How To Know If Your IP Has Been Grabbed? [And What to Do]

IP grabbing is the act of someone obtaining and using your IP address after you click on a malicious ad or link on a website, app, or even email.
Trackers place short links that if you click on, they can acquire your IP address. Your IP can also be grabbed on online forums or during P2P sharing.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
Someone could grab your IP to spam you, steal your identity, sell the IP address, send you DDoS attacks, and so on.
We’ll discuss below how you can tell your IP has been grabbed and what you can do about it.
How to know if your IP has been grabbed
- DDoS attacks: The most common sign that your IP has been grabbed is an influx of sudden DDoS attacks. This manifests in an unusually slow network, unstable network, or a 503 service unavailable error when trying to use the internet.
- IP associated with cybercrime: furthermore, you can use IP lookup tools to check if your IP address was used for cybercrime recently. Not only that, but these tools also let you know of websites that have blacklisted your IP.
- Slow network: In addition to this, you may notice your internet connection gets unusually slower. It could mean someone else is sharing your bandwidth and IP address.
What to do if you click an IP grabber?
If you know your IP has been grabbed, it’s important to take immediate action, because the consequences can be serious.
Here are some steps that you can take:
1. Disconnect from the internet
Immediately disconnect from the internet. This will prevent the IP grabber from collecting any further information about your device or network.
2. Scan your device for malware
Run a full virus scan on your device to check for any malware or viruses that may have been installed as a result of clicking on the link.
3. Change your passwords
If you entered any login credentials or personal information on the website that the IP grabber redirected you to, change your passwords for all of your accounts immediately.
4. Contact your Internet Service Provider (ISP)
If you believe that your IP address has been compromised, contact your ISP and report the incident. They may be able to help you identify and mitigate any potential risks.
What can someone do with your IP address?
1. Determine your location
By grabbing your IP address, a tracker would be able to determine a rough estimate of your region but not your exact home address.
They can either use it for anything from targeted ads to blackmailing and even SWAT attacks.
2. Track your internet activity
Websites and online services can use your IP address to track your online behavior, such as which pages you visit or which products you search for.
Some web servers record IP addresses, so if a particular IP keeps going back to a certain site, the administrators would be able to monitor the user’s preferences.
Activity tracking can serve non-malicious purposes such as sending targeted ads toward you.
However, malicious users can put two or two together and use your activity as a means to find out more about you and your identity and eventually use the info to blackmail you or steal your identity.
3. Block access to certain websites
Some websites or online services may block access to users from certain IP addresses. This happens mostly to IP addresses that associate with spam.
This will happen if you or someone who’s used your IP in the past broke the terms of use of a website or service. The good news here is that most services let you appeal the decision, so you
4. Conduct a DDoS attack
In a Distributed Denial of Service (DDoS) attack, multiple devices send traffic to a single IP address to overwhelm the server and cause it to crash or become inaccessible.
5. Identity theft
It’s not uncommon for cybercriminals to hijack IP addresses to engage in illegal activities.
This could include purchasing illicit items and they might even attempt to frame you for these offenses.
However, these scenarios like hacking require more than just your IP address. Hackers can use your IP to get additional details about you from your ISPs through network attacks.
In the same vein, by the use of security software and safe online practices, you can prevent most of these attacks.
It’s worth noting that your IP address can also reveal extra information about you, such as your ISP, your device, and the type of internet connection you have.
How to stay safe
To stay safe and prevent anyone from grabbing your IP, you need to take certain necessary security actions.
First and foremost, make sure to update your apps, and antivirus software and run virus checks on your device before you go ahead with the guide.
Here are some tips to strengthen your security online:
1. Use a VPN
A VPN is a cybersecurity tool that encrypts your traffic and conceals your IP address, this in turn protects you from IP grabbers.
Follow the guidelines below to use a VPN:
- Subscribe and download a reputable VPN provider.
For safe browsing and anti-IP- leak features we recommend ExpressVPN.
- Launch the VPN app and log in with your credentials.
- Connect to any server of your choice.

- Then go ahead and visit any website you want.
