servers in countries where users’ privacy is greatly respected. For instance, if your VPN’s servers are in Switzerland, this is far better for users’ privacy than having them in countries such as China, Russia, or even the US.
- Connection speed: Select the one with the best connection speed. This can be achieved by having different VPN servers in physical locations around you.
- Device compatibility: Ensure the provider supports different computing devices and operating systems.
- Easy to use: Choose a VPN with a friendly user interface. This allows non-tech-savvy users to use it easily.
Secure web browsing with HTTPS
HTTPS is an extension of the famous HTTP (Hypertext Transfer Protocol) that is used to securely transfer data over the internet. HTTPS works by providing an encrypted communication channel between a user’s web browser and the website they’re communicating with.
When surfing online, it’s critical to use HTTPS for these two reasons:
- Encryption: HTTPS encrypts data between your browser and the website you’re visiting. This prevents hackers from intercepting sensitive information, such as login credentials and banking details.
- Authentication: HTTPS guarantees that you’re connected to the right website and not a cloned, malicious version.
To ensure you’re using HTTPS when surfing online, you can check for the padlock icon in the address bar. Its presence means the visited website is using HTTPS.

It’s worth noting that major web browsers are now providing an option to enable only HTTPS mode by default. You can check the following guide on how to enable it for your web browser.
Still, you can use an open-source web extension to force all connections with a website to be over HTTPS whenever possible. The extension is developed by the EFF and is called HTTPS Everywhere.
Encrypt email communication
Email is the most used medium to exchange business and personal information. According to DemandsAge, people sent 347.3 billion emails every day in 2023. Emails may contain sensitive personal, health, financial, and business information that must be protected.
Encrypting these communications is essential for maintaining the confidentiality, integrity, and privacy of sensitive information for both individuals and organizations.
You can do this via two methods:
Using encrypted email services
These services handle the encryption of your communications for you. The most popular ones are Proton Mail, Tutanota, and Riseup.
ProtonMail
Proton Mail is a Swiss email service that employs end-to-end encryption.
Unlike popular email providers like Gmail and Outlook.com, Proton Mail utilizes client-side encryption. This means that email content and user data are scrambled before being transmitted to Proton Mail’s servers.
This effectively protects against data breaches and ensures no one (including Proton administrators) can not access users’ inboxes.
Tuta
Tuta, formally known as Tutanota, is an end-to-end encrypted email service that offers both free and premium subscriptions.
It focuses on providing secure and private email communication by encrypting the entire mailbox, including the subject line and attachments, to ensure user privacy.
Riseup
Riseup provides different online communication tools for people to interact freely.
