5 VPNs with Obfuscated Servers that Work Great on MacOS
8 min. read
Updated on
Read our disclosure page to find out how can you help VPNCentral sustain the editorial team Read more

If you’re a macOS user concerned about online privacy and security, you may be wondering if there are VPNs with obfuscated servers available for your device.
Well, we got good news. There are a lot of providers that offer this feature. However, not all of them work perfectly.

Access content across the globe at the highest speed rate.
70% of our readers choose Private Internet Access
70% of our readers choose ExpressVPN

Browse the web from multiple devices with industry-standard security protocols.

Faster dedicated servers for specific actions (currently at summer discounts)
To save you some time, we checked out several VPNs that claim to use obfuscation and listed below the best ones. Below are our top obfuscated VPNs for macOS.
Which are the best VPNs with obfuscated servers for macOS?
A VPN with the best obfuscated servers allows you to easily bypass firewalls that block VPNs and maintain privacy by hiding your online activity.
It should boast robust security features, blazing-fast speeds, and support simultaneous connections on multiple devices.
To help you make an informed decision, we’ve compiled a list of the best VPNs with obfuscated servers for macOS that offer superior privacy and security features.
1. NordVPN – advanced obfuscation technology
NordVPN is one of the leading VPN services that can effectively bypass internet restrictions, making it a top choice for macOS users.
While NordVPN doesn’t specify the obfuscation method used, it likely employs Obfsproxy or OpenVPN over SSL to bypass censorship and VPN detection techniques.
Furthermore, NordVPN has advanced features like MultiHop and Onion over VPN servers that provide extra layers of security to your internet connection.
MultiHop routes your traffic through multiple servers, while Onion over VPN adds a layer of encryption and anonymity by routing your traffic through the Tor network.
These features are effective even against the toughest censorship systems, such as the Great Firewall of China.
❗To access NordVPN’s obfuscated servers on macOS, you need to set your VPN protocol to OpenVPN TCP/UDP.
After setting your VPN protocol to OpenVPN TCP/UDP, go to the main page, pick Specialty Servers, and then select Obfuscated Servers.
Once connected to these special servers, you can browse the internet on your macOS device without worries.
Unique features of NordVPN:
- 5,400+ VPN servers in 59 countries for global coverage
- Custom DNS servers for enhanced privacy
- Compatible with Windows, macOS, Linux, Android, iOS, Chrome, Firefox, Opera
- Zero-logging policy for maximum security
- 30-day money-back guarantee (no free trial) for risk-free testing.

NordVPN
Bypass VPN firewalls and access any corner on the internet you want with NordVPN!2. ExpressVPN – built-in obfuscation on all servers
ExpressVPN offers obfuscation features to conceal your VPN traffic, making it an ideal choice for macOS users seeking enhanced online privacy.
One of the key features is the automatic obfuscation servers, which are built into all of ExpressVPN’s server locations.
❗ However, keep in mind that the obfuscation feature is always enabled. You can’t manually turn it on/off.
Because they hide VPN traffic, these servers effectively bypass restrictions and allow users to access the internet freely and securely, even in countries with limited internet freedom like China or Russia.
It’s also worth noting that obfuscated servers are available for use with all of ExpressVPN’s subscription plans and are located in different countries around the world.
ExpressVPN values security and offers AES 256-bit encryption, proprietary Lightway protocol, and a kill switch to protect users from data leaks in the event of a dropped VPN connection.
Additional features of ExpressVPN:
- Split tunneling
- DNS leak protection
- Unlimited bandwidth
- 24/7 customer support
- Compatibility with major platforms
- 3000+ servers in 90+ countries
- No-logs policy
- TrustedServer technology is a process that ensures all data on a server is erased after every reboot.

ExpressVPN
Say goodbye to internet barriers and embrace full browsing anonymity using ExpressVPN!3. Surfshark – two obfuscation modes
Surfshark, one of the top VPN services available, offers a range of powerful features that make it an excellent choice for macOS users who need to bypass VPN bans on apps like Netflix or Hulu.
As opposed to most VPNs, it offers two distinctive modes for obfuscation, which are Camouflage mode and NoBorders mode.
Camouflage mode removes all VPN-related data from your connection, making it look like a normal connection. This hides VPN traces and makes it difficult for networks to monitor your activity.
❗It is automatically activated when you connect to a server using the OpenVPN (UDP/TCP) protocol.
On the other hand, NoBorders mode allows you to use the Surfshark app in restrictive regions without issues. ❗It automatically turns on when needed and is also manually enabled in Settings.
This feature ensures seamless and secure browsing, even in countries with advanced online censorship systems.
Moreover, with Surfshark’s vast network of 3,200+ servers in over 100 countries you can overcome advanced censorship techniques and enjoy seamless and secure browsing.
Additionally features:
- Uses multiple VPN protocols (OpenVPN, IKEv2)
- Prioritizes privacy and security
- AES 256-bit encryption used
- Strict no-logs policy
- Data protection with a kill switch