Ensure the VPN of your choice uses 256-bit military encryption as that is the most secure algorithm for the best results.
❗Keep in mind that the VPN can’t stop you from clicking on an IP grabber. However, it will prevent your real IP address from being grabbed, which will in turn protect all your data.

ExpressVPN
Use ExpressVPN for secure browsing and top-of-the-line IP protection!2. Use Tor Browser
The Tor Browser uses a network of servers to encrypt and route your internet traffic through multiple nodes, making it difficult for anyone to track your online activity.
To set a specific country in a Tor Browser, you need to follow these steps:
- Download the Tor browser.
- Launch the Tor Browser on your device.
- Click on the folder on your device where the Tor browser is located to open.
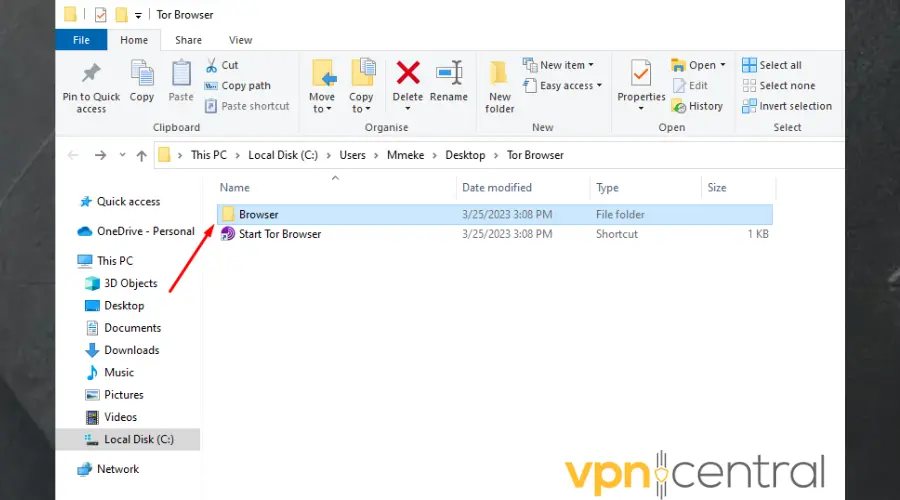
- Inside this folder, double-click on the TorBrowser folder.
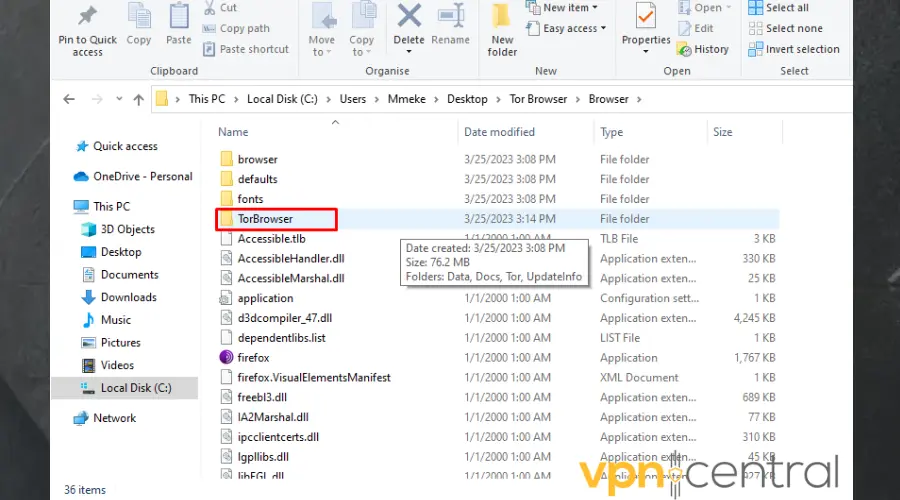
- Click on the data folder inside the TorBrowser folder.
- Then double-click on the Tor folder you find.