It has fully encrypted email storage and provides a VPN service. However, the problem with this service is that you need to have an invitation from an existing Riseup user in order to register for a new account.
Encrypt email using PGP
If your email does not support encryption, you can encrypt your emails using PGP.
What is PGP?
PGP, or Pretty Good Privacy, is a tool designed to facilitate secure communication. It can encrypt and decrypt messages, authenticate them through digital signatures, and encrypt files stored on local drives.
PGP began as freeware, initially copyrighted under the GNU Public License. After a while, it was upgraded and transitioned into a commercial program employing the RSA and IDEA encryption algorithms.
While there’s still a free version accessible for personal use, you can’t use it for commercial purposes or in organizational contexts.
For this guide, I will use GPG for encrypting email messages. GPG is an upgrade of PGP. It uses the Advanced Encryption Standard (AES) algorithm of the National Institute of Standards and Technology (NIST).
There are various tools for implementing GPG; the most popular and easy-to-use one is the Gpg4win program.
How to use Gpg4win
First, we need to download and install the tool.
Go to Gpg4win’s official website, download the tool, and install it on your computer.
Keep in mind that this will also set up four additional components:
- GnuPG: This is the actual encryption program.
- Kleopatra: A certificate manager for OpenPGP and X.509 (S/MIME) and common crypto dialogs.
- GpgOL: An add-in for Microsoft Outlook providing email cryptography. Supports both IMAP/SMTP and MS Exchange servers.
- GpgEX: A plugin for Microsoft Explorer (file encryption).
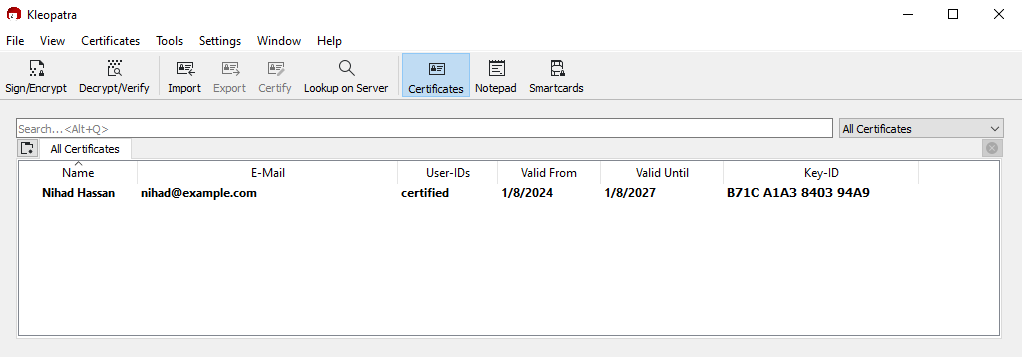
The first thing we need to do is create an OpenPGP key pair. We can do this using the Kleopatra tool.
1. Open the Kleopatra program, go to the File menu, and select the first option, New OpenPGP Key pair.
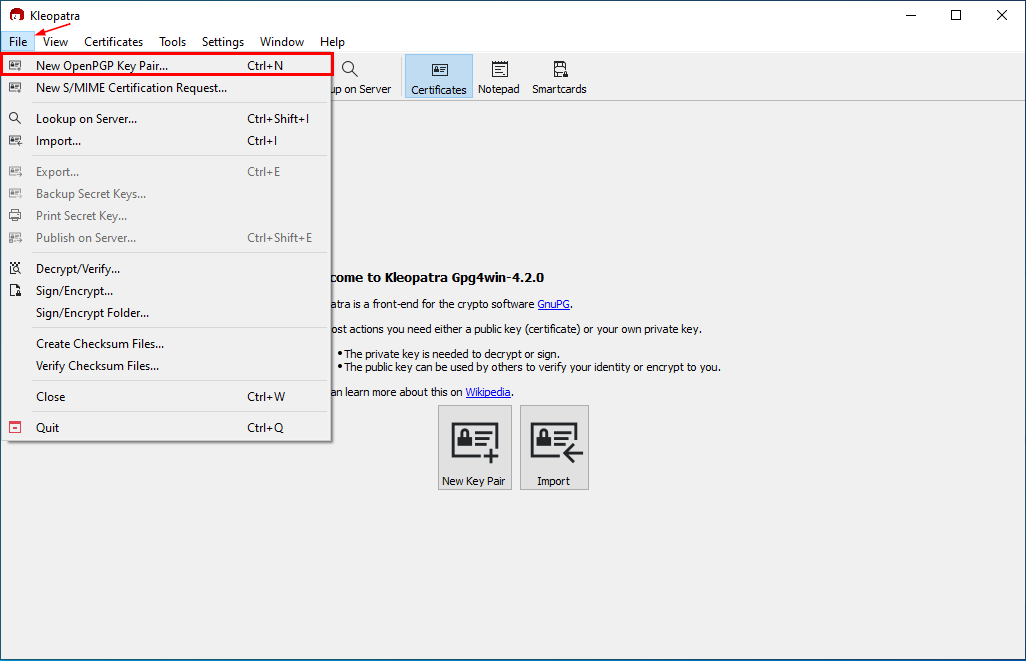
2. In the next window, you need to provide:
- A name for your key pair – it could be your name
- Email address
You can also protect the generated key using a passphrase. If we access the Advanced Settings, we can customize different technical aspects related to the generated key, such as:
- Key material
- Certificate usage attributes – expiration date, using it for signing and authentication, etc.

3. After providing these details, you’ll be prompted to enter a passphrase if you select to protect your key with this method.
4. After successfully creating a new key, you’ll get a success message.

5. The newly generated key pair will appear in the main Klepatra program.
How to use Pgp4win to sign/encrypt files?
After generating our PGP key pair, we can use it to sign/encrypt files in addition to sending and receiving encrypted emails.
1. To encrypt a file, all you need to do is right-click on it and select “Sign and encrypt”.

2. A new dialog appears; from here, you can select the key pair you want to use to encrypt/sign the file. You can also select the output location of the encrypted file.
3. You can also decide whether you want to protect the file with a password. After setting all attributes, click on “Sign/Encrypt”.