Surfshark
Disguise your VPN traffic and browse the web freely with Surfshark VPN!4. Proton VPN – built-in stealth mode technologies
One of the standout features of Proton VPN’s obfuscated servers is that they come with a Secure Core option that routes your traffic through multiple servers before reaching its final destination
This means that even if your connection is compromised at one of the servers, your data remains encrypted and secure.
This VPN’s obfuscation feature is named Stealth mode. ❗You can easily enable/disable it from settings and only use it as needed.
With Stealth enabled, ProtonVPN connections are almost completely undetectable.
In addition, Proton VPN also offers alternative routing and VPN Accelerator technologies that provide faster and more secure connections.
The alternative routing technology allows it to bypass VPN blocks by rerouting connections over other hard-to-trace paths.
Meanwhile, the VPN Accelerator can potentially speed up connection by up to 400%, making it an ideal solution for users in regions with slower internet.
Proton VPN has over 2,591 servers in 64 countries, providing reliable access and worldwide coverage.
Additional features:
- High-speed servers (up to 10Gbps)
- No-logging policy
- Premium ad blocker (NetShield)
- Supports streaming services

Proton VPN
Use Proton VPN for untraceable and completely secure connections!5. IPVanish – secure obfuscated server options

IPVanish offers an effective solution to bypass VPN blocking tools through their OpenVPN obfuscation setting, known as the Scramble.
❗You can find the feature in settings and easily enable it in a few clicks.
By utilizing this feature, your online activities remain private, as it renders it nearly impossible for anyone to analyze your data.
It achieves this by modifying the metadata in your data packets, which makes it virtually impossible for VPN detection tools such as Wireshark to identify any VPN patterns in your traffic.
Additionally, VPN-blocking tools are unable to detect your VPN, allowing your traffic to freely flow through.
On top of that, with over 2,200 servers located across 75+ locations worldwide, IPVanish offers global access to their VPN service.
Added options:
- WireGuard, IKEv2, and L2TP protocols.
- Split tunneling for apps
- Strict no-logs policy
- Unlimited devices connection