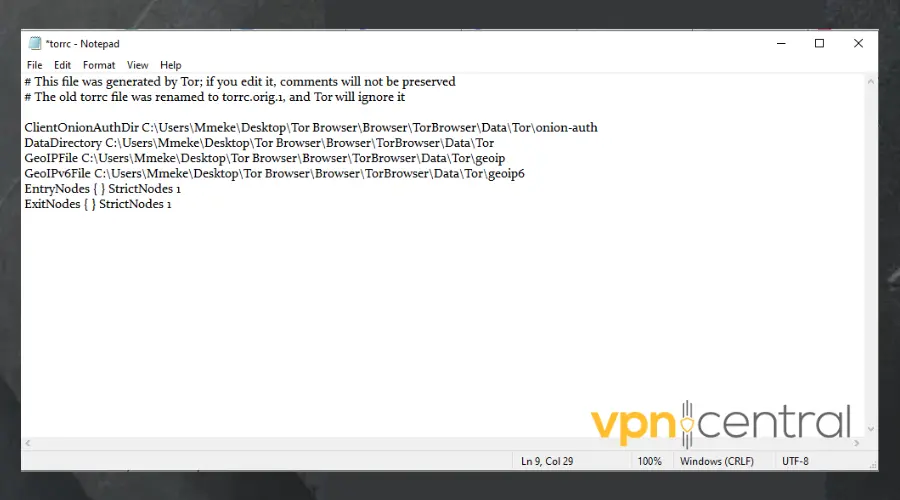
- Scroll down to the torcc file. This is a configuration file that you can make changes to.
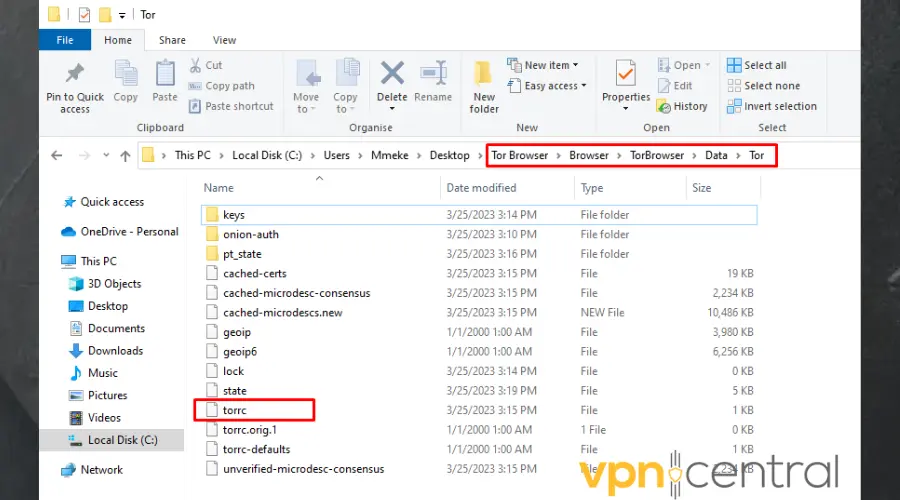
- Click on the file to open it. Ensure to select a text editor like Notepad. Then click Ok.
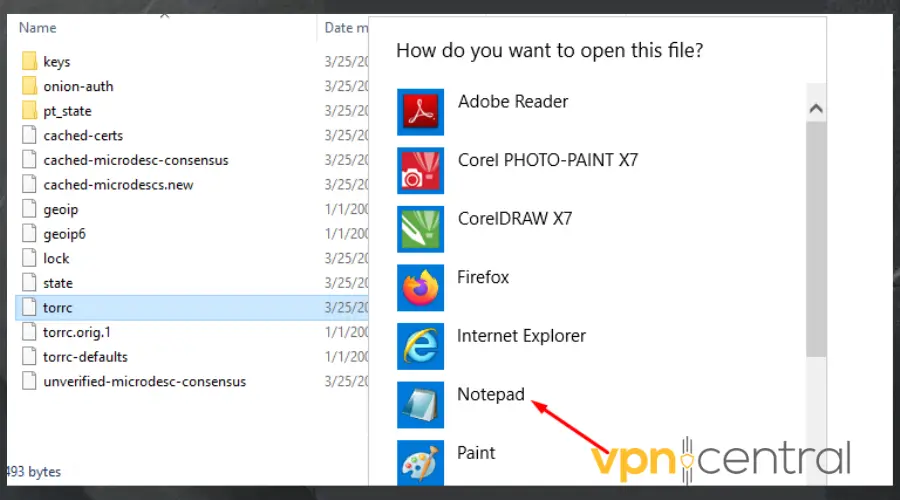
- Place your cursor below the last line of the text in the document, then type in EntryNodes { } StrictNodes 1 and press Enter to go to the next line.