4. A success window will appear after encrypting/signing the file successfully. The newly generated file will have a different icon and a GPG extension:

Types of Internet Encryption
There are two primary types of encryption systems used to secure data on the Internet:
Symmetric encryption
We use the same encryption key in symmetric encryption to encrypt and decrypt data. Keeping the shared encryption key private is essential to maintain the system’s security.
I’ll demonstrate how symmetric encryption works using the following example:
Usage scenario: John and Sally want to communicate securely via the internet and want to use symmetric encryption to secure their transmitted data.
Key generation:
John and Sally create a secret key that only they know. This is the encryption key, and they’ll use it for both encryption and decryption.
Encryption:
When Sally wants to send a confidential message to John, she’ll use the secret key to encrypt the message. After encrypting it, the plaintext of the message content will turn into scrambled text, also known as ciphertext.
Transmission:
Sally sends the ciphertext message to John using a particular communication channel, such as the internet. If third-party observers intercept the message, they can’t reveal its contents without the secret key.
Decryption:
John, upon receiving the scrambled message, needs to use the shared secret key to decrypt the message, turning it back into its original state (plaintext).
Popular symmetric encryption protocols
There are different symmetric encryption protocols. The most used ones are:
- AES (Advanced Encryption Standard): We can use AES to encrypt data at rest and in transit. Wi-Fi networks are commonly secured using this protocol.
- Blowfish: This is an older symmetric encryption algorithm developed by Bruce Schneier. It has gradually been replaced with other modern algorithms, such as AES. But Blowfish is still used in some cases, like for data compression.
Asymmetric encryption
Asymmetric encryption (Also known as public key cryptography) uses a key pair for encryption and decryption. A public key is used for encryption, while a private key is used for decryption.
Although both keys are mathematically linked, we can’t derive one from the other.
Usage scenario: John and Sally want to communicate securely via the internet and want to use public key cryptography to secure their transmitted data.
Key generation:
Sally generates two encryption keys: a public key and a private key. The public key can be distributed publicly. However, the private key should remain confidential.
Encryption:
When John wants to send a confidential message to Sally, he needs to get her public key to encrypt the message.
Transmission:
John sends the encrypted message to Sally using any digital transmission medium. For example, the internet.
Decryption:
Now, when Sally receives the encrypted message. She needs to use her private key to decrypt it and retrieve the original plaintext.
Popular asymmetric encryption protocols
There are different Asymmetric encryption protocols. The most used one is RSA.
Rivest–Shamir–Adleman (RSA)
RSA is widely used for secure data transmission and digital signatures.
It’s also used in HTTPS and PGP email encryption. It’s worth noting that RSA is the preferred encryption algorithm used for key exchange in Public-Key Infrastructure (PKI). It securely exchanges symmetric keys between different parties over an insecure medium, like the internet.
What are their use cases?
Symmetric encryption is best suited for encrypting data on hard drives. This is because it requires less computational power to encrypt and decrypt stored data.
Asymmetric encryption is used widely to secure online communications. It can easily facilitate the initial key exchange (in a PKI system) and ensures the confidentiality and integrity of data during transmission.
Benefits of encrypting your Internet connection
There are several reasons why you may want to encrypt your internet communications, such as:
- Protect personal information: Encryption prevents external parties from intercepting your internet traffic. Your online communications may contain sensitive personal data, such as your personal, medical, and financial information.
- Protect financial information: People are increasingly using the internet for shopping and online banking. Securing your internet connection will prevent malicious parties, such as hackers, from capturing such important information.
- Use public Wi-Fi securely: Many people use public internet hotspots to get online. Without encryption, hackers can intercept internet communications passing through public Wi-Fi.
- Secure remote work: After the COVID-19 pandemic, more people are working remotely. Encrypting your internet connection is vital to secure work information when accessing company resources.
- Prevent cyber attacks: Encrypting internet connections will prevent many cyber attacks. For example, a Man-in-the-middle attack works by intercepting internet connections between two parties exchanging information. But with encryption, attackers will only see scrambled data instead of plain text.

- Ensure data integrity: Encytping internet connections will not only prevent unauthorized access to sensitive data. It will also prevent external parties from modifying your data while transmitting it online.
Wrap up
Now you know how to encrypt your internet connection to boost your online privacy and security.
Just follow the practical steps above and you can significantly reduce the risk of unauthorized access to your data.









User forum
0 messages