IPVanish
Shield your VPN connection for secure and unrestricted browsing on any webpage or app!What are obfuscated servers and how do they work?
Obfuscated servers are VPN servers that use an extra layer of encryption to make traffic unidentifiable and prevent blocking.
They work by altering data to appear less suspicious to detection systems implemented by countries like Russia and China and websites that block VPN access.
VPN providers have multiple methods to obfuscate their servers, they can also scramble packet metadata or use additional SSL/SSH encryption to disguise traffic as regular HTTPS traffic.
This makes it harder for detection systems to identify and block VPN traffic.
How to enable obfuscated servers?
You can enable the feature in your macOS device by selecting the obfuscated server option in the settings menu.
Once enabled, the VPN connection is routed through an obfuscated server to mask the VPN traffic.
The following are steps to connect to obfuscated servers using NordVPN in macOS:
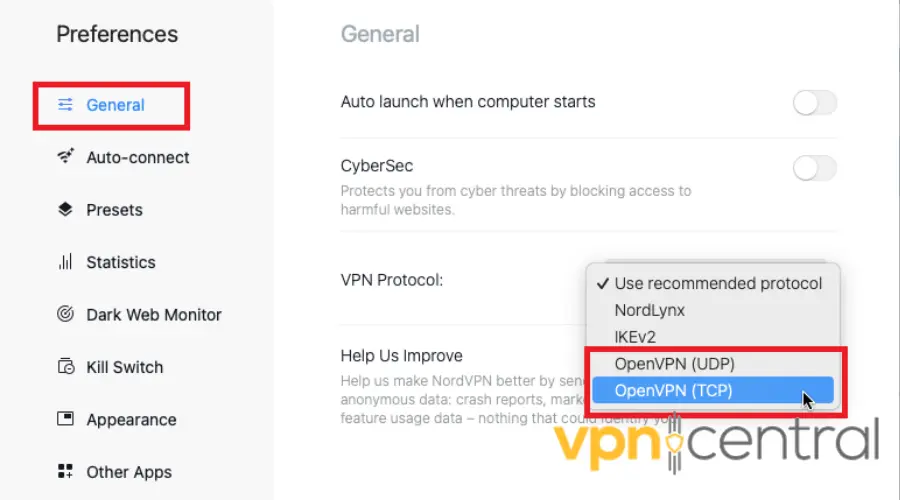
- Open your VPN app and click the Settings menu in the lower left corner.
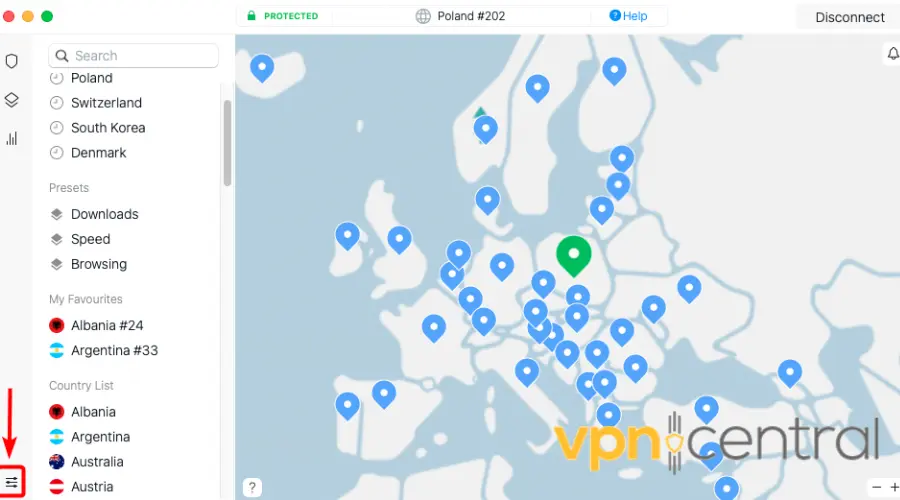
- Navigate to General.
- Select the OpenVPN (UDP) or OpenVPN (TCP) option in the VPN Protocol menu.
- Enable Obfuscated Servers once you locate the it under the Specialty Servers section
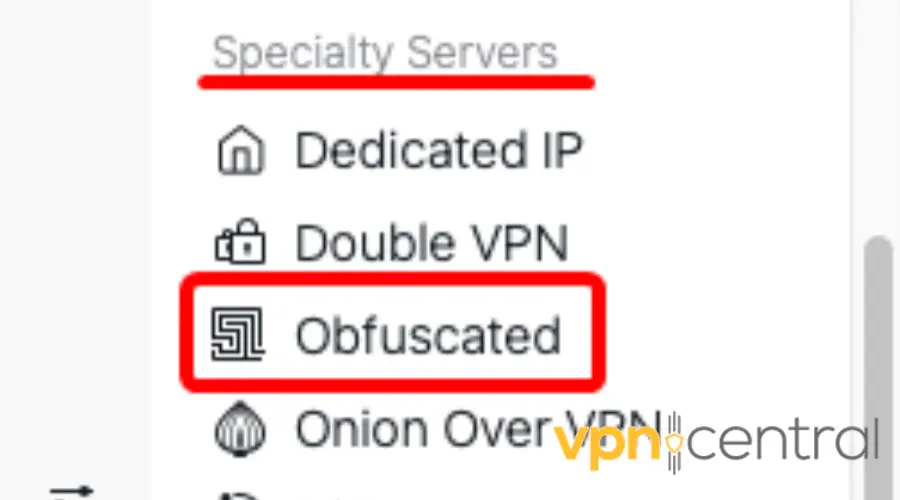
Following these simple steps, you can now connect to obfuscated servers on NordVPN and stay hidden from VPN-blocking technologies.
Wrap up
Obfuscated servers are essential for bypassing internet censorship in restrictive countries and accessing geo-restricted content, including streaming services like Netflix.
They also provide privacy protection and access to restricted apps and websites. When choosing a VPN for macOS, look for one with obfuscated servers.
The VPNs mentioned in this article offer secure, anonymous browsing and work in highly restricted countries.









User forum
0 messages