- Type ExitNodes { } StrictNodes 1 in the current line.
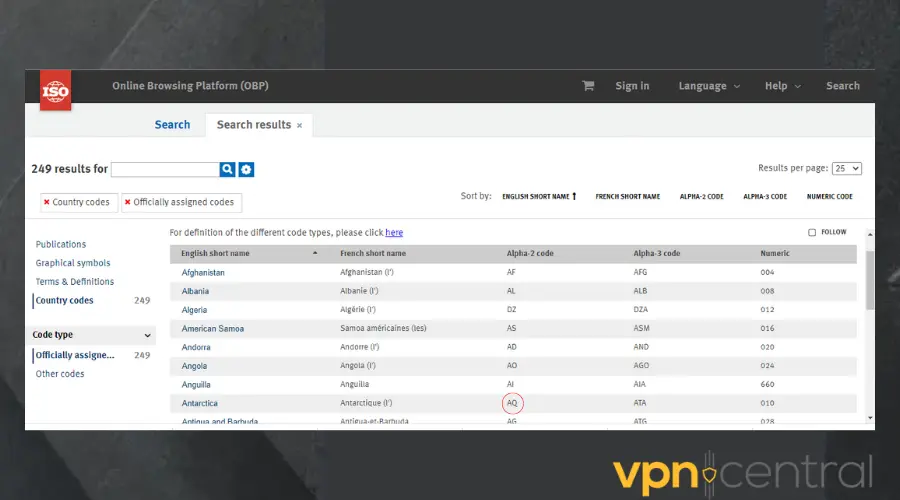
- Visit the Online Browsing Platform website and pick the 2-digit codes for the two countries of your choice.
- Enter those codes individually inside your entry and exit codes.
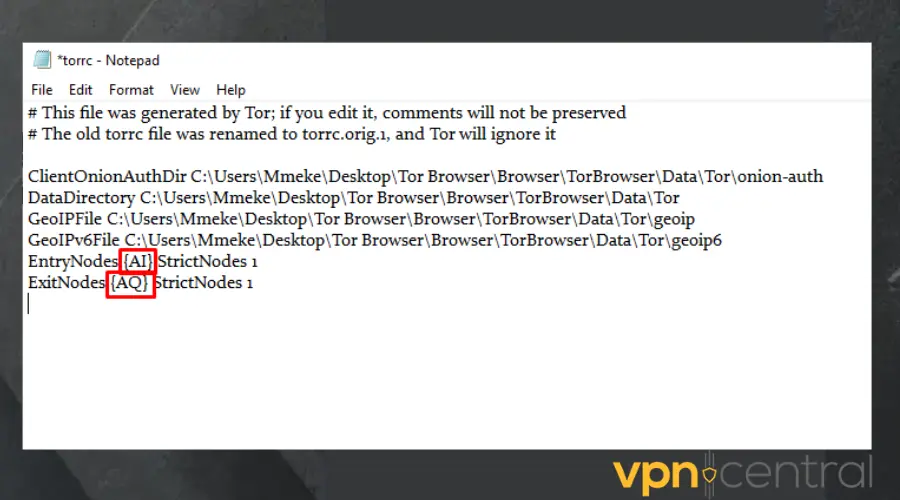
- Disable the entry and exit nodes by replacing the 1 with 0 if you want the Tor browser to use other countries if the connection fails.
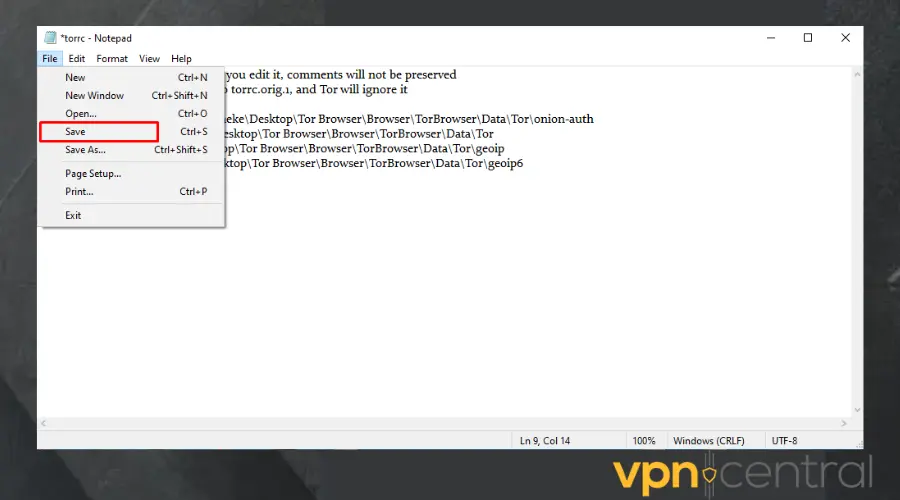
- Click on File, and select Save to update the changes. Exit the document.
- Go back to the website where your IP was grabbed and try to gain access again.
3. Enable your firewall
A Firewall’s primary purpose is to block unauthorized access to or from the internet to your device. It can serve as a means to protect valuable information, including your IP address.
- Select Start, then open Settings.
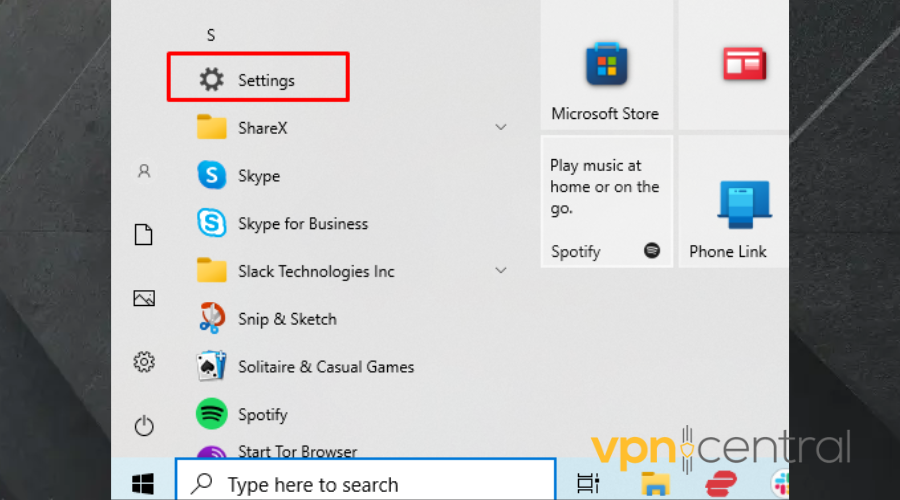
- Click on Update and Security.
- Choose select Windows Security > Firewall & network protection.
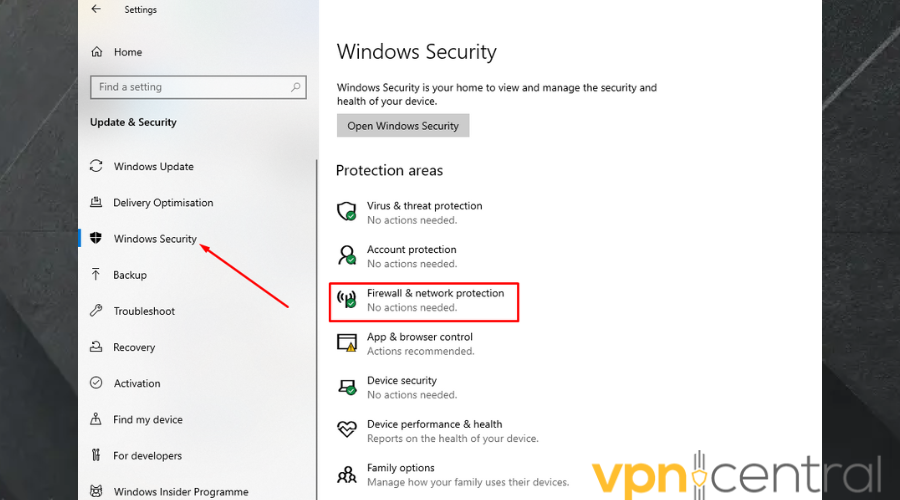
- Select a network profile: Domain network, Private network, or Public network.
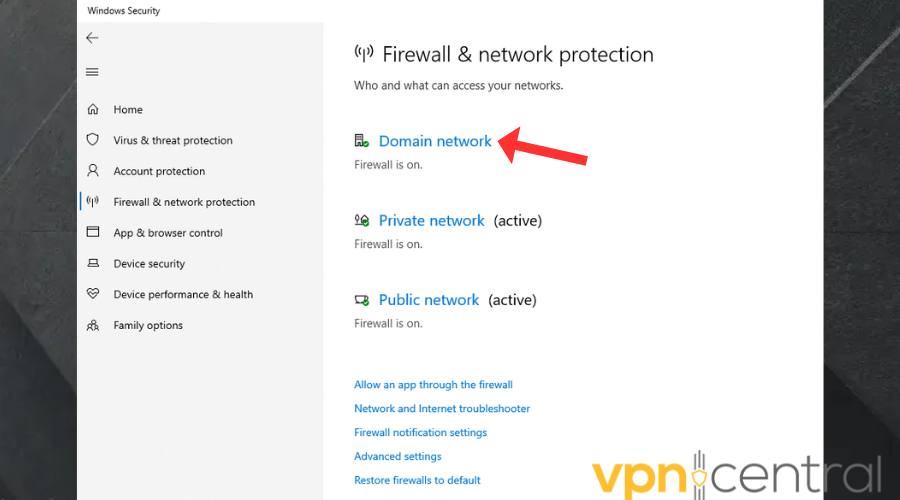
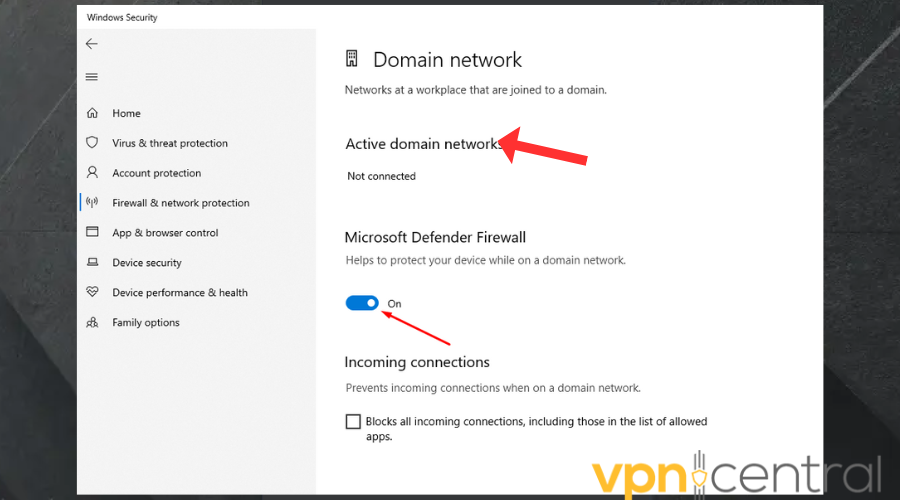
- Under Microsoft Defender Firewall, toggle the switch to ON.
Read more:
- Your Access to This Site Has Been Limited By the Site Owner [Fix]
- FIX: Your IP Has Been Flagged for Potential Security Violations
Summary
Cybercriminals use methods like phishing to grab IP addresses especially to track users’ locations. To know your IP address has been grabbed, check out for unusual activity in your network.
Thankfully, by updating your Firewall settings, and using a VPN or Tor browser, you can resolve this issue before it gets out of hand.
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more



User forum
1 messages